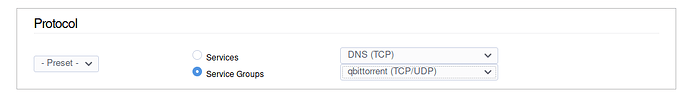
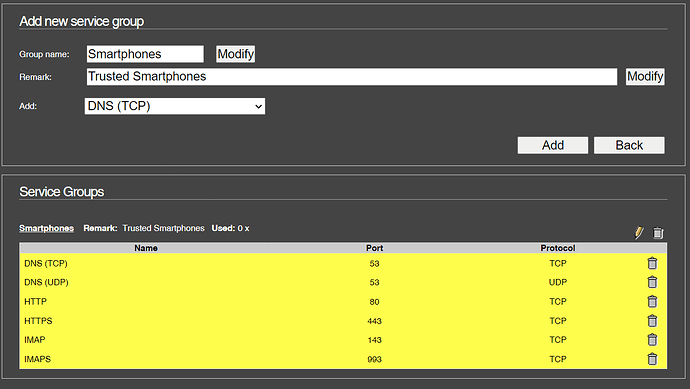
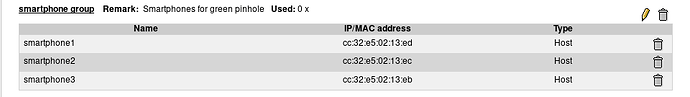
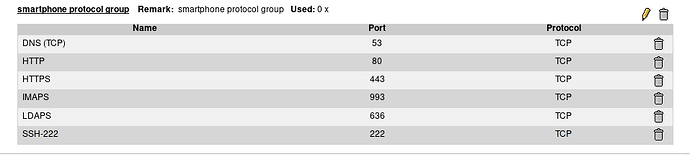
I recently upgraded my AP’s Firmware and while doing that I considered enabling the Guest mode for some devices. I did not proceed since I am concerned about CPU/RAM load on the AP and perhaps this should be done in IPFire instead, since that machine has plenty CPU/RAM.
The AP is connected to Green via Patch panel and Switch. I have no Blue configured, nor anything connected to a NIC that could adopt the Blue role.
It is not a Wifi NIC as stated here: wiki.ipfire.org - Wireless Access Point
I do not think hostapd is relevant for my scenario…
Looking through IPFire system I see no obvious way to enable any Wifi Guest functionality, which I guess is fine since I have no Blue configured.
What I believe I should do, from reading threads here and the wiki, is:
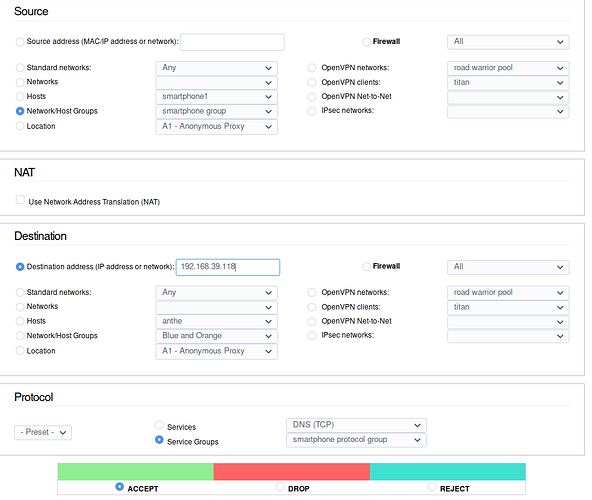
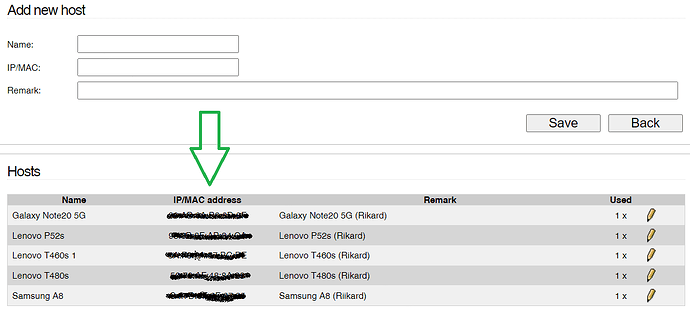
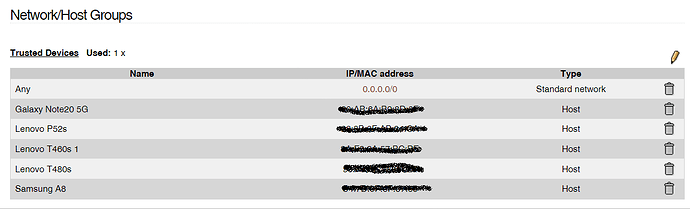
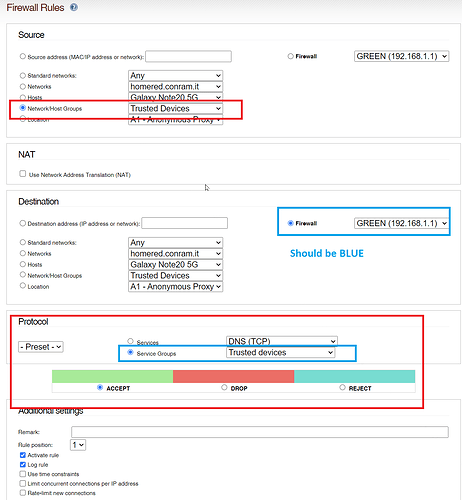
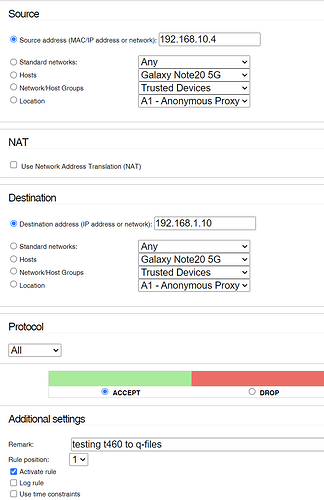
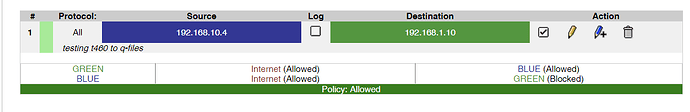
Connect the AP to a NIC on my IPFire computer and configure Blue to that NIC, which is perfectly possible. That raises additional questions.
- How do I then create a Guest network for untrusted Wifi connected devices? A vlan? On Blue? How?
- How do I configure Blue so trusted Wifi devices can access the rest of the trusted Lan network, that being 192.168.1.1/24?