Hi
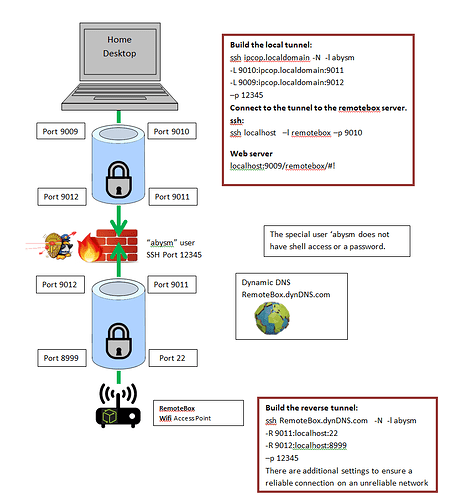
In my application, I want to setup an ssh reverse tunnel. The reverse tunnel is initiated by a unsecure remote client (ET phone home). The reverse tunnel stays live 24/7, but I only need occasional access from my end. I need to open a port on the RED interface to allow the reverse tunnel to connect to ipFire…
Typically ssh connections are forwarded from the firewall to a specific machine on the Green/Blue networks. I do not want to do that. If a bad actor gains access to the remote client and hacks in to get access to the machine, they will then be able to get onto my GREEN network.
My solution to this problem is to create a special user within ipFire called abysm using the commands:
$ useradd abysm -m -d /home/abysm -s /bin/true
$ usermod -p ‘*’ abysm
This creates a user with no shell access, and no password login access. Even if a hacker can tunnel to this user, they can’t go any further. The reverse tunnel terminates at the abysm user within ipFire.
The remote client initiates a reverse tunnel to the user absym. From my (any) pc on the green/blue network, I setup a forward tunnel that connects with the absym user. The tunnels are configured to connect end-to-end and act like they are seamless. It creates a tunnel from my pc to the remote client.
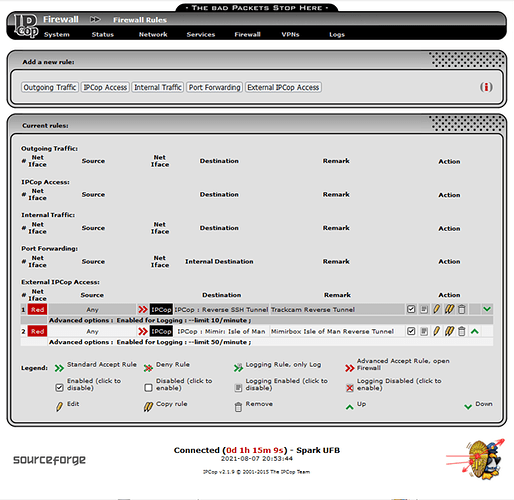
This is highly secure. This method creates a reverse tunnel that ends at a dead-end with no access to any ipFire protected network or machine. The tunnel is only open when I connect a forward tunnel to the end of the reverse tunnel. It would be a lot easier to explain if I could attach an diagram, but it worked well on ipCop. Now I need to replicate the setup on ipFire.
