Hi
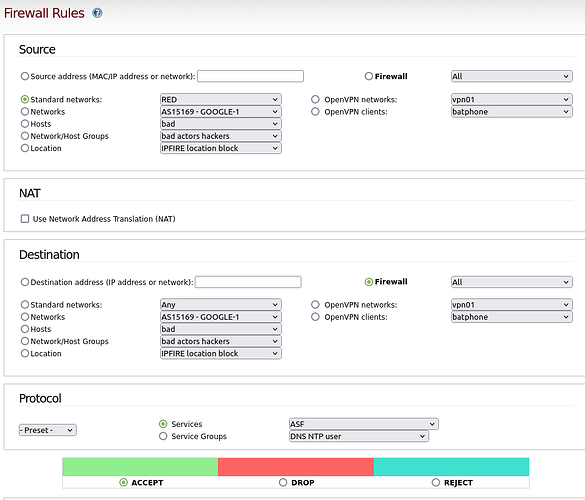
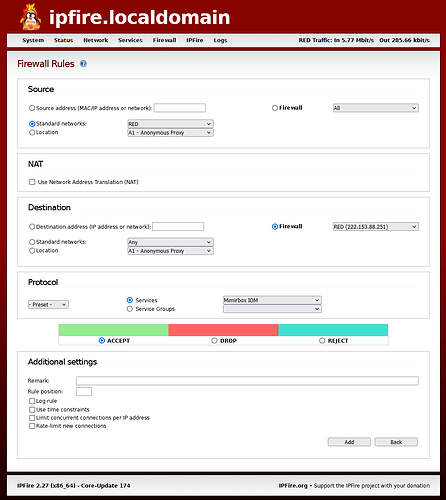
I have spent a few hours working on this today. I tried the Firewall Rules with the settings shown above, that included the custom service. I also turned on DEBUG1 level in the ‘/etc/ssh/sshd’_config file so I could see the logged response by ipFire.
The result is the same as before but worse.
I can gain remote access with the command $ ssh -N -222 -v abysm@123.456.789.0
I can see this in the ipFire logs.
I then ran the command $ ssh -N -24837 -v abysm@123.456.789.0
The connection was refused, but nothing showed in the ipFire logs.
I then added Port 24837 to /etc/ssh/sshd_config and restarted sshd.
I now have Port 222 and Port 24837 entries.
When I ran the ssh command with -p222, I connect.
When I run the same ssh command with -p24837, the connection is refused. This is worse than before.
Before I added the custom service to the Firewall Rules, I could connect by adding -p24837 to /etc/ssh/sshd_config. Now the connection is refused. Nothing appears in the ipFire logs. It appears that the connection attempt never makes it to sshd. I don’t think this has anything to do with specifying a service.
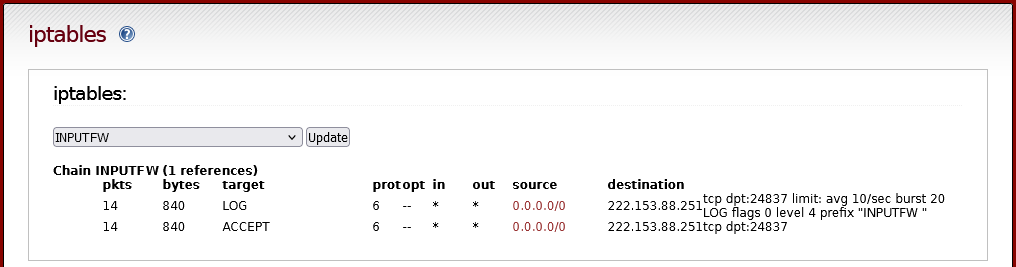
I looked at the iptables page on the ipFire WUI. I have little knowledge of iptables, but it appears that the connection attempt on port 24837 is being routed back out to the Internet.
From the ipFire CLI, I get:
`# iptables -S | grep 24837
-A INPUTFW -d 222.153.88.251/32 -p tcp -m tcp --dport 24837 -m limit --limit 10/sec --limit-burst 20 -j LOG --log-prefix "INPUTFW "
-A INPUTFW -d 222.153.88.251/32 -p tcp -m tcp --dport 24837 -j ACCEPT `
and also:
`# iptables -L | grep 24837
LOG tcp – anywhere 222-153-88-251-fibre.sparkbb.co.nz tcp dpt:24837 limit: avg 10/sec burst 20 LOG level warn prefix "INPUTFW "
ACCEPT tcp – anywhere 222-153-88-251-fibre.sparkbb.co.nz tcp dpt:24837
`
- For anyone concerned about me revealing my actual ip address, the ISP routinely changes it.
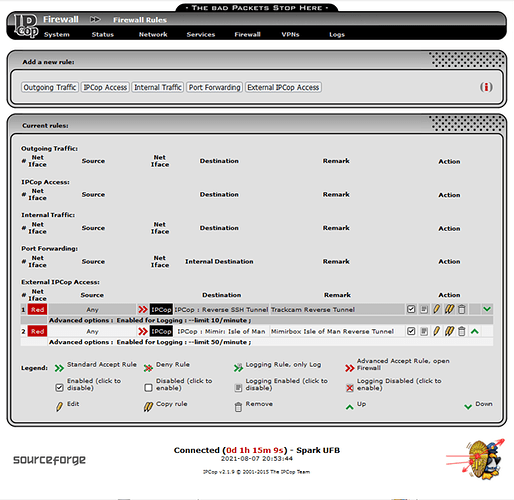
So it appears that the connection is being refused because the Firewall Rule is wrong. I think the traffic is being forwarded back out to the Internet. I want a rule that will allow me to route all traffic on port 24387 to within ipFire, and not out to any other network. ipCop included that as an option, but ipFire doesn’t.
My understanding of the instructions for external connections is to use RED as a destination to stay within ipFire, but that doesn’t work for me. I definitely want to block traffic on port 24837 escaping from ipFire out onto one of my networks.
So my question is how do I create a Firewall Rule that specifies ipFire as the destination (that is not all)?