EDIT: this post is a work in progres and it might be changed at a later date.
EDIT 2: the tutorial is in post 9. This documents is a confused mess of notes (some of them are also incorrect) that I wrote down as a basis for the tutorial.
I am having a back and forth discussion with @jon concerning the wiki documentation of OpenVPN for phones, I thought it would be more useful to discuss it with the entire community.
My problem is that the documentation as it is today is barely helpful for someone who understands a bit of system administration and I would argue even negatively helpful (as in just confusing) for a newbie. The reason for this is: obsolescence, as there are several moving part that have evolved over time, including OpenVPN server, OpenVPN connect (the official client for both platforms), iOS and android (the OSes).
I will describe below my understanding of the situation today, and propose several changes on the wiki to create a more helpful documentation.
Premise
OpenVPN connect needs 5 pieces of information to successfully establish a road warrior tunnel with OpenVPN server:
- the
.ovpnconfiguration file; - the client certificate;
- the private key;
- the Certificate Authority (CA);
- the HMAC authentication key (tls-auth).
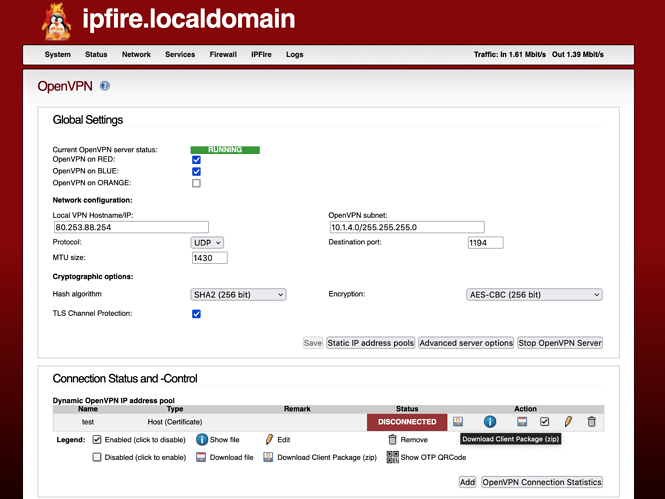
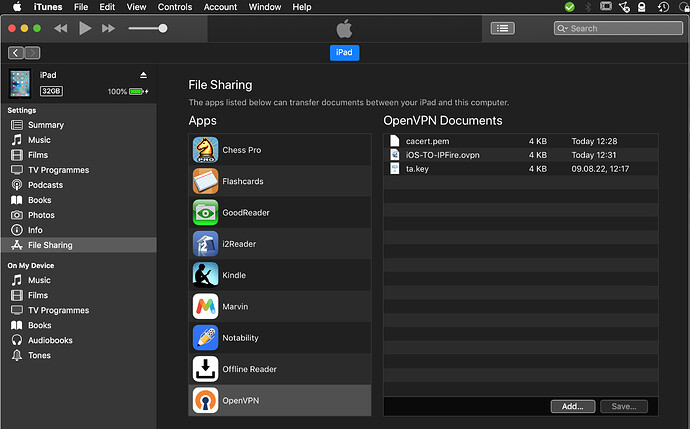
These 5 pieces of information are provided in 2 possible forms by the CGI code behind the WUI.
If during the roadwarrior configuration the PKCS12 File Password field is set to a string of characters then the code creates the following
-
a downloadable zip file named
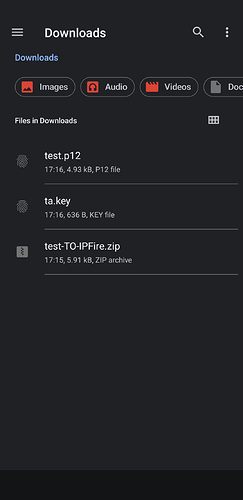
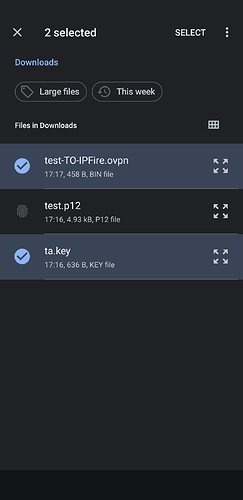
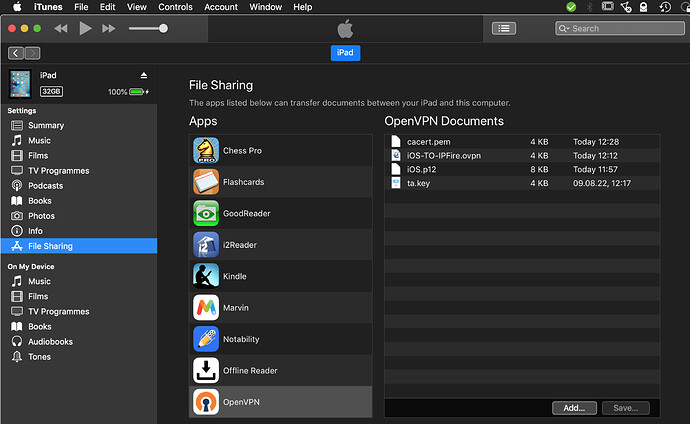
client package, composed by 3 files:-
name-TO-IPFIRE.ovpn, contenting the configuration file, the first piece of information needed, -
ta.key, containing the fifth piece of info, the HMAC authentication key -
name.p12, containing the remaining information (client, private key and CA);
-
instead if PKCS12 File Password is LEFT EMPTY, there will be two zip files created, the same 1) as above and
-
a second downloadable zip file named
