Hi
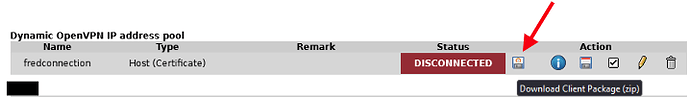
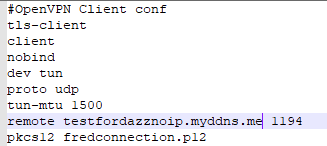
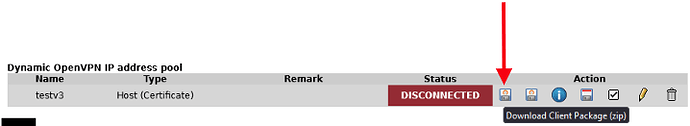
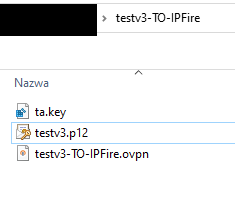
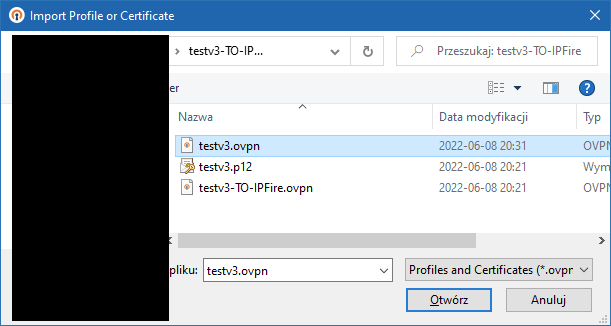
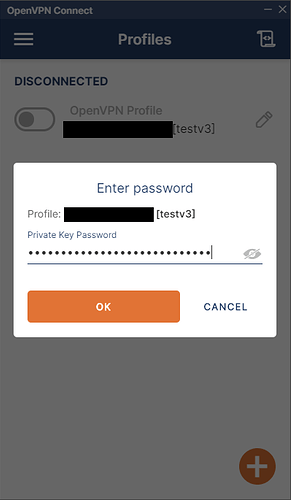
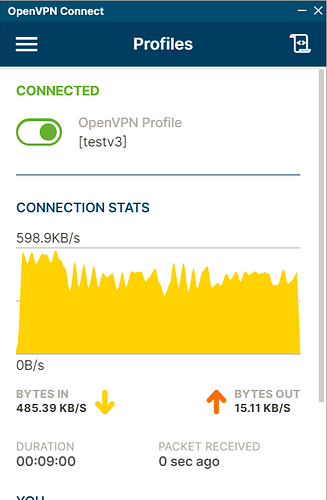
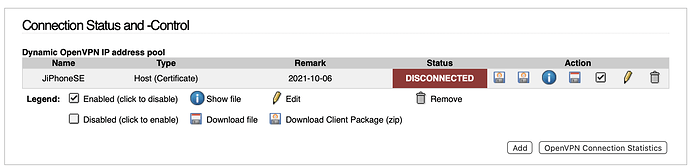
Downloading and using the zip file, rather than the PKCS12 file resulted in a successful VPN connection.
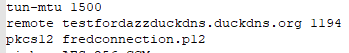
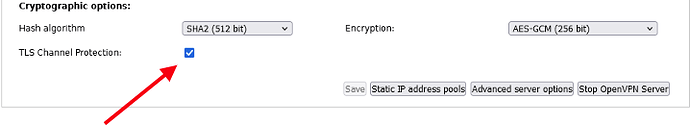
With ipCop, I only ever used the PKCS12 files so I had no reason to think that they would not work with ipFire.
