I can generate a Cert just fine. But I am not sure it is correct since I cannot connect.
I tried GREEN, and BLUE and neither of them work. From the Wiki, it sounds like it is suppose to be a “new subnet”. I tried that also and it did not work for me…
@jon
Yes, documentation seems to indicate that the remote host (iPad or iPhone) is getting it’s own subnet where you assign an IP.
If this is correct, this may cause a problem for me, as my intention is have access to same subnet as home, in order to make what I’m testing to work. (Roon streaming).
A interesting observation is that if I put a higher number than 28 (tried 33 and 45), I’m getting an error.
Doesn’t matter if it’s 192.168.20.1 of 192.168.20.0
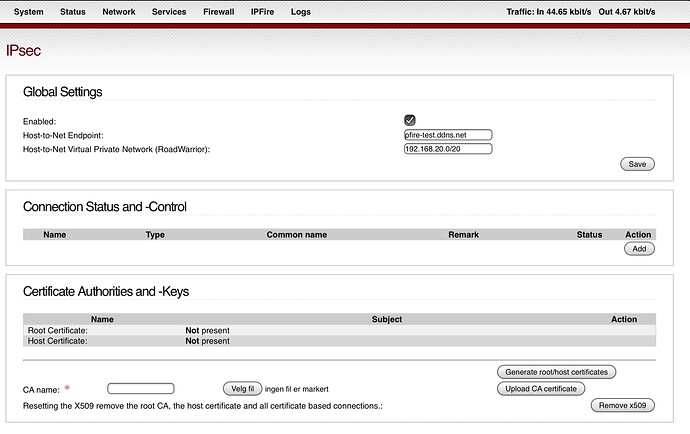
Are you referring to the far right number (the last 20) in the Host-to-Net Virtual Private Network (RoadWarrior): field → 192.168.20.0/20??
If so, please read about CIDR notation (and subnetting). I tried to find a good article for you and found these two links. You may want to keep searching for something better!
To the right of the / can be a number between 32 and 0. So 33 and 45 will not work.
EDIT: For me I picked /28 so I have 16 address to pick from (actually a few less but that doesn’t matter at the moment). But you may want to pick something like /24 (~256 address available). Hope this helps! Read up about CIDR. 
Ugh! I may have stumbled across an answer…
![]()
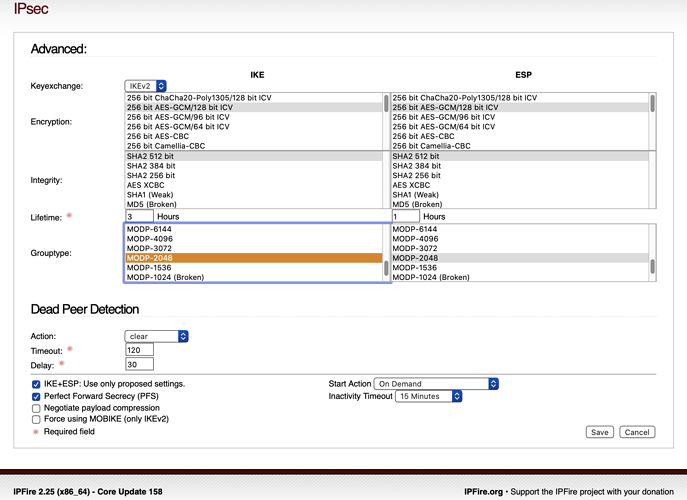
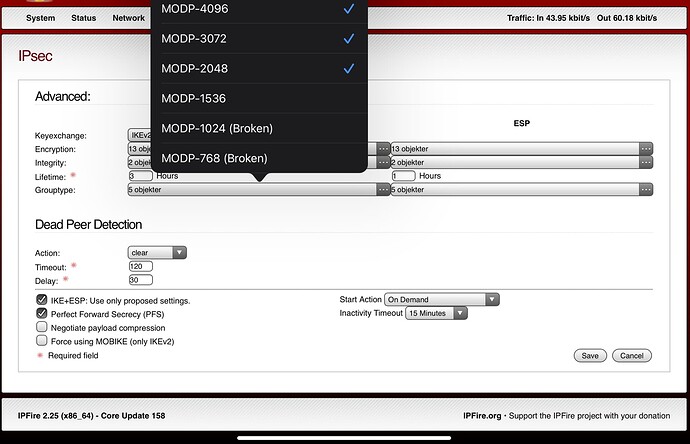
On the Advanced page change the Grouptype from MOD-1024 to MOD-2048.
I see the following in the IPFire messages log (/var/log/messages):
Jul 25 16:25:20 ipfire charon: 06[CFG] received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/MODP_2048
Jul 25 16:25:20 ipfire charon: 06[CFG] configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/MODP_1024
Jul 25 16:25:20 ipfire charon: 06[IKE] remote host is behind NAT
Jul 25 16:25:20 ipfire charon: 06[IKE] received proposals unacceptable
MOD-2048 is what my iPhoneSE sends (see 1st line). And the IPFire box was expecting MODP_1024. I am wild guessing the iPhoneSE doesn’t accept MODP_1024.
I just started testing but all looks good for the moment…
EDIT: FYI - this is testing a PSK and not a certificate.
The screenshot is from Safari 14.1.2 browser on macOS Catalina 10.15.7.
