I stumbled upon this public DNS, it might be useful to someone in the Far East countries
Public DNS 119.29.29.29
Public DNS service provided by Tencent Cloud (DNSPod) is free for all users. It supports DoH, DoT, BGP Anycast, and ECS.
I stumbled upon this public DNS, it might be useful to someone in the Far East countries
Public DNS 119.29.29.29
Public DNS service provided by Tencent Cloud (DNSPod) is free for all users. It supports DoH, DoT, BGP Anycast, and ECS.
Chinese DNS provider. Oh my.
Yes, Chinese provider
someone asked for a DNS server in that part of the world.
I’ve been using https://www.dns0.eu for some time without issues.
Added entries also to wiki page.
There are also ZERO(malware filtering etc.) and Kids friendly servers
This DNS server claims “No DNS record blocking or manipulation”
It seems to be Anycast
Unfiltered Configuration
DNS-over-TLS/DoQ
p0.freedns.controld.com
76.76.2.11
Plain DNS
76.76.2.0 and 76.76.10.0
Privacy Policy
dig www.ipfire.org @76.76.2.11 +dnssec
; <<>> DiG 9.16.44<<>> www.ipfire.org @76.76.2.11 +dnssec
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14953
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 1232
;; QUESTION SECTION:
;www.ipfire.org. IN A
;; ANSWER SECTION:
www.ipfire.org. 6202 IN CNAME fw01.ipfire.org.
www.ipfire.org. 6202 IN RRSIG CNAME 8 3 21600 20240229000000 20240208000000 6900 ipfire.org. Jht8hS7bGe/hP0Vlm8BbE+KkRzB7nBJISypPQxIwTdXG61NWuEucR75N StElWtt53NVNjoauzdksz1jcvGpghD6iNOikd05jFPeBvH2j+0DDMqcc vPMsLvokL2E8OSbebdxsq0pJGMD1XdIc/aqiD3YpEtp1AnBavneqVtxr bZx64MzN3lwzMNM8EVKlHNBVYrJuIgyVhEwm1lJ5Og0aQox9R7YL9J3A +ftBxfTr0RV9snMATh8Lxdyr+70ql3eZNwhJmfRzACRsDaOY7hUOVgb/ 4plkIVjPDIQUXsIc9EUvsW10ZbzATRuQCvaiF1ewNl/BeLHIiGlx3IEs 0PIUPg==
fw01.ipfire.org. 3092 IN A 81.3.27.38
fw01.ipfire.org. 3092 IN RRSIG A 8 3 21600 20240229000000 20240208000000 6900 ipfire.org. tlxT4DGsV5OVa+5RC1JeDCrjXhnQ80+WXk1ewCbMNzPzLXs/283yA63s NiMcmz7haq+SnLRyO9G6xnFxzsdhnV1dLjKaj1YHx1gvUIhUKXhNP5CQ y40cFKPBcyZJXy1DQAMzfeJGz0wV/gErR3rt8c8ojPZNm+zi9Gx36qBy Tj0vqDCf7dKXt0OOPw9XbqlnH8hFyGYhc7RSz6imyybolFa2YzYB8DoJ ONWYlwdZQjWs6n5yJCHiwTqeudpe2r9FvKqCU6Fx2u0QtlsJl2hQ8zZ2 lqao4uvaPHNbdKOVUFfk4Yfl/Oe5R7CB0fayku+MCo8ltedm+izrHFDu dtDBnQ==
;; Query time: 29 msec
;; SERVER: 76.76.2.11#53(76.76.2.11)
;; WHEN: Sun Feb 18 18:04:11 PST 2024
;; MSG SIZE rcvd: 674
My usage of IPFire follows the goal “get pure IP access to the internet from some ISP, control the traffic by the device owned by me”.
This means no restrictions outside my gateway, neither by my ISP nor by any DNS server.
Filtering malware etc. by means of DNS can be done with the RPZ functionality of unbound and forcing DNS requests to IPFire’s DNS server.
This allows policies controlled by me only. Filtering DNS by external services includes some external storage of my DNS requests, logging and configuring doesn’t function without.
Just my opinion,
Bernhard
I totally agree, @bbitsch
In this thread we share unfiltered DNS servers, that claim not to store or censor any data.
Are you aware of any filtering by above DNS servers?
How do you display or lookup the response from Unbound RPZ when a query gets a NX or other negative response?
I can look at the unbound logs for the negative response:
Or in the message log:
Feb 19 11:39:10 ipfire unbound: [8391:0] info: rpz: applied [sblack] telemetry.malwarebytes.com. rpz-nxdomain 192.168.60.212@60312 telemetry.malwarebytes.com. HTTPS IN
Feb 19 11:39:10 ipfire unbound: [8391:0] info: rpz: applied [sblack] telemetry.malwarebytes.com. rpz-nxdomain 192.168.60.212@54385 telemetry.malwarebytes.com. A IN
Feb 19 11:39:20 ipfire unbound: [8391:0] info: rpz: applied [sblack] telemetry.malwarebytes.com. rpz-nxdomain 192.168.60.20@54243 telemetry.malwarebytes.com. A IN
I see there are a few interesting threads on a different forum discussing this DNS provider
“It’s basically NextDNS but without the control panel.”
https://www.reddit.com/r/nextdns/comments/10w10ce/dns0eu_a_new_dnsservice_by_nextdns_ehm_what/
https://www.reddit.com/r/nextdns/comments/12qnvig/does_nextdns_benefit_from_being_a_partner_with/
Perhaps the above quote is what @bbitsch was hinting to?
and perhaps that’s why NextDNS is not even mentioned on the wiki page?
