Hi,
I need some help with using the config option print_trigger_exec. The trigger should call a Python script to insert the content of the generated CSV-file to a database (InfluxDB).
Here is my configuration file, parts of it:
syslog: daemon
promisc: true
interface: green0
plugins: print[green_full]
print_output_file[green_full]: /root/metrics/traffic_green_full.csv
print_output[green_full]: csv
print_history[green_full]: 1m
print_history_roundoff[green_full]: m
#Execute plugin cache scanner each 60s
print_refresh_time[green_full]: 60
#Execute trigger to insert data into InfluxDB # Command cd is important otherwise Python script throws invisible errors about metrics.conf
print_trigger_exec[green_full]: /usr/bin/python3 /root/metrics/traffic.py -f /root/metrics/traffic_green_full.csv -i green0 -m full
Problem is that this trigger or better the Python script gets not executed! Or at least I cannot see the result in the database. When using the command line that is given above, manually in the IPFire shell, the values are properly inserted into the database.
For debugging, I’ve replaced the above option with the following one and added a CD command to no avail either:
print_trigger_exec[green_full]: cd /root/metrics && /usr/bin/python3 /root/metrics/traffic.py -f /root/metrics/traffic_green_full.csv -i green0 -m full
Next step I tried, use a much more simpler shell-script, test.sh that uses arguments and pass it to a bash-script:
#!/bin/bash
cd /root/metrics/ && /usr/bin/python3 /root/metrics/traffic.py -f $1 -i $2 -m $3
and changed the command line within pmacct.conf
print_trigger_exec[green_full]: /root/metrics/test.sh /root/metrics/traffic_green_full.csv green0 full
Both changes did not work either.
Next step, I changed the content of my test.sh and replaced it with:
#!/bin/bash
echo “test” >> test.log
THIS now works as expected! So right now, I’m both confused and clueless.
Nevertheless while executing parts of the initial command
traffic.py -f /root/metrics/traffic_green_full.csv -i green0 -m full
I once got an error indicating that the logging functions I’ve used inside traffic.py cannot access the necessary logging configuration file: metrics.conf. This file is located in the same folder as the appropriate Python script itself and some other Python scripts can access them. Maybe it is a problem with the daemon pmacctd that runs with different credentials?
More info: I’ve got some more Python scripts within the same folder that are called by cron without any issues. Those scripts, too, use the same logging functiosn and configuration file w/o any problems.
Since no message gets logged neither in /var/log/messages nor elsewhere I could not figure out if this once raised errors still raises and is the cause for no data being inserted into my database.
Is there sthg. I could test?
Michael
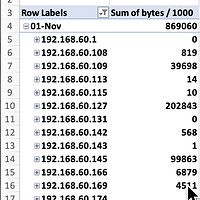
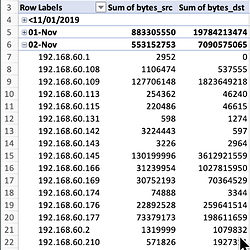
 is that I will have to start a different daemon with a different configuration file that monitors one of the other interfaces.
is that I will have to start a different daemon with a different configuration file that monitors one of the other interfaces.