Maybe you are using giggle chrome? Or?
iPad. Safari or Chrome is equal. (Everything latest versions).
I’m wondering if my host name should equal the FQDN ?
So I should change host name from iPfire to iPfire-test (as shown in my examples) and then change domain to ddns.net
…or if there are some basic settings that I haven’t done other places.
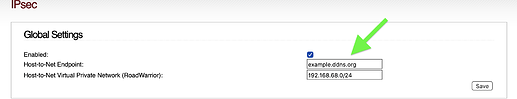
Are you referring to the Host-to-Net Endpoint: field?
If yes, then the field should be the name you obtained from ddns.net.
So for you: ipfire-test.ddns.net
Actually no. I’m thinking more in general how you name your iPfire installation.
I think the first part can only be done by SSH.
So it’s what’s been displayed here:
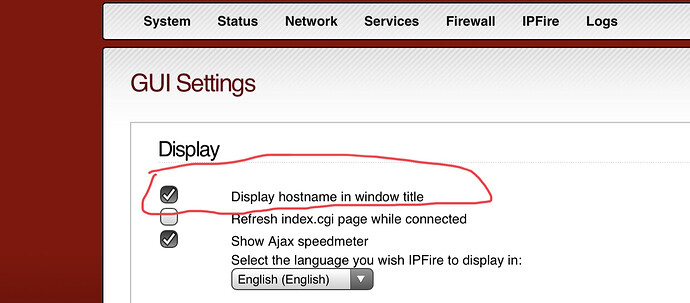
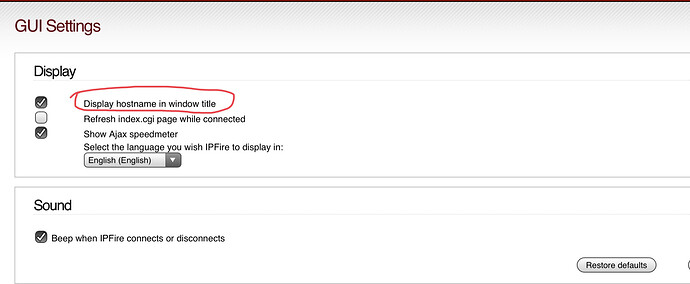
The Hostname in GUI Setting > Display should not match your FQDN. It has nothing to do with IPsec.
Just leave that hostname something simple like ipfire.
For now it is better to leave things simple until you get farther along…
OK, anyway I assume there is a minor bug in this release, and it’s being worked on, so eventually IPSec will work using road warrior with iOS.
I am not aware of any bugs in the implementation.
Could we try to organise this thread and collect any error messages from /var/log/messages if there are any? I just set up a connection and it worked straight away for me.
Hi Jon,
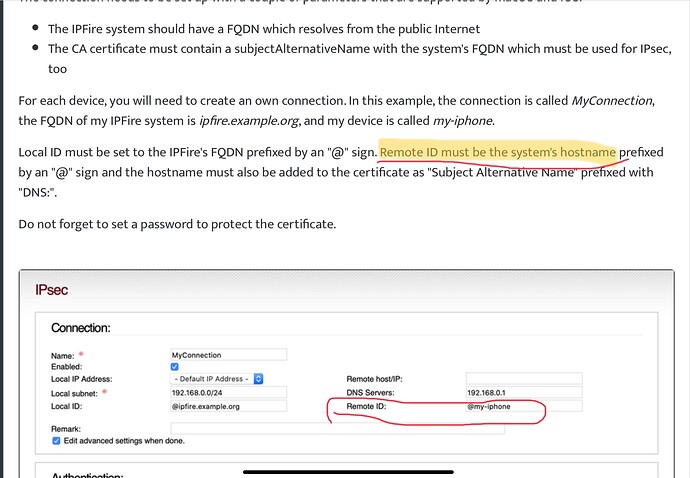
I believe that the following is meant.
The first bullet is saying that you need to have a FQDN for your IPFire system either as a fixed IP with your own domain name or with an IP from an ISP together with a domain name from a DDNS supplier.
The second bullet then says that the FQDN from the first bullet must be used for the subjectAlternativeName in the CA certificate that is being generated for your IPsec server
Hope this helps
Your explanation is correct. But, It’s not working. (At least not for me)
One year noip is now 14.95 by using code VIP10.
Andreas @r1200cl -
Are you using an iPad Wi-Fi or an iPad with Cellular (LTE) to connect to IPsec?
So for me I am connected like this:
iPhoneSE via LTE → Internet → IPFire box
I am thinking you may be connected like this:
iPad Wi-Fi → wi-fi → IPFire box
And that will not work…
Michael,
The issue for me was Wiki-ish. no bugs found!
I am using iOS 14.6. The Diffie Hellman Group (DH group) was updated from MODP-1024 to MODP-2048 after iOS 14.2. So MODP-1024 did not work for me.
See Apple-VPN.IKEv2.ChildSecurityAssociationParameters.
This is the error in the message log:
https://community.ipfire.org/t/one-click-ipsec-vpns-for-apple-ios/5847/26?u=jon
What parameters did you use that worked?
This is the only one that works for me:
iOS 14 (default values): AES-256 (GCM or CBC) / SHA2-256 / MODP-2048