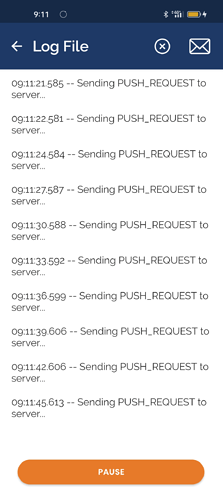
Hi Michael. Thanks for your reply.
This is my IPFire´s OpenVPN log:
IPFire diagnostics
Sección: openvpn
Fecha: Julio 13, 2022
09:47:18 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 SIGTERM[soft,remote-exit] received, client-instance exiting
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 PUSH: Received control message: 'PUSH_REQUEST'
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 SENT CONTROL [Realme]: 'PUSH_REPLY,route 10.81.40.1,topology net30,route 10.254.0.0 255.255.255.0,ifconfig 10.81.50.2 10.81.50.1,peer-id 0,cipher AES-128-GCM' (status=1)
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 MULTI: primary virtual IP for Realme/79.xxx.xxx.xxx:48941: 10.81.50.2
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 MULTI: Learn: 10.81.50.2 -> Realme/79.xxx.xxx.xxx:48941
09:47:13 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 OPTIONS IMPORT: reading client specific options from: /tmp/openvpn_cc_45a0f2358073da343d8b696df3cd77f1.tmp
09:47:12 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 OPTIONS IMPORT: reading client specific options from: /var/ipfire/ovpn/ccd/Realme
09:47:12 openvpnserver[28569]: Realme/79.xxx.xxx.xxx:48941 MULTI_sva: pool returned IPv4=10.81.40.10, IPv6=(Not enabled)
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 [Realme] Peer Connection Initiated with [AF_INET]79.xxx.xxx.xxx:48941
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
09:47:12 openvpnserver[28569]: MANAGEMENT: CMD 'client-auth-nt 0 0'
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1449', remote='link-mtu 1421'
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 TLS: Username/Password authentication deferred for username ''
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_SSO=webauth,openurl
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.7-7957
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_AUTO_SESS=1
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_PROTO=30
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_TCPNL=1
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_NCP=2
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_PLAT=android
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 peer info: IV_VER=3.git::d3f8b18b:Release
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Informatica, CN=Realme
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 VERIFY SCRIPT OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Informatica, CN=Realme
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 VERIFY OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
09:47:12 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 VERIFY SCRIPT OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
09:47:11 openvpnserver[28569]: 79.xxx.xxx.xxx:48941 TLS: Initial packet from [AF_INET]79.xxx.xxx.xxx:48941, sid=702e98d8 f6e026a9
09:46:43 openvpnserver[28569]: MANAGEMENT: Client connected from /var/run/openvpn.sock
09:46:42 openvpnserver[28569]: Initialization Sequence Completed
09:46:42 openvpnserver[28569]: Laptop,10.81.40.4,
09:46:42 openvpnserver[28569]: IFCONFIG POOL LIST
09:46:42 openvpnserver[28569]: succeeded -> ifconfig_pool_set(hand=0)
09:46:42 openvpnserver[28569]: ifconfig_pool_read(), in='Laptop,10.81.40.4,'
09:46:42 openvpnserver[28569]: IFCONFIG POOL IPv4: base=10.81.40.4 size=62
09:46:42 openvpnserver[28569]: MULTI: multi_init called, r=256 v=256
09:46:42 openvpnserver[28569]: UID set to nobody
09:46:42 openvpnserver[28569]: GID set to nobody
09:46:42 openvpnserver[28569]: UDPv4 link remote: [AF_UNSPEC]
09:46:42 openvpnserver[28569]: UDPv4 link local (bound): [AF_INET][undef]:1194
09:46:42 openvpnserver[28569]: Socket Buffers: R=[212992->212992] S=[212992->212992]
09:46:42 openvpnserver[28569]: Could not determine IPv4/IPv6 protocol. Using AF_INET
09:46:42 openvpnserver[28569]: /sbin/ip route add 10.81.40.0/24 via 10.81.40.2
09:46:42 openvpnserver[28569]: /sbin/ip route add 10.81.50.0/24 via 10.81.40.2
09:46:42 openvpnserver[28569]: /sbin/ip addr add dev tun0 local 10.81.40.1 peer 10.81.40.2
09:46:42 openvpnserver[28569]: /sbin/ip link set dev tun0 up
09:46:42 openvpnserver[28569]: /sbin/ip link set dev tun0 up mtu 1400
09:46:42 openvpnserver[28569]: TUN/TAP device tun0 opened
09:46:42 openvpnserver[28569]: ROUTE_GATEWAY 192.168.0.1/255.255.255.0 IFACE=red0 HWADDR=c2:11:ca:57:c9:00
09:46:42 openvpnserver[28569]: CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
09:46:42 openvpnserver[28569]: Diffie-Hellman initialized with 2048 bit key
09:46:42 openvpnserver[28569]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
09:46:42 openvpnserver[28569]: NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet.
