Hello everyone,
Sorry for this wall of text, but a log or now special messages would be rather counterproductive here due to the total failure and thousands of error messages, so I’ll try to describe…how it came about and where I start why it came about…
I need tips on whether something can still be saved.
I can’t say exactly what the cause was or how it came about, nor what really happened, but my Ipfire has a permanent fault and I’m trying to provide all the relevant information here as to where I think the problem lies.
What happened?
I added another provider to the IPS, reloaded the log from time to time on the side, I noticed that the IP block lists were also increasingly blocking Tor addresses, which was otherwise not the case. I had already cleaned it up and removed the affected list, as I didn’t want to disrupt Tor operations.
Then it was suddenly no longer possible to reload the IPfire web interface or call up any website via the Squid in the browser.
Apart from that, the internet connection via Squid was stable. I’ve had this before, when the Squid got stuck, either it recovered or crashed completely, then you could access the ipfire web interface via the Squid proxy and just had to restart the Squid. But this time it was different, I could no longer establish a connection to the Ipfire. SSH was deactivated, no chance to start the SSH server to see what was going on on the console. I had no choice but to press the hardware button and then the problems really started.
First I tried everything after the reboot and realized that nothing was working, no web interface, my PC didn’t get its IP from the DHCP, something was wrong… so I went to the ipfire box, last chance to find out something… but when the monitor came on, the firewall log rattled relentlessly, it was not possible to make an entry, the text overwrote everything… I didn’t know anything like that…, so I rebooted and followed the boot process, an error in the file system was displayed, but it could be repaired and was now checked for the second time.
After starting the firewall, the text started again, but I recognized my external IP again, turned off the modem and had the opportunity to log in properly on the ipfire.
I started the setup and set up a native configuration, because I had a card with 2 VLANs assigned. So peace and quiet returned to the IPfire, then I reconfigured the switch because of the VLANs, restarted everything and I had my computer back on the network and access to the Ipfire web interface.
I still have a red error message when booting, the displayed file has something to do with ipset and firewall.local, because both processes are started or tried to be started there, but I’ll get to that in a moment. The path to this file was something like /etc/rc.d/6rc.d/98schlagmichtot.ja
But that was not all, I have restored the previous network configuration with the two VLANs, everything is running normally again, everything works as before, only the IPS can no longer be started, no matter which provider which network card I select. As soon as I press Save, a blank white page is loaded, the options are accepted, but the process is not started.
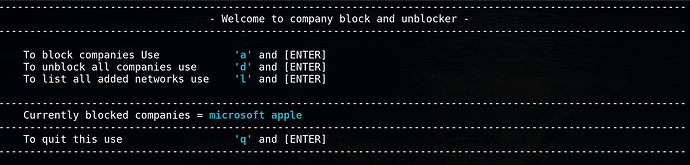
Now to my suspicions, a few weeks ago I found a script that creates ASN lists based on company names and creates the corresponding networks and enters them directly into the groups created for this purpose in the ipfire firewall group function. Everything is nicely organized, first the networks, then the respective groups, but unfortunately the script also wants to create the corresponding firewall rules, which probably doesn’t work, the script ends with an error message.
Thanks to the groups, however, the rules were created quite quickly and I thought that would be fine. Everything worked without me noticing anything special.
After a while, however, I noticed that after automatic script execution using the fcrontab entry, an error occurred that affected the system, but it took me a while to find the connection.
