That is a very valuable link. Should we add that? I have seen you have already added MODP-2048 which is very helpful.
Never mind. You have already been faster than me ![]()
You are just bouncing around guessing at things. Start with the information in /etc/messages and then troubleshoot from there. The “No Proposal Chosen” error or other errors surrounding proposals have to do with the encryption ciphers selected. Uncheck the box to only use selected proposals at first, so StrongSwan will not insist that the far side match with what you have selected in the Advanced page. Then, once you have a working connection, you can see what proposals worked in /etc/messages and then enable those items in the advanced page and re-select the checkbox. Leaving the checkbox deselected in the long run is a bad idea, as it can result in low quality encryption if the far side proposes it.
Hi Tom,
Thank you! I’m not sure I understand the above but let me give things a try before I ask too many questions!
In the beginning I was “just bouncing around guessing at things” since nothing made sense. One of the messages that was driving me insane is related to the %any.
Jul 22 22:42:47 ipfire charon: 10[CFG] selected peer config 'iPhoneSE'
Jul 22 22:42:47 ipfire charon: 10[IKE] no shared key found for '%any' - '101.185.xxx.xxx'
Jul 22 22:42:47 ipfire charon: 10[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Jul 22 22:42:47 ipfire charon: 10[IKE] peer supports MOBIKE
Jul 22 22:42:47 ipfire charon: 10[ENC] generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
-and-
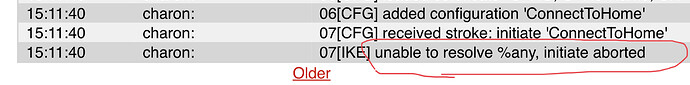
Jul 26 21:44:45 ipfire charon: 10[CFG] received stroke: initiate 'iPhoneSE'
Jul 26 21:44:45 ipfire charon: 10[IKE] unable to resolve %any, initiate aborted
Jul 26 21:44:54 ipfire charon: 11[NET] received packet: from <internetIP>[12720] to <iphoneIP>[4500] (128 bytes)
- What is
%anyin the above message log snippets?- is this an error? Or just info?
- Is this related to Remote host/IP?
- my Remote host/IP field is blank.
New / separate issue:
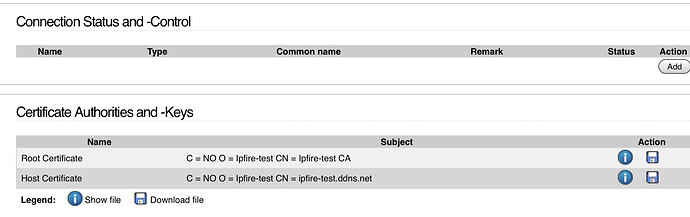
Is the IPsec x509 shared with OpenVPN x509? Or is it two different things?
I ask because my OpenVPN no longer works and I either broke something in the OpenVPN side -OR- I deleted its x509.
So, if I click the IPsec Remove x509 will it destroy the OpenVPN x509?
@jon: This is better.
For any tunnel you configure, the local and remote IP addresses need to be defined. For a Net-to-Net tunnel, you specify the actual IP address for the remote site. However, since a RoadWarrior can be anywhere, you don’t specify a specific address, you specify “%any”, meaning any remote IP can connect to this configuration. This is done automatically when you create a Host-to-Net tunnel, you don’t need to type it anywhere (the remote IP box is actually disabled for that reason, IIRC).
The first log snippet seems to be the results of initiating the tunnel from the iPhone.
- The “selected peer config ‘iPhoneSE’” message indicates that the system is picking the correct configuration. Now you need to make sure that the configuration is, well, configured properly.
- “no shared key found” seems to indicate that you have a PSK configuration selected, not a certificate configuration. What’s worse, it indicates that the system cannot find that PSK in the /etc/ipsec.secrets file, perhaps. I vaguely remember an issue where one had to either restart strongswan or force strongswan to read new PSKs when creating a new tunnel, but I think that was fixed 5 or more years ago. I suspect this is more of a symptom of your making 1,000 changes trying to make this work. It wouldn’t hurt to reboot IPFire, just in case, but maybe starting from scratch would be an even better solution. It depends on how many other things you have configured on this machine.
