Howzit Jon
When you do a
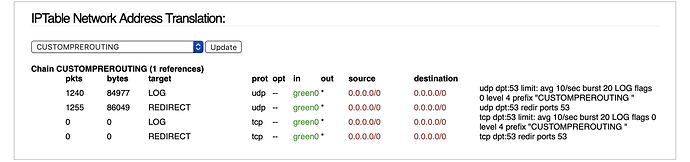
iptables -nvL -t nat
What is the output on CUSTOMPREROUTING? And does port 53 show up anywhere else?
Just out of interest sake…
These are the rules I have in my
/etc/sysconfig/firewall.local`
## add your 'start' rules here
# Force DNS for green to query the firewall, and not an outside DNS server
/sbin/iptables -t nat -A CUSTOMPREROUTING ! -o green0 -p udp --destination-port 53 -j REDIRECT --to-ports 53
/sbin/iptables -t nat -A CUSTOMPREROUTING ! -o green0 -p tcp --destination-port 53 -j REDIRECT --to-ports 53
/sbin/iptables -t nat -A CUSTOMPREROUTING ! -o green0 -p udp --destination-port 853 -j REDIRECT --to-ports 853
/sbin/iptables -t nat -A CUSTOMPREROUTING ! -o green0 -p tcp --destination-port 853 -j REDIRECT --to-ports 853
## add your 'stop' rules here
# DNS ReDirect flushing related chains
/sbin/iptables -t nat -F CUSTOMPREROUTING
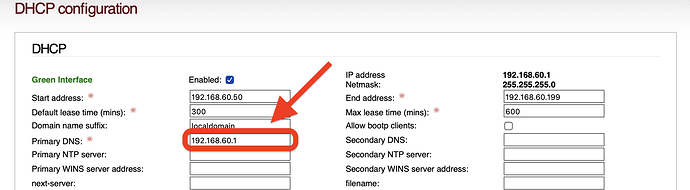
In the GUI FW side I also have entries permitting UDP&TCP traffic on ports 53 and 853.
These are however firewall rules, and not NAT rules.
I know they work, because on my LAN external DNS replies or results change when I change the DNS server I use to resolve things with on the FW.
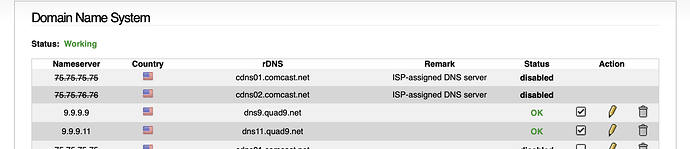
For example, instead of 8.8.8.8 change it to 185.228.168.10 or 185.228.168.168 (currently the server uses DNS over TLS, but that does not make a difference to the results below).
From a workstation on that network, check that you have another DNS server as the primary DNS entry. I for example set 8.8.8.8, no secondary DNS, and this is the result from the command prompt.
C:\Users\andi>nslookup google.com
Server: dns.google
Address: 8.8.8.8
Non-authoritative answer:
Name: google.com
Addresses: 2a00:1450:4001:801::200e
172.217.170.78
C:\Users\andi>nslookup pornhub.com
Server: dns.google
Address: 8.8.8.8
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** dns.google can't find pornhub.com: Server failed
As far as the workstation is concerned it is talking to 8.8.8.8 ias its DNS server, it does not know that the FW has a routing table entry that redirects the request to itself. The FW is currently using 185.228.168.10 and 185.228.168.11 as it’s source. Those two IP belong to Cleanbrowsing and have an Adult Filter on it. This means no xxx sites are accessible.
If your results differ, then you may have something else in the FW rules, causing a problem.
There won’t be any FW log entries, just in case you were wondering about it.
Hope this shines a bit more light on the matter.
cheers
UPDATE: Just a note on the -o versus -i
- -i is for the name of an interface via which a packet was received. As the request from the workstation may not be directed at the FW, but an external DNS server this entry would be mute. Otherwise you would need an entry for every DNS server that could be used.
-
-o is the name of an interface via which a packet is going to be sent or forward to.
As we are not trying to modify packets, and don’t know the destination IP, but do know on which protocols those packets will be send, we want to redirect only that traffic to another machine the -o is the correct use.
I have seen the errors of my ways 
DNS is usually UDP, but can also be done via TCP so you would need to have an entry for both on port 53.
DNS over TLS and DNS over HTTPS (shudder) are most likely not used by workstations directly, but if you want to prevent that add port 853 as well.
DNS over HTTPS would indicate the the queries go via 443, but that’s a misnomer. The client hopes that the DoH server will do the right thing, it however still sends out queries via UDP/53 or TCP/53, or 853.

 i think i may be confusing myself and probably everyone else with that explanation
i think i may be confusing myself and probably everyone else with that explanation