insecure client packagecomposed by 5 files:-
name-TO-IPFIRE.ovpn, contenting the configuration file, first piece of information needed, but this time including also all the other pieces of information embedded inside in xml tags. This file is calledunified format -
ta.key, containing the fifth piece of info, the HMAC authentication key -
name.pemclient certificate in text format -
name.keycontaining the private key in text format -
cacert.pemcontaining the CA certificate in text format
-
The .ovpn file is different between the standard and unified format. In the standard, more secure, format it will point to the ta.key and the .p12 certificates files with the following syntax
pkcs12 name.p12
tls-auth ta.key
in the insecure package it will NOT have the above directives, but commented out lines pointing to each of all four individual certificate
;ca cacert.pem
;cert name.pem
;key name.key
;tls-auth ta.key
AND also all those certificates embedded in xml tags
<ca>
-----BEGIN CERTIFICATE-----
censored
-----END CERTIFICATE-----
</ca>
<cert>
Bag Attributes
friendlyName: name
localKeyID: censored
subject=C = censored, ST = censored, O = censored, CN = censored
issuer=C = censored, ST = censored, L = censored, O = censored, CN = censored CA, emailAddress = censored
-----BEGIN CERTIFICATE-----
censored
-----END CERTIFICATE-----
</cert>
<key>
Bag Attributes
friendlyName: name
localKeyID: censored
Key Attributes: <No Attributes>
-----BEGIN PRIVATE KEY-----
censored
-----END PRIVATE KEY-----
</key>
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
censored
-----END OpenVPN Static key V1-----
</tls-auth>
Android configuration
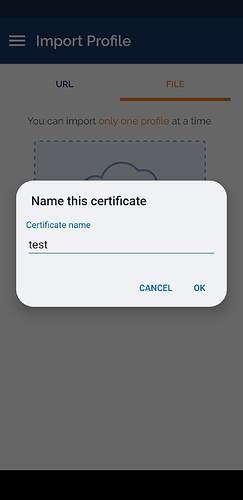
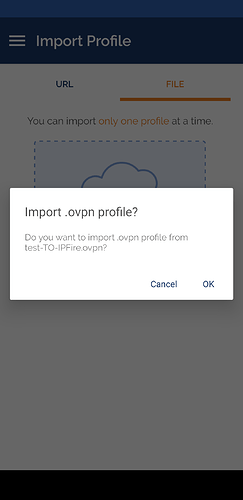
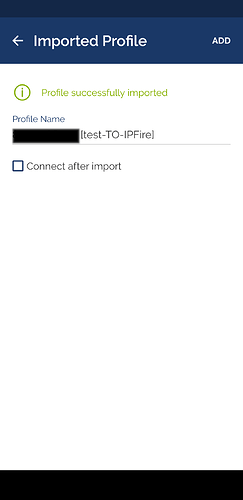
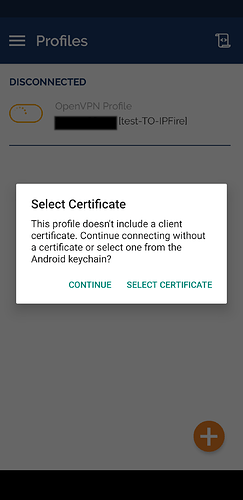
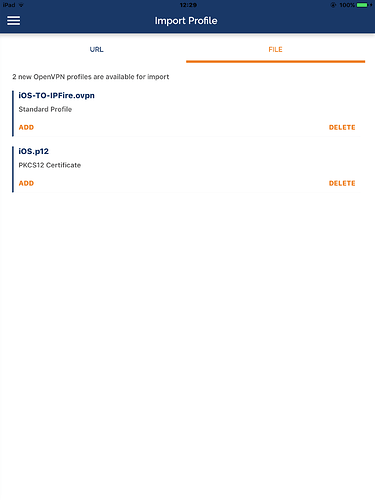
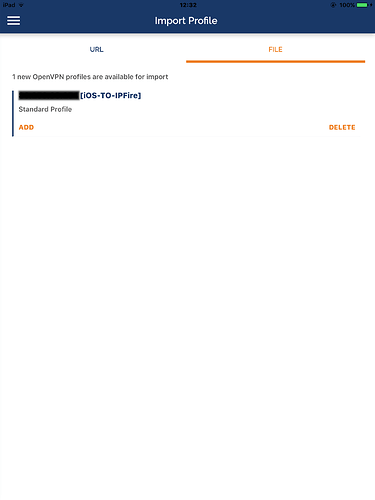
To configure OpenVPN connect on Android, you can import the .ovpn file from the insecure client package and it will work as it is and out of the box as it contains everything needed for the tunnel. Instead, if you use the client package there will be several problems to solve.