- The failure to find a PSK results in the final “AUTH_FAILED” message, as the system can’t successfully authenticate against a PSK it can’t find.
The second log snippet looks to me like you initiated the tunnel from the IPFire device, either as a side-effect of a configuration change (which shouldn’t really happen), or by issuing the command “ipsec up iPhoneSE” on the command line. What the second snippet is saying is that Strongswan on the IPFire box has received a command to bring up the “iPhoneSE” tunnel, and it immediately fails because the tunnel is configured to allow any host to connect, so it has no way of knowing what host to contact in order to bring the tunnel up. This is the very nature of a RoadWarrior tunnel, and the only odd thing is that IPFire was asked to bring that tunnel up. Perhaps it is a side effect of loading the tunnel from the configuration?
I’m pretty certain the clicking “Remove x.509” on the IPSec page will break any OpenVPN connections, but I’m no expert on OpenVPN, as it always seemed far too complex to me.
So let’s try to understand where I’m doing wrong.
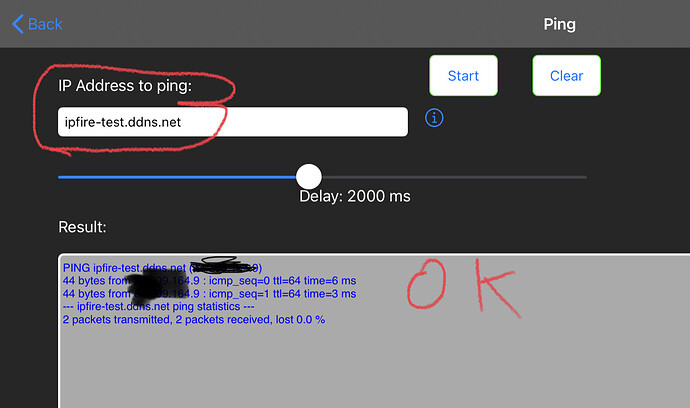
I’m using
Which shows my DNS is OK.
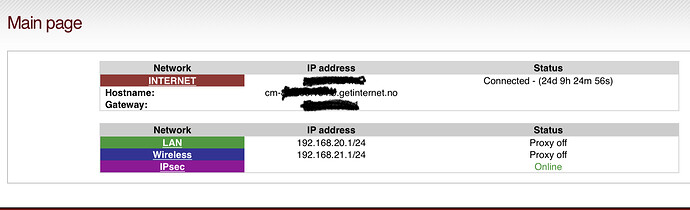
Also I like to showmain page with my ISP info.
I’m showing this, as host name isn’t same as my DNS host name.
In addition my iPfire installation has a different host name.
So the term host name can be a bit confusing.
However FQDN ought to be clear. It can be your host name, but it can also be something else. In my case I expect “iPfire-test.ddns.net” to be my only FQDN.