09:46:42 openvpnserver[28569]: WARNING: --keepalive option is missing from server config
09:46:42 openvpnserver[28569]: MANAGEMENT: unix domain socket listening on /var/run/openvpn.sock
09:46:42 openvpnserver[28568]: library versions: OpenSSL 1.1.1p 21 Jun 2022, LZO 2.10
09:46:42 openvpnserver[28568]: OpenVPN 2.5.6 aarch64-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Jul 7 2022
09:46:42 openvpnserver[28568]: WARNING: --topology net30 support for server configs with IPv4 pools will be removed in a future release. Please migrate to --topology subnet as soon as possible.
09:46:42 openvpnserver[28568]: DEPRECATED OPTION: ncp-disable. Disabling cipher negotiation is a deprecated debug feature that will be removed in OpenVPN 2.6
09:46:37 openvpnserver[20455]: SIGTERM[hard,] received, process exiting
09:46:37 openvpnserver[20455]: Linux ip addr del failed: external program exited with error status: 2
09:46:37 openvpnserver[20455]: /sbin/ip addr del dev tun0 local 10.81.40.1 peer 10.81.40.2
09:46:37 openvpnserver[20455]: Closing TUN/TAP interface
09:46:37 openvpnserver[20455]: ERROR: Linux route delete command failed: external program exited with error status: 2
09:46:37 openvpnserver[20455]: /sbin/ip route del 10.81.40.0/24
09:46:37 openvpnserver[20455]: ERROR: Linux route delete command failed: external program exited with error status: 2
09:46:37 openvpnserver[20455]: /sbin/ip route del 10.81.50.0/24
09:46:37 openvpnserver[20455]: event_wait : Interrupted system call (code=4)
09:18:00 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 SIGTERM[soft,remote-exit] received, client-instance exiting
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 PUSH: Received control message: 'PUSH_REQUEST'
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 SENT CONTROL [Realme]: 'PUSH_REPLY,route 10.81.40.1,topology net30,route 10.254.0.0 255.255.255.0,ifconfig 10.81.50.2 10.81.50.1,peer-id 0,cipher AES-128-GCM' (status=1)
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 MULTI: primary virtual IP for Realme/79.xxx.xxx.xxx:47210: 10.81.50.2
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 MULTI: Learn: 10.81.50.2 -> Realme/79.xxx.xxx.xxx:47210
09:17:54 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 OPTIONS IMPORT: reading client specific options from: /tmp/openvpn_cc_195edd733a22dc473327730c264259b6.tmp
09:17:53 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 OPTIONS IMPORT: reading client specific options from: /var/ipfire/ovpn/ccd/Realme
09:17:53 openvpnserver[20455]: Realme/79.xxx.xxx.xxx:47210 MULTI_sva: pool returned IPv4=10.81.40.10, IPv6=(Not enabled)
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 [Realme] Peer Connection Initiated with [AF_INET]79.xxx.xxx.xxx:47210
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
09:17:53 openvpnserver[20455]: MANAGEMENT: CMD 'client-auth-nt 1 0'
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1449', remote='link-mtu 1421'
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 TLS: Username/Password authentication deferred for username ''
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_SSO=webauth,openurl
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.7-7957
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_AUTO_SESS=1
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_PROTO=30
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_TCPNL=1
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_NCP=2
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_PLAT=android
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 peer info: IV_VER=3.git::d3f8b18b:Release
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Informatica, CN=Realme
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 VERIFY SCRIPT OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Informatica, CN=Realme
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 VERIFY OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
09:17:53 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 VERIFY SCRIPT OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
09:17:52 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
09:17:52 openvpnserver[20455]: 79.xxx.xxx.xxx:47210 TLS: Initial packet from [AF_INET]79.xxx.xxx.xxx:47210, sid=63af78d7 7e279c3c
09:12:27 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 SIGTERM[soft,auth-control-exit] received, client-instance exiting
09:11:57 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 PUSH: Received control message: 'PUSH_REQUEST'
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 PUSH: Received control message: 'PUSH_REQUEST'