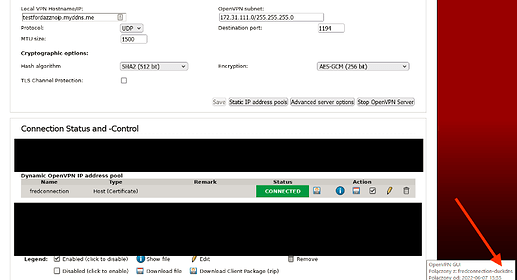
Here is the log for a successful VPN connection (client side)
Blockquote
Wed Jun 08 18:01:41 2022 OpenVPN 2.4.8 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Oct 31 2019
Wed Jun 08 18:01:41 2022 Windows version 6.2 (Windows 8 or greater) 64bit
Wed Jun 08 18:01:41 2022 library versions: OpenSSL 1.1.0l 10 Sep 2019, LZO 2.10
Enter Management Password:
Wed Jun 08 18:01:41 2022 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Wed Jun 08 18:01:41 2022 Need hold release from management interface, waiting…
Wed Jun 08 18:01:41 2022 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘state on’
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘log all on’
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘echo all on’
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘bytecount 5’
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘hold off’
Wed Jun 08 18:01:41 2022 MANAGEMENT: CMD ‘hold release’
Wed Jun 08 18:01:41 2022 MANAGEMENT: >STATE:1654682501,RESOLVE,
Wed Jun 08 18:01:41 2022 TCP/UDP: Preserving recently used remote address: [AF_INET]xxx.yyy.81.67:1194
Wed Jun 08 18:01:41 2022 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Jun 08 18:01:41 2022 UDP link local: (not bound)
Wed Jun 08 18:01:41 2022 UDP link remote: [AF_INET]xxx.yyy.81.67:1194
Wed Jun 08 18:01:41 2022 MANAGEMENT: >STATE:1654682501,WAIT,
Wed Jun 08 18:01:41 2022 MANAGEMENT: >STATE:1654682501,AUTH,
Wed Jun 08 18:01:41 2022 TLS: Initial packet from [AF_INET]xxx.yyy.81.67:1194, sid=58acae9e d6b6d67b
Wed Jun 08 18:01:42 2022 VERIFY OK: depth=1, C=NZ, ST=City, L=, O=test, OU=Director, CN=test CA, emailAddress=sales@test.co.nz
Wed Jun 08 18:01:42 2022 VERIFY KU OK
Wed Jun 08 18:01:42 2022 Validating certificate extended key usage
Wed Jun 08 18:01:42 2022 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Jun 08 18:01:42 2022 VERIFY EKU OK
Wed Jun 08 18:01:42 2022 VERIFY X509NAME OK: C=NZ, ST=Wellington, O=test, OU=Director, CN=xxx-yyy-81-67-adsl.sparkbb.co.nz
Wed Jun 08 18:01:42 2022 VERIFY OK: depth=0, C=NZ, ST=Wellington, O=test, OU=Director, CN=xxx-yyy-81-67-adsl.sparkbb.co.nz
Wed Jun 08 18:01:42 2022 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Wed Jun 08 18:01:42 2022 [222-154-81-67-adsl.sparkbb.co.nz] Peer Connection Initiated with [AF_INET]xxx.yyy.81.67:1194
Wed Jun 08 18:01:43 2022 MANAGEMENT: >STATE:1654682503,GET_CONFIG,
Wed Jun 08 18:01:43 2022 SENT CONTROL [xxx-yyy-81-67-adsl.sparkbb.co.nz]: ‘PUSH_REQUEST’ (status=1)
Wed Jun 08 18:01:43 2022 PUSH: Received control message: ‘PUSH_REPLY,route 10.158.55.1,topology net30,route 172.30.23.0 255.255.255.0,ifconfig 10.158.55.6 10.158.55.5,peer-id 0,cipher AES-256-CBC’