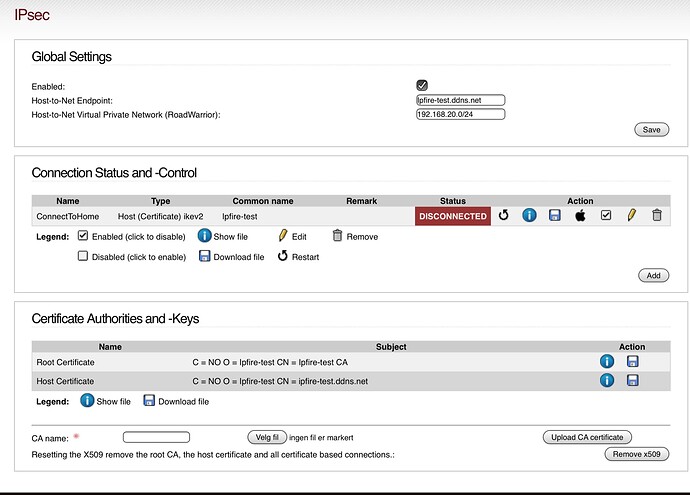
Next, there is 3 steps to be done:
- Create a global setting
- Generate a certificate
- Create a connection
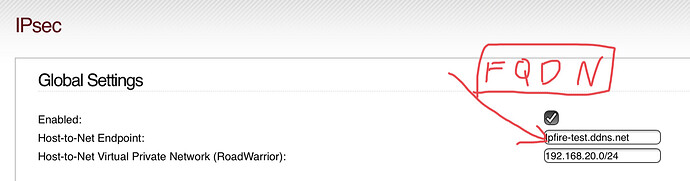
So, step one in my case look like this.
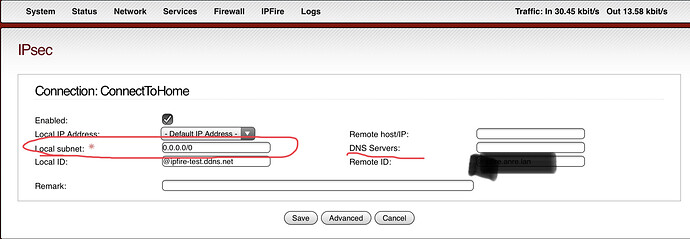
I’m not sure about the RoadWarrior setting, as the subnet isn’t part of my subnet locally. So 192.168.20.0/24 may working and may not. I don’t know. The zero before 24 is the number I rather change to 1, in order to comply with my local network. However my understanding from previous answers in this tread is it doesn’t matter, as this is just to assign an ip to the remote host. (My iPad).
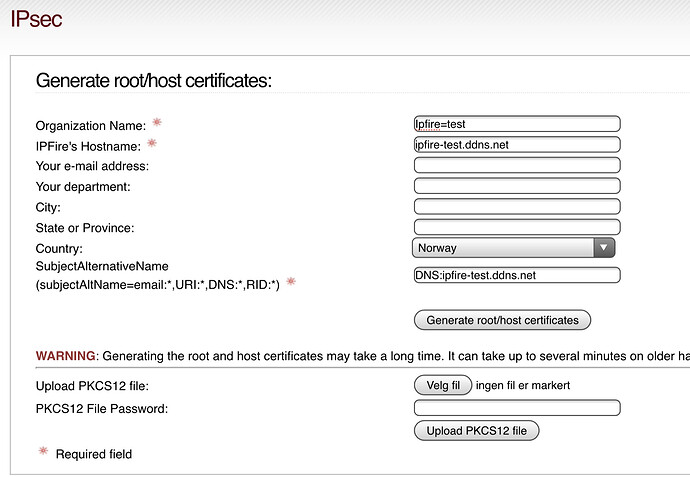
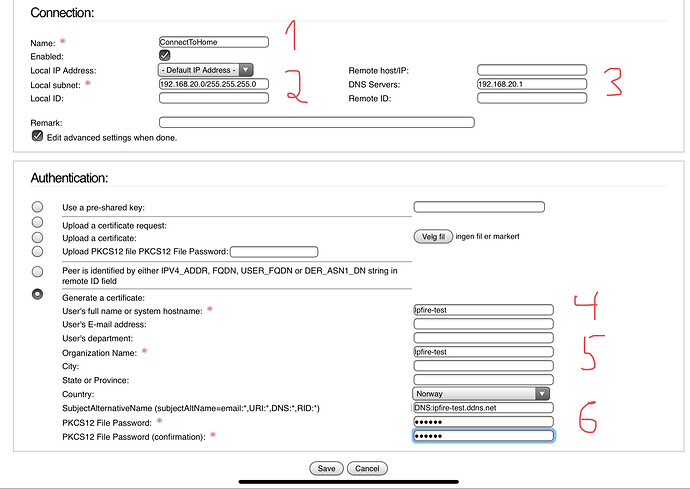
Next is certificate:
Appart from the first required filed which can be anything, the next two required fields has been assigned the FQDN. Is this correct ?