I would recommend using their ‘open’ resolver
# open.dns0.eu
# The unfiltered version of dns0.eu. Use at your own risk.
[DNS-over-TLS/QUIC]
open.dns0.eu
[DNS-over-HTTPS]
https://open.dns0.eu/
[DNS53]
193.110.81.254
185.253.5.254
2a0f:fc80::ffff
2a0f:fc81::ffff
[Apple Configuration Profile]
https://dns0.eu/open.dns0.eu.mobileconfig
Quad9 filtering was discussed here a long while ago,
Anyone following the Sony vs Quad9 dispute? Basically the court ordered Quad9 to censor DNS queries because a DNS provider is just like Youtube .
This 2023 and 2024 test confirms that Quad9 is filtering DNS queries
Most of the tested DNS providers have few resolvers, mostly the “filtered” ones were tested.
Google Public DNS - 8.8.8.8 (for reference, unfiltered)
ControlD Malware - 76.76.2.1 (new in the test)
Norton ConnectSafe - 199.85.126.10 (new in the test)
UltraDNS Threat Protection - 156.154.70.2 (new in the test)
Quad9 - 9.9.9.9
Cloudflare for Families - 1.1.1.2
dns0.eu - 193.110.81.0
dns0.eu ZERO - 193.110.81.9
CleanBrowsing Security Filter - 185.228.169.9
Comodo Secure DNS - 8.26.56.26
If anyone want’s to test Quad9 “unfiltered” the address would be 9.9.9.10 (no DNSSEC)*
*Thanks @bonnietwin
That is why Quad 9 is in the list of DNS providers not recommended for IPFire.
According to their DNS website 9.9.9.10 has no DNSSEC validation!!
It is worth noting that they are no longer based in America.
and they comply with EU regulations.
Probably a win for everyone using it.
Hmm maybe basic dns0.eu should be moved to not recomended section? I tought it doesn’t filter traffic. ZERO service did filter some of the legimate sites I tried to visit.
I am not sure, we can test it out. did you try using the Open version or the regular dns0.eu?
The DNS server I found is not working in IPFire:
The Unfiltered ControlD DNS server is getting a time out when clicking on Check DNS servers.
Checking the Suricata log shows that a ET Info DoH Rule is getting triggered.
I will have to take some screenshots
I used regular dns0.eu ip adresses ending .0 and I haven’t sen anything special in suricata logs. I guess I haven’t visited any malware sites. ![]()
Now I switched to open.dns0.eu. I wonder why they don’t mention it anywhere in their site?
By the time I got to make a screenshot, the ControlD unfiltered DNS is validating.
Let me know if anyone is using the server
Yesterday it was timing out, and I found this in the Suricata log:
@porkyle Could you share the settings for your dns0.eu server?
I want to try it out but don’t know what IP to put, they only list a hostname
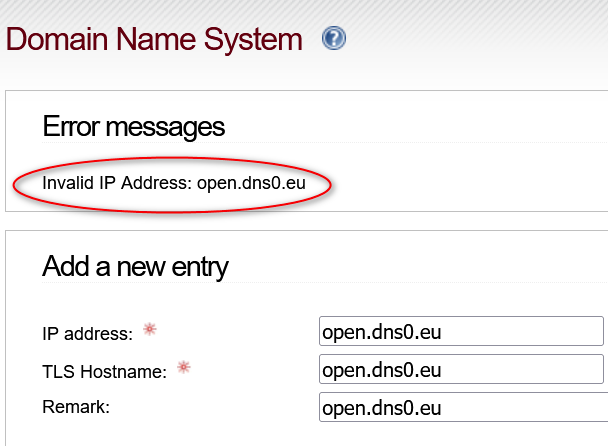
New DNS servers didn’t last long,
Check DNS gives Error TLS peer took too long to respond
Suricata logs
I don’t have a subscription to Proofpoint but this is what I can see about the Suricata alert
I guess you already find the IPs?
You are talking about suricata ET info rules and I don’t have those enabled. There seems to be rules that block those dns providers from working, you have to find and untick those rules.
From those screenshots it looks like surricate just detects dns TLS traffic for .dns0 and .controld domains and blocks them just because it was detected.
That refrence github page gives huge list of dns providers ![]()
I think those INFO rules are meant for monitoring or to block some services you don’t want your clients to use and some off them can be regular traffic, so not necessarily malicious web traffic.