- in the
.ovpnfile, the directive
tls-auth ta.key
will trigger an error from OpenVPN connect even if you download ta.key in the same folder with the .ovpn file. Simply OpenVPN connect looks for this file in the wrong place and it will not import the configuration file, giving a file not found error.
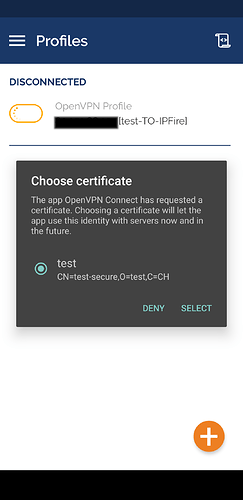
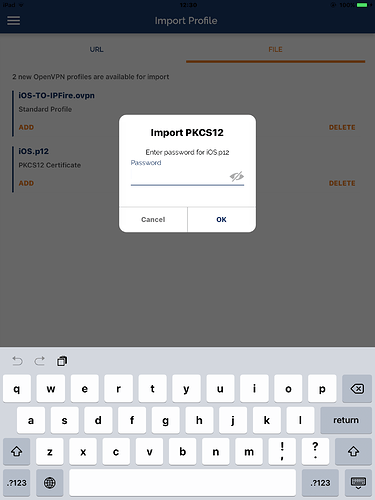
- you will need to import the
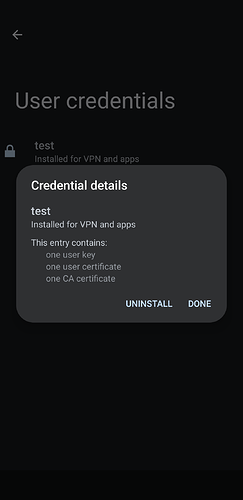
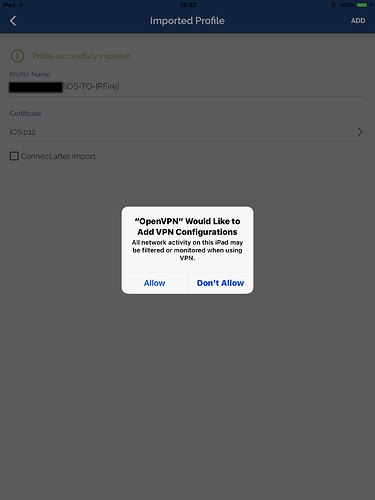
name.p12file with the client, private, and CA certificates. This can be done from insideOpenVPN connectwithout any issue. If you manage to import the configuration file, you will be ask to link it to all the certificates which will be available if you have imported them.
Why would you want to use the second option, even with the ta.key issue? Because this is way more secure, as all the certificates are handled by Android using the dedicated hardware of the phone to protect this crucial piece of information. With the insecure package, anyone having access to the .ovpn unified format file will have everything necessary to connect to the server.
How to fix the ta.key issue? Modify the .ovpn file to include the ta certificate in the embedded format:
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
censored
-----END OpenVPN Static key V1-----
</tls-auth>
with also the following directive:
key-direction bidirectional
AND comment out the directive tls-auth ta.key
;tls-auth ta.key
iOS configuration
All the information described in the previous section is valid also fo iOS, IN ADDITION TO another issue.
OpenVPN connect in iOS cannot get the CA certificate from the .p12 file.
By the way, to import the certificates in iOS name.p12 has to be renamed name.ovpn12 otherwise .iOS will not know that this file should be handled by OpenVPN connect.
How to tell .OpenVPN connect where to find the CA certificate? As in the TA certificate, it needs to be embedded in the .ovpn file.
First, to extract it from the .p12 file you need to have access to openssl and use the following command:
openssl pkcs12 -in name.ovpnp12 -cacerts -nokeys -out ca.crt
Then, you can copy and paste it like this:
<ca>
-----BEGIN CERTIFICATE-----
censored
-----END CERTIFICATE-----
</ca>
The rest, works exactly as in the Android configuration.
Summary
This post, including corrections from the community, should be distilled in an unified howto for mobile machines, with all the steps documented with images. Also, from the current wiki text, the part describing how to deliver all the files containing the 5 pieces of information to OpenVPN connect should be maintained as it is still relevant and well explained. The rest should be moved to a separate page that specify how the information is obsolete and left available only for historical reasons.