It’s very clear to me that the host name has to equal the FQDN.
The explanation under Subject Alternative Name is very confusing to me. It’s a requirement, but it says IF you have (then conditions), you CAN implement them here, like if I don’t have, leave blank. Also the choices is so many.
This must be better explained in Wiki.
Last is connection.
Wiki is here:
And it’s not helpful at all. And latest editing did it even worse.
Adding name is easy. Call it what ever you like.
Local and Remote ID isn’t required. So I leave blank. But I think it’s not correct, as somewhere else the wiki says it’s a requirement and I don’t understand those requirements transferred to my example.
Local ID must be set to the IPFire’s FQDN prefixed by an “@” sign. Remote ID must be the system’s hostname prefixed by an “@” sign and the hostname must also be added to the certificate as “Subject Alternative Name” prefixed with “DNS:”.
I will test with FQDN on local ID after. @ipfire-test.ddns.net ought to be the correct setting. My iPfire host name I’m not 100% sure about. I do expect my iPfire host name to comply with what I actually have named my installation, but my understanding from @jon is that I’m wrong in this case.
As suggest before, it ought to to be equal to what’s visible using this setting:
But my understanding is I’m wrong.
Local subnet may be 0.0.0.0/0, but can also be something else. My picture shows what iPfire suggested. I don’t to my knowledge have this subnet.
192.168.20.0
I have
192.168.20.1
DNS servers (in plural?) is hopefully my local 192.168.20.1. I don’t know.
Further there is a authentication to be filled in.
I assume name and organization name can be anything. And those are the two required fields (apart from PW).
I think however SubjectAlternativeName(subjectAltName=email:,URI:,DNS:,RID:) must be filled in.
I’m confused what to fill in. I think DNS:”your FQDN”. That will at least comply with what I did when using same field (well same name) in creating the certificate.
It was said before to equal the remote ID, but that field is now blank.
@ms says it’s working for him. But can you either show what’s working or tell me what I’m doing wrong ?
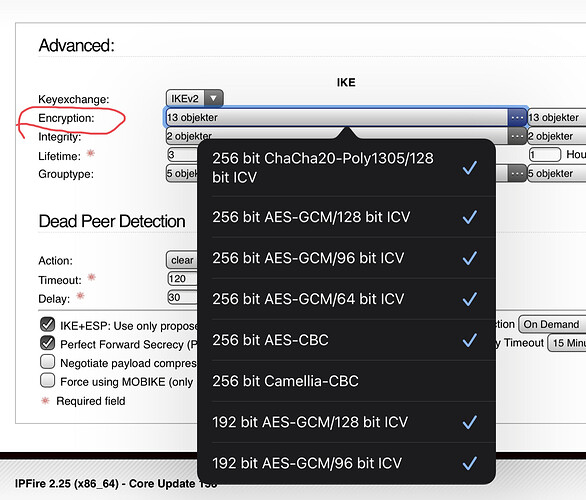
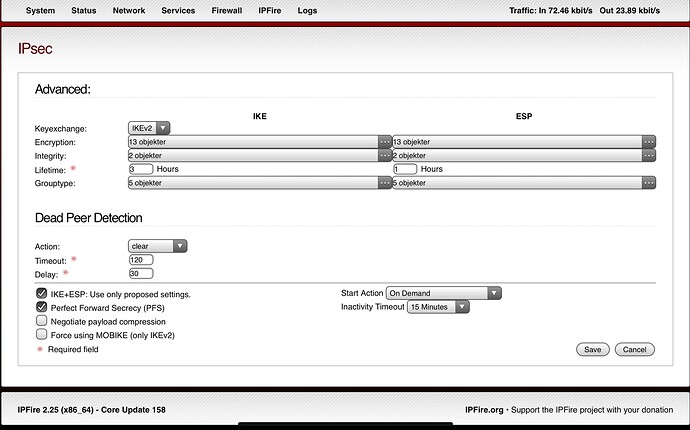
I’m now been taking to the advanced section.