Wed Jun 08 18:01:43 2022 OPTIONS IMPORT: --ifconfig/up options modified
Wed Jun 08 18:01:43 2022 OPTIONS IMPORT: route options modified
Wed Jun 08 18:01:43 2022 OPTIONS IMPORT: peer-id set
Wed Jun 08 18:01:43 2022 OPTIONS IMPORT: adjusting link_mtu to 1524
Wed Jun 08 18:01:43 2022 OPTIONS IMPORT: data channel crypto options modified
Wed Jun 08 18:01:43 2022 Outgoing Data Channel: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Jun 08 18:01:43 2022 Outgoing Data Channel: Using 256 bit message hash ‘SHA256’ for HMAC authentication
Wed Jun 08 18:01:43 2022 Incoming Data Channel: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Jun 08 18:01:43 2022 Incoming Data Channel: Using 256 bit message hash ‘SHA256’ for HMAC authentication
Wed Jun 08 18:01:43 2022 interactive service msg_channel=412
Wed Jun 08 18:01:43 2022 ROUTE_GATEWAY 192.168.1.1/255.255.255.0 I=6 HWADDR=50:3e:aa:96:03:9a
Wed Jun 08 18:01:43 2022 open_tun
Wed Jun 08 18:01:43 2022 TAP-WIN32 device [Local Area Connection] opened: \.\Global{B1AA5CC6-A435-4BCF-A3AC-B2BAB535B8E5}.tap
Wed Jun 08 18:01:43 2022 TAP-Windows Driver Version 9.24
Wed Jun 08 18:01:43 2022 Notified TAP-Windows driver to set a DHCP IP/netmask of 10.158.55.6/255.255.255.252 on interface {B1AA5CC6-A435-4BCF-A3AC-B2BAB535B8E5} [DHCP-serv: 10.158.55.5, lease-time: 31536000]
Wed Jun 08 18:01:43 2022 Successful ARP Flush on interface [70] {B1AA5CC6-A435-4BCF-A3AC-B2BAB535B8E5}
Wed Jun 08 18:01:43 2022 MANAGEMENT: >STATE:1654682503,ASSIGN_IP,10.158.55.6,
Wed Jun 08 18:01:48 2022 TEST ROUTES: 2/2 succeeded len=2 ret=1 a=0 u/d=up
Wed Jun 08 18:01:48 2022 MANAGEMENT: >STATE:1654682508,ADD_ROUTES,
Wed Jun 08 18:01:48 2022 C:\WINDOWS\system32\route.exe ADD 10.158.55.1 MASK 255.255.255.255 10.158.55.5
Wed Jun 08 18:01:48 2022 Route addition via service succeeded
Wed Jun 08 18:01:48 2022 C:\WINDOWS\system32\route.exe ADD 172.30.23.0 MASK 255.255.255.0 10.158.55.5
Wed Jun 08 18:01:48 2022 Route addition via service succeeded
Wed Jun 08 18:01:48 2022 WARNING: this configuration may cache passwords in memory – use the auth-nocache option to prevent this
Wed Jun 08 18:01:48 2022 Initialization Sequence Completed
Wed Jun 08 18:01:48 2022 MANAGEMENT: >STATE:1654682508,CONNECTED,SUCCESS,10.158.55.6,xxx.yyy.81.67,1194,
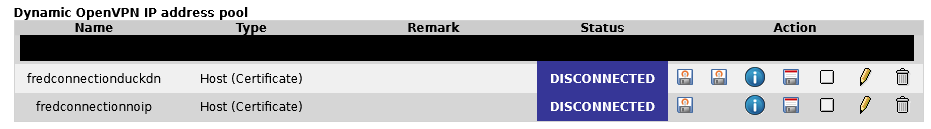
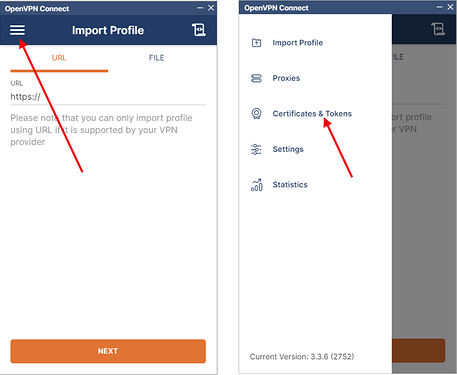
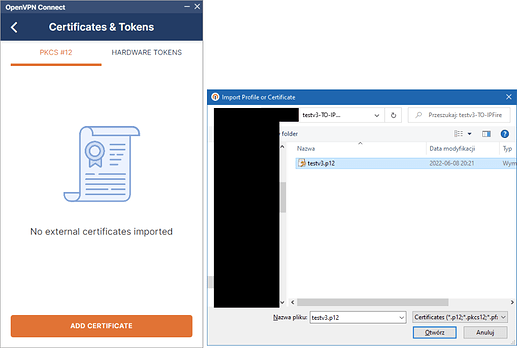
but it is not that simple because this worked with the Open VPN client version openvpn-install-2.4.8-l602.Win10.exe It did not work with the very latest client version ‘openvpn-connect-3.3.6.2752_signed.msi’ No changes were made on my (server) end.
So it seems likely there is some issue with openVPN.