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 [Realme] Peer Connection Initiated with [AF_INET]79.xxx.xxx.xxx:40983
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1449', remote='link-mtu 1421'
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 TLS: Username/Password authentication deferred for username ''
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_SSO=webauth,openurl
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.7-7957
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_AUTO_SESS=1
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_PROTO=30
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_TCPNL=1
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_NCP=2
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_PLAT=android
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 peer info: IV_VER=3.git::d3f8b18b:Release
09:11:21 openvpnserver[20455]: 79.xxx.xxx.xxx:40983 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=Informatica, CN=Realme
...
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1449', remote='link-mtu 1421'
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 TLS: Username/Password authentication deferred for username ''
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_SSO=webauth,openurl
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.7-7957
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_AUTO_SESS=1
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_PROTO=30
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_TCPNL=1
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_NCP=2
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_PLAT=android
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 peer info: IV_VER=3.git::d3f8b18b:Release
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=North Secure, CN=Realme
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 VERIFY SCRIPT OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=North Secure, CN=Realme
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 VERIFY OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
07:50:43 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 VERIFY SCRIPT OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
07:50:42 openvpnserver[5113]: 79.xxx.xxx.xxx:47279 TLS: Initial packet from [AF_INET]79.xxx.xxx.xxx:47279, sid=6b88edd4 b7a7d3b0
07:50:34 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:16 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:13 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:10 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:07 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:04 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:50:01 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:49:58 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:49:55 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 PUSH: Received control message: 'PUSH_REQUEST'
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 [Realme] Peer Connection Initiated with [AF_INET]79.xxx.xxx.xxx:49381
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1449', remote='link-mtu 1421'
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 TLS: Username/Password authentication deferred for username ''
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_SSO=webauth,openurl
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_GUI_VER=net.openvpn.connect.android_3.2.7-7957
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_AUTO_SESS=1
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_PROTO=30
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_TCPNL=1
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_NCP=2
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_PLAT=android
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 peer info: IV_VER=3.git::d3f8b18b:Release
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 VERIFY OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=North Secure, CN=Realme
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 VERIFY SCRIPT OK: depth=0, C=ES, ST=Bizkaia, O=North Secure, OU=North Secure, CN=Realme
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 VERIFY OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
07:49:49 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 VERIFY SCRIPT OK: depth=1, C=ES, ST=Bizkaia, L=Derio, O=North Secure, OU=North Secure, CN=North Secure CA, emailAddress=contacto@northsecure.es
07:49:48 openvpnserver[5113]: 79.xxx.xxx.xxx:49381 TLS: Initial packet from [AF_INET]79.xxx.xxx.xxx:49381, sid=68339d70 9dbd4a25
I put everything since I don’t know what to look for and surely at a glance you will see something.
Maybe the problem is that I’m very clumsy 
Thank you very much.