Here the wiki has been updated, but it’s unclear to me if the suggested choices is the only one to select, or of I can add several more.
I’m using lates iOS 14.7
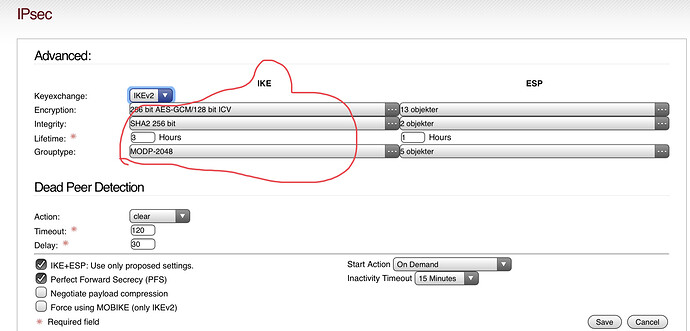
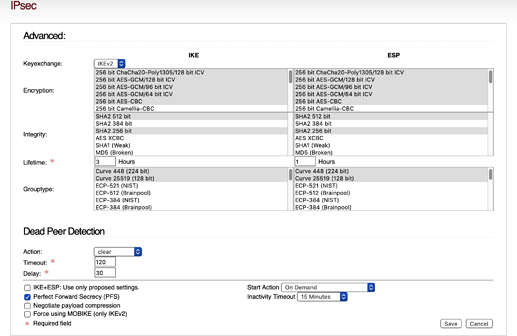
First question is if IKE and ESP settings shall be equal.
Next, the wiki doesn’t say which of possible 3 drop down selections to edit. And what is written in wiki isn’t shown at all as an option.
But one can guess.
- iOS 14: AES-GCM-256-128 / SHA2-256 / MODP-2048
Is probably here under encryption:
So question is, should I remove all default selections, and only select the 3 wiki says ?
I’m trying this for now.
So it’s looking like this and I’m ready for import to my iPad.
But it’s not working. So where to start and make corrections ?
Edit:
There is one error here for sure.
“ The hostname in the certificate has to match for MacOS and iOS to accept the certificate”
But I don’t fully understand that sentence.
We have host certificate and root certificate and then whatever shall be matched in iOS.
I’m sitting local at home and I’m doing everything on my iPad with Cellular.
But when testing IPSec, I’m switching of WiFi.
I can’t use WiFi to connect to IPSec. That’s impossible of cause.
Unless I was sitting in another WiFi than my home and at home is also where my iPfire installation is of cause.
Hi Jon,
No it will not. They are separate certificate structures. See following post from @pmueller
https://community.ipfire.org/t/ipsec-remove-x509-what-it-affects/5771/2
Further, it turns out this working VPN at the moment has no value to me. I’m not able to access my PC using RDT. (I was used to use ipCop and OpenVPN doing this before by using another computer).
So I tried some editing here:
Changing local subnet from 192.168……to 0.0.0./0 didn’t help.
Removing DNS servers didn’t help either.
Changing this one didn’t help either:
Well at least we know those fields won’t affect the working VPN connection.
So no is the big question, how to access anything locally?
Fire rules?
Just like to add, I didn’t edit anything on this page:
So all preselected parameters is OK. (On a iPad Pro).
Andreas: I know you’re frustrated, but please try to understand what the fields you are modifying actually do, which parameters in the StrongSwan config they correspond to, and then provide us with the relevant output from /var/log/messages so we can have useful details to go on. ‘grep charon /var/log/messages’ should do the trick if you don’t have other tunnels on the machine.
