Hi there.
I have the task of upgrading the firewall server for my university computing lab. I am replacing the ancient Core 2 Quad machine running IPCop with a Core i7 7th gen machine with IPFire.
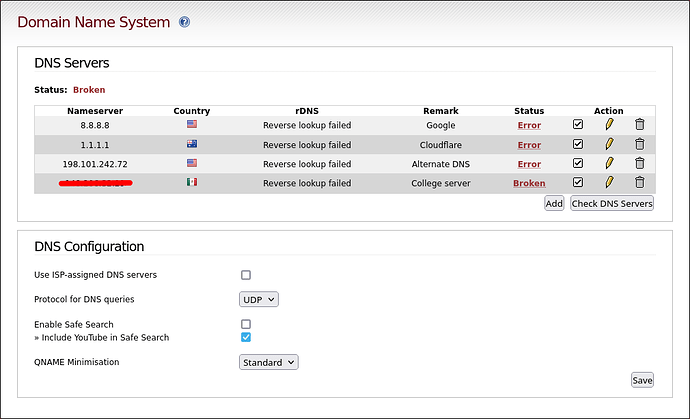
My problem is that I cannot setup the DNS servers no matter what. I’m trying to discard a port blockade from the uni sysadmin department (because dealing with them is a pain)
The connection to the outside is provided as a RJ45 port in the wall going netadmins know where, so I cannot give details about anything beyond that. I have an assigned IP aswell as our own DNS server IP, so RED is configured with static IP (no DHCP or dialup)
I have tried both the DNS our college has as pretty much evey single DNS server found at the wiki. each in UDP, TLS (ensuring to put the TLS hostname in each entry) and TCP. Even I tried reinstalling IPFire several times and doing that as the first ever config in order to avoid a wanky rule I may had setup badly.
Nothing.
I always get “reverse lookup failed” and an error status (but our DNS says “broken” for some reason).
Here is my config:
and the logs of unbound:
Nov 11 17:28:21 firewall unbound: [1659:0] info: service stopped (unbound 1.16.3).
Nov 11 17:28:21 firewall unbound: [1659:0] info: server stats for thread 0: 108 queries, 0 answers from cache, 108 recursions, 0 prefetch, 0 rejected by ip ratelimiting
Nov 11 17:28:21 firewall unbound: [1659:0] info: server stats for thread 0: requestlist max 18 avg 15.1111 exceeded 0 jostled 0
Nov 11 17:28:21 firewall unbound: [1659:0] notice: Restart of unbound 1.16.3.
Nov 11 17:28:21 firewall unbound: [1659:0] notice: init module 0: validator
Nov 11 17:28:21 firewall unbound: [1659:0] notice: init module 1: iterator
Nov 11 17:28:21 firewall unbound: [1659:0] info: start of service (unbound 1.16.3).
Nov 11 17:28:21 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:21 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:21 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:21 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:21 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:21 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:37 firewall unbound: [1659:0] error: read (in tcp s): Connection timed out for 1.1.1.1 port 53
Nov 11 17:28:37 firewall unbound: [1659:0] error: read (in tcp s): Connection timed out for 198.101.242.72 port 53
Nov 11 17:28:52 firewall unbound: [1659:0] error: read (in tcp s): Connection timed out for 1.1.1.1 port 53
Nov 11 17:28:52 firewall unbound: [1659:0] error: read (in tcp s): Connection timed out for 198.101.242.72 port 53
Nov 11 17:28:52 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <ping.ipfire.org. A IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org.labT169. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org. A IN>: key for validation . is marked as invalid
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <. DNSKEY IN>: no signatures from 148.206.32.29 for trust anchor . while building chain of trust
Nov 11 17:28:52 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. A IN>: key for validation . is marked as invalid
Nov 11 17:29:27 firewall unbound: [1659:0] info: service stopped (unbound 1.16.3).
