It is a fixed parameter since some Core Updates ago.
forgot about that. See this:
OpenVPN is automatically reconfigured to use a secure Diffie-Hellman parameter, both of sufficient length of 4,096 bit and standardized (see RFC 7919, section A.3, bug #12632). All OpenVPN clients and peers will automatically benefit from this cryptography improvement; no manual action is required. This also obsoletes the necessity of generating or uploading Diffie-Hellman parameters while configuring OpenVPN, saving a lot of time, as the generation of such parameters could have taken hours on slower hardware.
In the past I did not have a dynamic dns. I do now. Is it best to use that in the cert generation?
Ok, new certs new roadwarrior. No connect.
Log from the phone:
[Feb 06, 2024, 14:25:21] OpenVPN core 3.8.4connectX(3.git::c424d46c:RelWithDebInfo) android arm64 64-bit PT_PROXY
[Feb 06, 2024, 14:25:21] ----- OpenVPN Start -----
[Feb 06, 2024, 14:25:21] EVENT: CORE_THREAD_ACTIVE
[Feb 06, 2024, 14:25:21] Frame=512/2112/512 mssfix-ctrl=1250
[Feb 06, 2024, 14:25:21] NOTE: This configuration contains options that were not used:
[Feb 06, 2024, 14:25:21] Internal option allowed only to be pushed by the server
[Feb 06, 2024, 14:25:21] 17 [auth-token-user] [USER]
[Feb 06, 2024, 14:25:21] 18 [auth-token] [TOTP]
[Feb 06, 2024, 14:25:21] EVENT: CORE_THREAD_ERROR info='option_error: sorry, unsupported options present in configuration: Internal option allowed only to be pushed by the server (auth-token,auth-token-user)'
[Feb 06, 2024, 14:25:21] EVENT: CORE_THREAD_DONE
Please follow the tutorial to the letter, the 2FA authentication is not supported by OpenVPN Connect.
Create roadwarrior tutorial?
The tutorial I linked previously, contains a roadwarrior setting for Android and iOS.
No change, won’t connect.
Those lines have been present in .ovpn profiles even for non 2FA client connections and they are ignored by my Network Manager and OpenVPN for Android clients.
Maybe they used to be ignored by the OpenVPN Connect for earlier versions but now are flagged up[ as a problem and prevent the acceptance of the .ovpn profile.
From my understanding you have not checked the box labelled “Enable OTP:”
so in that case you could edit the .ovpn file and remove the following lines:-
auth-token-user USER
auth-token TOTP
and then retry installing that .ovpn profile and the ta-key/.p12 files.
Just to be clear. the ta.key doesn’t need to be in the .ovpn file?
Ok, did that, installed the cert, etc.
Now try to connect and it times out.
If you have the TLS Channel Protection checked as per
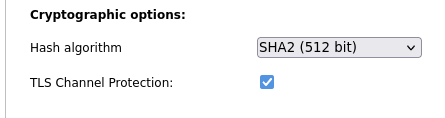
then yes you need the ta.key in the .ovpn file and in the connection zipped package.
If you have the TLS Channel Protection not checked as per
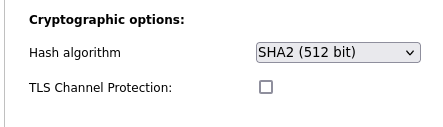
then no the ta.key should not even be in the .ovpn file and should not be in the connection zipped package.
However the TLS Channel Protection being checked does give you better security for your OpenVPN Tunnel.
It would be useful to see what the client log and the IPFire server log say for that connection attempt. Without that then there can be a myriad of reasons for why a connection might timer out so it would be just guesswork on our part.
I think when I set mine up.
I put in everything but the cert.
Then tried to make a connection.
It ask for the cert. then I added it.
This was not as strait forward as it should be.
A Openvpn App nuance.
Here is the log from the last attempts. It is interesting that I did not attempt any connections in the time frame of the last 3 entries.