The local subnet field is one of the traffic selectors, and it determines what traffic will be sent to the tunnel, and where IPFire will allow the client to connect. “0.0.0.0/0” will allow the client to connect to anywhere, and is used when you want all of the client’s traffic, including internet traffic, to go over the tunnel and through IPFire. If memory serves, iOS client has odd behavior WRT that setting, and either will only send all traffic over the tunnel, or will only work with split tunneling, I can’t remember. If you set this equal to the RoadWarrior subnet defined in the IPSec page, it will only be able to contact that subnet. If you set it to the green subnet and the roadwarrior subnet, it will be able to contact devices on those two subnets (separate them with a comma).
At this point, you seem to have the tunnel established, but traffic is not flowing. The error logs should help point us in the right direction.
Hi Tom
Thanks for replying. Yes, I finally have a working tunnel. (Also working on my iPhone XS Max. Same profile tested).
I actually deleted the first working configuration in order to make a new one, where I’m 100% sure about what settings is working.
It’s all about where to put the FQDN and where to put your “real” iPfire host name.
I think my error may have been how I did step 2, creating certificate. There also the FQDN must be added.
Now it’s a challenge to understand what you’re trying to tell me ![]()
WRT ? How to obtain split tunneling ? (I will google as well).
Is the logs from here you’re asking ?
What is or where is exactly the RoadWarrior subnet ?
Maybe the field DNS servers in Connection?
This may be the key to a solution, but I have no idea where or how to do.
Is SSH only solution?
(It’s not a problem. There is of cause a nice IOS app for that) ![]()
Hi Tom - I’ve been experimenting with IKE+ESP: Use only proposed settings. in the unchecked mode.
Just for fun - I unchecked IKE+ESP: Use only proposed settings and then left the “default” Advanced settings as-is:
Is it this line?
Jul 28 16:12:24 ipfire charon: 05[CFG] selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/MODP_2048
-or- this line:
Jul 28 16:12:24 ipfire charon: 07[CFG] selected proposal: ESP:AES_GCM_16_256/NO_EXT_SEQ
Or something else? (I am assuming the first)
Let me know if you would prefer to see other lines in the message log.
Andreas @r1200cl - I’m going to pick one item at a time…
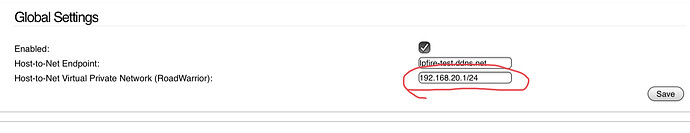
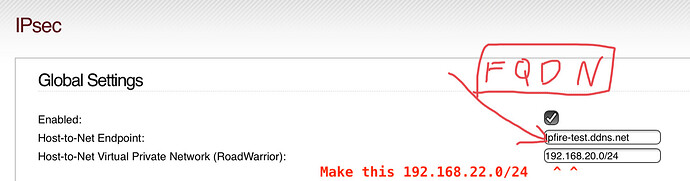
The Host-to-Net Virtual Private Network (RoadWarrior): is incorrect.
Per the images above it is currently part of your GREEN zone at 192.168.20.1/24. It should be a NEW subnet. Let’s pic: 192.168.22.0/24.
Jon
Tom - I am running iOS 14.6. And I set Local subnet to 0.0.0.0/0. No odd behavior that I have noticed. I can ping/connect to internal/external IP addresses and hostnames (name.locadomain) without issue.
Is there something I should be checking for?
EDIT: Sorry I don’t know “split tunneling”…
I got it! I’ve done this in the past but I didn’t know what it was called!!
![]()
@jon: When it’s set to 0.0.0.0/0, does your traffic to the Internet go through IPFire? You can check the IP address using Google (search “what is my IP Address”) or ipchicken.com.
From my iPhoneSE via LTE w/o IPsec VPN. This displays the IP address of my iPhone.
From my iPhoneSE via LTE with IPsec VPN enabled. This displays the IP address my IPFire box.
Hope that made sense!