Nov 11 17:29:27 firewall unbound: [1659:0] info: server stats for thread 0: 67 queries, 50 answers from cache, 17 recursions, 0 prefetch, 0 rejected by ip ratelimiting
Nov 11 17:29:27 firewall unbound: [1659:0] info: server stats for thread 0: requestlist max 12 avg 7.64706 exceeded 0 jostled 0
Nov 11 17:29:27 firewall unbound: [1659:0] info: average recursion processing time 15.579281 sec
Nov 11 17:29:27 firewall unbound: [1659:0] info: histogram of recursion processing times
Nov 11 17:29:27 firewall unbound: [1659:0] info: [25%]=6.5 median[50%]=16.8889 [75%]=24.4444
Nov 11 17:29:27 firewall unbound: [1659:0] info: lower(secs) upper(secs) recursions
Nov 11 17:29:27 firewall unbound: [1659:0] info: 0.524288 1.000000 1
Nov 11 17:29:27 firewall unbound: [1659:0] info: 1.000000 2.000000 2
Nov 11 17:29:27 firewall unbound: [1659:0] info: 4.000000 8.000000 2
Nov 11 17:29:27 firewall unbound: [1659:0] info: 8.000000 16.000000 3
Nov 11 17:29:27 firewall unbound: [1659:0] info: 16.000000 32.000000 9
Nov 11 17:29:27 firewall unbound: [1659:0] notice: Restart of unbound 1.16.3.
Nov 11 17:29:27 firewall unbound: [1659:0] notice: init module 0: validator
Nov 11 17:29:27 firewall unbound: [1659:0] notice: init module 1: iterator
Nov 11 17:29:27 firewall unbound: [1659:0] info: start of service (unbound 1.16.3).
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <. DNSKEY IN>: all the configured stub or forward servers failed, at zone . from 8.8.8.8 upstream server timeout
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <ping.ipfire.org. A IN>: all the configured stub or forward servers failed, at zone . from 1.1.1.1 upstream server timeout
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . from 1.1.1.1 upstream server timeout
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:28 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:44 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:44 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:44 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:44 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:52 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:52 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:52 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:29:52 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:00 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:16 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:16 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:16 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:16 firewall unbound: [1659:0] error: SERVFAIL <0.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:24 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:24 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:24 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. A IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:24 firewall unbound: [1659:0] error: SERVFAIL <1.ipfire.pool.ntp.org.labT169. AAAA IN>: all the configured stub or forward servers failed, at zone . no server to query nameserver addresses not usable have no nameserver names
Nov 11 17:30:41 firewall unbound: [1659:0] info: service stopped (unbound 1.16.3).
Nov 11 17:30:41 firewall unbound: [1659:0] info: server stats for thread 0: 58 queries, 29 answers from cache, 29 recursions, 0 prefetch, 0 rejected by ip ratelimiting
Nov 11 17:30:41 firewall unbound: [1659:0] info: server stats for thread 0: requestlist max 0 avg 0 exceeded 0 jostled 0
Nov 11 17:30:41 firewall unbound: [1659:0] info: average recursion processing time 0.029884 sec
Nov 11 17:30:41 firewall unbound: [1659:0] info: histogram of recursion processing times
Nov 11 17:30:41 firewall unbound: [1659:0] info: [25%]=2.68519e-07 median[50%]=5.37037e-07 [75%]=8.05556e-07
Nov 11 17:30:41 firewall unbound: [1659:0] info: lower(secs) upper(secs) recursions
Nov 11 17:30:41 firewall unbound: [1659:0] info: 0.000000 0.000001 27
Nov 11 17:30:41 firewall unbound: [1659:0] info: 0.262144 0.524288 1
Nov 11 17:30:41 firewall unbound: [1659:0] info: 0.524288 1.000000 1
Nov 11 17:30:41 firewall unbound: [1659:0] notice: Restart of unbound 1.16.3.