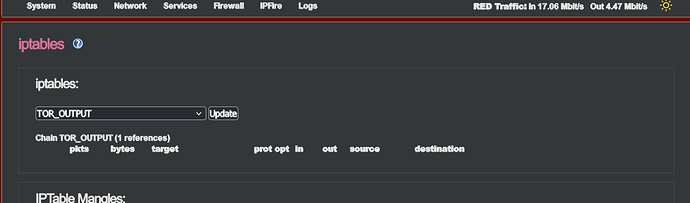
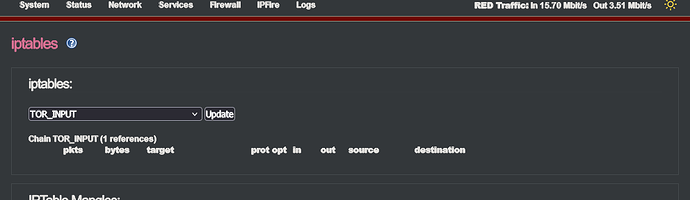
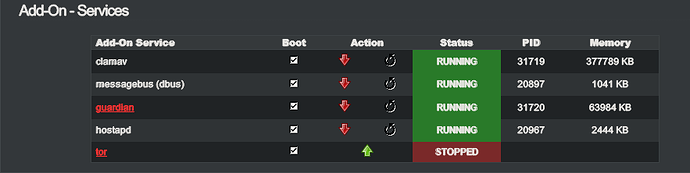
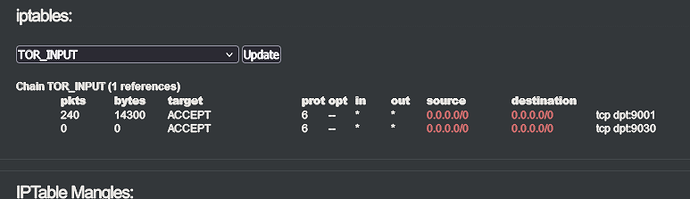
The iptables entries for my tor node were deleted, and I always wondered why the Tor process was running, but no connections to other nodes were established.
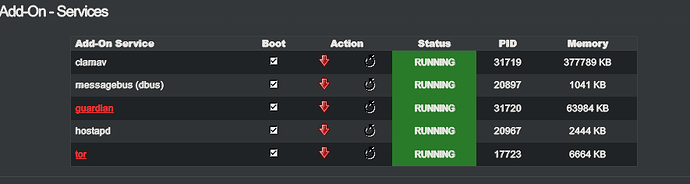
However, this could easily be corrected by restarting the Tor process. So I took the entry out of the fcrontab again and decided to start a manual script so that I could then restart the Tor process so that it would continue normally without any problems.
So everything worked again without me noticing anything.
I suspect that by changing the IPS provider, there were now complications in connection with the groups created by the script, or with the entries in the iptables with the wrong references, which finally completely shot down the system.
Although the script is not executed automatically, the exact same error message also appears when booting the Ipfire…as if it were being executed. The script tries to read the iptables in the same way as during the boot process.
The message says that the iptables do not know the companies or groups and the start of firewall.local is terminated twice with an error.
The script wants to create the firewall rules with the created firewall groups and this leads to the errors that the rules for the Tor node disappear and probably permanently wrong references/groups have been entered with which iptables cannot do anything, which leads to this permanent error message.
I don’t have much idea how to write iptables, how to write scripts or how to read scripts, but my conclusions are logical to the error messages, the script also comes from a trustworthy source, it was written especially for ipfire, but has not been updated for two years, which is probably the reason why it only works partially. Unfortunately the creator has not answered me and my attempts to find the script or the error myself failed, as I said I am a layman who only has a basic understanding of all this.
What is my question to you now… How do I get the IPS running again, or how do I clean up the iptables so that the conflicts no longer occur? Or is my only option a complete reinstallation of IPfire?
@ummeegge With you I see the biggest hope that you can help me to find out what exactly went wrong, because you also provide a similar script, which automates a blocking via the DNS level of the ASN entries with companies, if you want I can link you the script or post it here. The process is similar to yours, IP lists are created, I find this solution even more elegant because of the firewall groups, which you can then use for rules in the web interface, because you can determine exactly who has access to which networks. I would have already shared this with you if it had been error-free, I wanted to try it first to see if it remained stable despite the error, which is probably not the case.
Thank you in advance for reading and maybe someone can help, give their opinion or just laugh at me…