Hi Matthias,
Continuing the discussion from Forcing all DNS traffic from the LAN to the firewall:
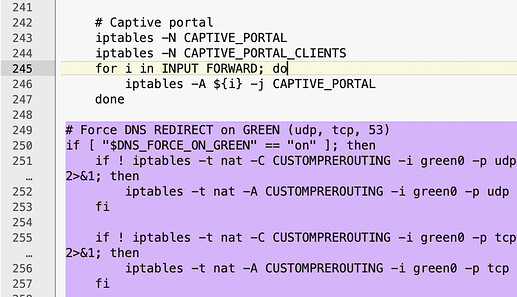
I tried to test some of the code from your developer list post. I really am not sure how to apply any of the patches in the post so I grabbed a chunk of code, removed the + and dropped it into my firewall.local. Not the most elegant solution!
#!/bin/sh
set -x
# Used for private firewall rules
#
# Use this at your OWN RISK. It is not fully supported!
# https://community.ipfire.org/t/forcing-all-dns-traffic-from-the-lan-to-the-firewall/3512
#
# See how we were called.
case "$1" in
start)
## add your 'start' rules here
DNS_FORCE_ON_GREEN="on"
DNS_FORCE_ON_BLUE="on"
NTP_FORCE_ON_GREEN="on"
NTP_FORCE_ON_BLUE="on"
;;
stop)
## add your 'stop' rules here
DNS_FORCE_ON_GREEN=""
DNS_FORCE_ON_BLUE=""
NTP_FORCE_ON_GREEN=""
NTP_FORCE_ON_BLUE=""
;;
reload)
$0 stop
$0 start
## add your 'reload' rules here
;;
flush)
iptables -t nat -F CUSTOMPREROUTING
;;
*)
echo "Usage: $0 {start|stop|reload|flush}"
;;
esac
# Force DNS REDIRECT on GREEN (udp, tcp, 53)
if [ "$DNS_FORCE_ON_GREEN" == "on" ]; then
if ! iptables -t nat -C CUSTOMPREROUTING -i green0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i green0 -p udp -m udp --dport 53 -j REDIRECT
fi
if ! iptables -t nat -C CUSTOMPREROUTING -i green0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i green0 -p tcp -m tcp --dport 53 -j REDIRECT
fi
else
if iptables -t nat -C CUSTOMPREROUTING -i green0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i green0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1
fi
if iptables -t nat -C CUSTOMPREROUTING -i green0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i green0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1
fi
fi
# Force DNS REDIRECT on BLUE (udp, tcp, 53)
if [ "$DNS_FORCE_ON_BLUE" == "on" ]; then
if ! iptables -t nat -C CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 53 -j REDIRECT
fi
if ! iptables -t nat -C CUSTOMPREROUTING -i blue0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i blue0 -p tcp -m tcp --dport 53 -j REDIRECT
fi
else
if iptables -t nat -C CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 53 -j REDIRECT >/dev/null 2>&1
fi
if iptables -t nat -C CUSTOMPREROUTING -i blue0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i blue0 -p tcp -m tcp --dport 53 -j REDIRECT >/dev/null 2>&1
fi
fi
# Force NTP REDIRECT on GREEN (udp, 123)
if [ "$NTP_FORCE_ON_GREEN" == "on" ]; then
if ! iptables -t nat -C CUSTOMPREROUTING -i green0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i green0 -p udp -m udp --dport 123 -j REDIRECT
fi
else
if iptables -t nat -C CUSTOMPREROUTING -i green0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i green0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1
fi
fi
# Force DNS REDIRECT on BLUE (udp, 123)
if [ "$NTP_FORCE_ON_BLUE" == "on" ]; then
if ! iptables -t nat -C CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -A CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 123 -j REDIRECT
fi
else
if iptables -t nat -C CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1; then
iptables -t nat -D CUSTOMPREROUTING -i blue0 -p udp -m udp --dport 123 -j REDIRECT >/dev/null 2>&1
fi
fi
Anyway, this snippet of code works A-OK!!