Nov 11 17:30:41 firewall unbound: [1659:0] notice: init module 0: validator
Nov 11 17:30:41 firewall unbound: [1659:0] notice: init module 1: iterator
Nov 11 17:30:41 firewall unbound: [1659:0] info: start of service (unbound 1.16.3).
Nov 11 17:30:41 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:30:41 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:30:41 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:30:41 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:30:41 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:30:41 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <www.google.com. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <ping.ipfire.org. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <pakfire.ipfire.org. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <pakfire.ipfire.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <pacifico.izt.uam.mx. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <8.8.8.8.in-addr.arpa. PTR IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org.labT169. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <1.ipfire.pool.ntp.org. A IN>: key for validation . is marked as invalid
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <. DNSKEY IN>: no signatures from 148.206.32.29 for trust anchor . while building chain of trust
Nov 11 17:51:06 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. A IN>: key for validation . is marked as invalid
Nov 11 17:52:04 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. A IN>: key for validation . is marked as invalid
Nov 11 17:52:04 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. A IN>: key for validation . is marked as invalid
Nov 11 17:52:04 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org.labT169. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:52:04 firewall unbound: [1659:0] info: validation failure <0.ipfire.pool.ntp.org. AAAA IN>: key for validation . is marked as invalid
Nov 11 17:52:10 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:52:10 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:52:10 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:52:10 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:52:10 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: service stopped (unbound 1.16.3).
Nov 11 17:57:44 firewall unbound: [1659:0] info: server stats for thread 0: 434 queries, 13 answers from cache, 421 recursions, 6 prefetch, 0 rejected by ip ratelimiting
Nov 11 17:57:44 firewall unbound: [1659:0] info: server stats for thread 0: requestlist max 17 avg 14.192 exceeded 0 jostled 0
Nov 11 17:57:44 firewall unbound: [1659:0] info: average recursion processing time 618.637512 sec
Nov 11 17:57:44 firewall unbound: [1659:0] info: histogram of recursion processing times
Nov 11 17:57:44 firewall unbound: [1659:0] info: [25%]=317.091 median[50%]=624.432 [75%]=910.703
Nov 11 17:57:44 firewall unbound: [1659:0] info: lower(secs) upper(secs) recursions
Nov 11 17:57:44 firewall unbound: [1659:0] info: 0.032768 0.065536 2
Nov 11 17:57:44 firewall unbound: [1659:0] info: 0.262144 0.524288 1
Nov 11 17:57:44 firewall unbound: [1659:0] info: 4.000000 8.000000 2
Nov 11 17:57:44 firewall unbound: [1659:0] info: 8.000000 16.000000 2
Nov 11 17:57:44 firewall unbound: [1659:0] info: 16.000000 32.000000 8
Nov 11 17:57:44 firewall unbound: [1659:0] info: 32.000000 64.000000 12
Nov 11 17:57:44 firewall unbound: [1659:0] info: 64.000000 128.000000 18
Nov 11 17:57:44 firewall unbound: [1659:0] info: 128.000000 256.000000 22
Nov 11 17:57:44 firewall unbound: [1659:0] info: 256.000000 512.000000 66
Nov 11 17:57:44 firewall unbound: [1659:0] info: 512.000000 1024.000000 148
Nov 11 17:57:44 firewall unbound: [1659:0] info: 1024.000000 2048.000000 50
Nov 11 17:57:44 firewall unbound: [1659:0] notice: Restart of unbound 1.16.3.
Nov 11 17:57:44 firewall unbound: [1659:0] notice: init module 0: validator
Nov 11 17:57:44 firewall unbound: [1659:0] notice: init module 1: iterator
Nov 11 17:57:44 firewall unbound: [1659:0] info: start of service (unbound 1.16.3).
Nov 11 17:57:44 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: failed to prime trust anchor -- DNSKEY rrset is not secure . DNSKEY IN
Nov 11 17:57:44 firewall unbound: [1659:0] info: generate keytag query _ta-4a5c-4f66. NULL IN
Thanks in advance, and hailings from Mexico.