15:28:02 openvpnserver[30093]: 166.182.254.59:8204 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:28:02 openvpnserver[30093]: 166.182.254.59:8204 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:28:02 openvpnserver[30093]: 166.182.254.59:8204 TLS: Initial packet from [AF_INET]166.182.254.59:8204, sid=4daa0ab8 e1536fa3
15:28:02 openvpnserver[30093]: 166.182.254.59:8204 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 TLS_ERROR: BIO read tls_read_plaintext error
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 TLS Error: TLS object -> incoming plaintext read error
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 TLS Error: TLS handshake failed
15:28:04 openvpnserver[30093]: 166.182.254.59:8204 SIGUSR1[soft,tls-error] received, client-instance restarting
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 TLS: Initial packet from [AF_INET]166.182.254.59:8596, sid=2b0562cc 7a6aa4e3
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 TLS_ERROR: BIO read tls_read_plaintext error
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 TLS Error: TLS object -> incoming plaintext read error
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 TLS Error: TLS handshake failed
15:28:46 openvpnserver[30093]: 166.182.254.59:8596 SIGUSR1[soft,tls-error] received, client-instance restarting
15:29:04 openvpnserver[30093]: 166.182.254.59:5112 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:29:04 openvpnserver[30093]: 166.182.254.59:5112 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:29:04 openvpnserver[30093]: 166.182.254.59:5112 TLS: Initial packet from [AF_INET]166.182.254.59:5112, sid=6477880d efd1f5d5
15:29:04 openvpnserver[30093]: 166.182.254.59:5112 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 TLS_ERROR: BIO read tls_read_plaintext error
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 TLS Error: TLS object -> incoming plaintext read error
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 TLS Error: TLS handshake failed
15:29:05 openvpnserver[30093]: 166.182.254.59:5112 SIGUSR1[soft,tls-error] received, client-instance restarting
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 TLS: Initial packet from [AF_INET]166.182.254.59:8468, sid=c4a39082 8f752858
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 TLS_ERROR: BIO read tls_read_plaintext error
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 TLS Error: TLS object -> incoming plaintext read error
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 TLS Error: TLS handshake failed
15:29:47 openvpnserver[30093]: 166.182.254.59:8468 SIGUSR1[soft,tls-error] received, client-instance restarting
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 TLS: Initial packet from [AF_INET]166.182.254.59:8602, sid=cd5bc7cc c409771e
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 TLS_ERROR: BIO read tls_read_plaintext error
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 TLS Error: TLS object -> incoming plaintext read error
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 TLS Error: TLS handshake failed
15:30:54 openvpnserver[30093]: 166.182.254.59:8602 SIGUSR1[soft,tls-error] received, client-instance restarting
15:31:36 openvpnserver[30093]: 166.182.254.59:5055 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:31:36 openvpnserver[30093]: 166.182.254.59:5055 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
15:31:36 openvpnserver[30093]: 166.182.254.59:5055 TLS: Initial packet from [AF_INET]166.182.254.59:5055, sid=bc20911b 17ae077c
15:31:36 openvpnserver[30093]: 166.182.254.59:5055 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 OpenSSL: error:0A000086:SSL routines::certificate verify failed
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 TLS_ERROR: BIO read tls_read_plaintext error
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 TLS Error: TLS object -> incoming plaintext read error
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 TLS Error: TLS handshake failed
15:31:37 openvpnserver[30093]: 166.182.254.59:5055 SIGUSR1[soft,tls-error] received, client-instance restarting
16:50:30 openvpnserver[30093]: TLS Error: cannot locate HMAC in incoming packet from [AF_INET]38.132.109.169:33789
22:15:09 openvpnserver[30093]: TLS Error: cannot locate HMAC in incoming packet from [AF_INET]167.248.133.164:61032
23:18:11 openvpnserver[30093]: TLS Error: cannot locate HMAC in incoming packet from [AF_INET]51.195.4.41:54482
This is indicating that you have somehow or other revoked your certificate and therefore the verification will fail.
Once a certificate has been revoked it cannot be unrevoked. You need to create a new certificate.
If your Root/Host certificate for the server had been revoked then I believe the server would not even start, so this suggests that the certificate that the client has is the one that is revoked.
When you restarted creating the certificates on your IPFire system, did you install the new certificates into your phone. If you tried to install the old zip package into the phone after you had cleared your x509 system on IPFire and re-created it then those old certificates will no longer match with the new root/host certificate set on your IPFire.
I have now modified the .ovpn thusly:
.
#tls-auth ta.key
.
#auth-token-user USER
#auth-token TOTP
.
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
<censored>
-----END OpenVPN Static key V1-----
</tls-auth>
key-direction bidirectional
Moved the .ovpn and .p12 to the phone.
Added the .pk12
Added the .ovpn
Attempt to connect and the log IPFire>OpenVPN reports:
08:29:13 openvpnserver[30093]: 166.182.249.12:20990 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
08:29:13 openvpnserver[30093]: 166.182.249.12:20990 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
08:29:13 openvpnserver[30093]: 166.182.249.12:20990 TLS: Initial packet from [AF_INET]166.182.249.12:20990, sid=61fa6c00 9dcc2477
08:29:14 openvpnserver[30093]: 166.182.249.12:20990 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 OpenSSL: error:0A000086:SSL routines::certificate verify failed
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 TLS_ERROR: BIO read tls_read_plaintext error
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 TLS Error: TLS object -> incoming plaintext read error
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 TLS Error: TLS handshake failed
08:29:15 openvpnserver[30093]: 166.182.249.12:20990 SIGUSR1[soft,tls-error] received, client-instance restarting
08:29:56 openvpnserver[30093]: 166.182.249.12:14386 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
08:29:56 openvpnserver[30093]: 166.182.249.12:14386 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
08:29:56 openvpnserver[30093]: 166.182.249.12:14386 TLS: Initial packet from [AF_INET]166.182.249.12:14386, sid=91d6190a 544b39e3
08:29:56 openvpnserver[30093]: 166.182.249.12:14386 CRL: loaded 1 CRLs from file /var/ipfire/ovpn/crls/cacrl.pem
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 VERIFY ERROR: depth=0, error=certificate revoked: C=US, O=parkerhome, CN=Mac, serial=2
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 OpenSSL: error:0A000086:SSL routines::certificate verify failed
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 TLS_ERROR: BIO read tls_read_plaintext error
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 TLS Error: TLS object -> incoming plaintext read error
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 TLS Error: TLS handshake failed
08:29:58 openvpnserver[30093]: 166.182.249.12:14386 SIGUSR1[soft,tls-error] received, client-instance restarting
I cleared the cert (x509), regenerated, then created the roadwarrior zip.
Before moving any of those to the phone, I removed all old certs on the phone.
Edit: I went back and looked at the WUI OpenVPN page and noted I had not created a new roadwarrior. Once I did and made the edits as noted previously it connects.
Thank you Adolf for your help and patience.