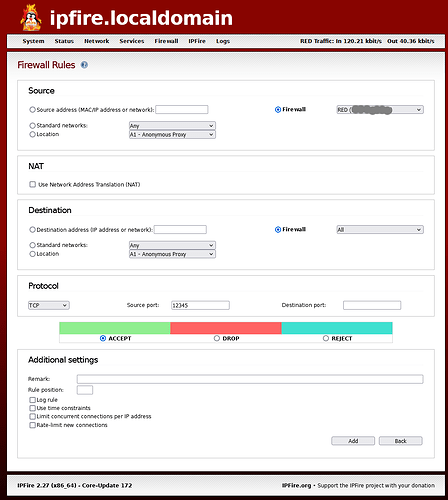
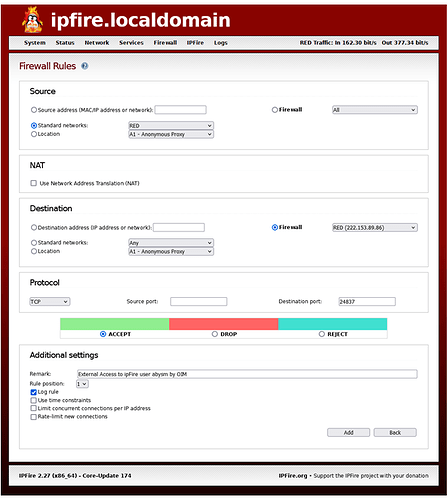
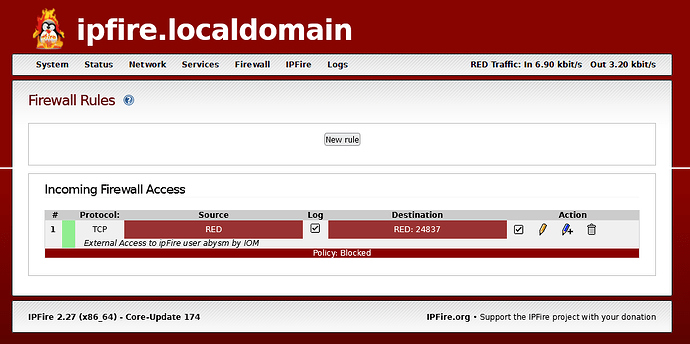
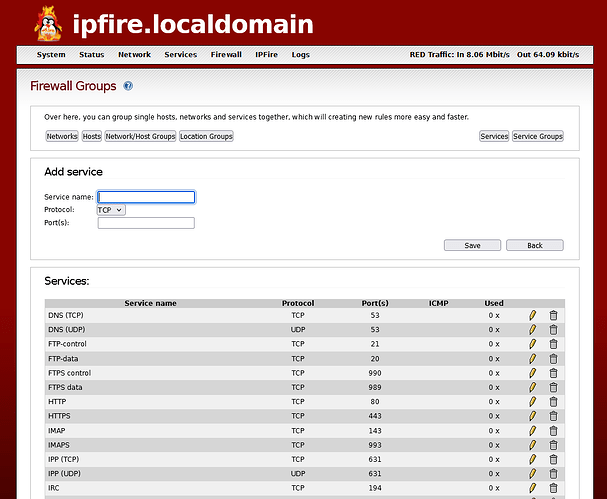
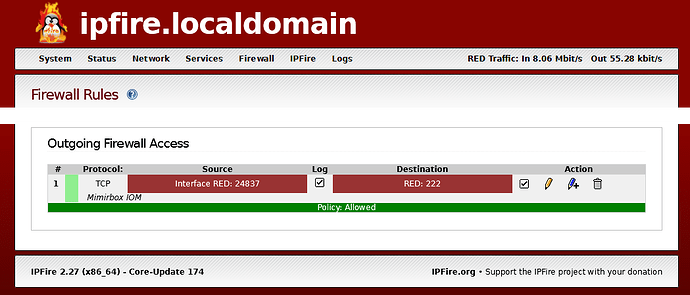
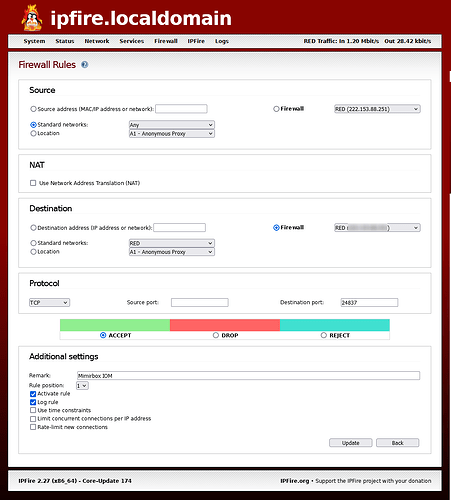
On the “Firewall Rules” page of ipFire, I have set the following entries:
Source
Standard networks RED
NAT
No tick in Use Network Translation (NAT)
Destination
Firewall RED
Protocol
TCP
At least one reason this won’t work is because none of the above opens the pin-hole destination port. I can’t find anywhere in the ipFire user interface/documentation where I can specify an incoming port to open without NAT. I am not forwarding the port.
If this is not something I can set up on the ipFire WUI, do I need to use iptables CLI??