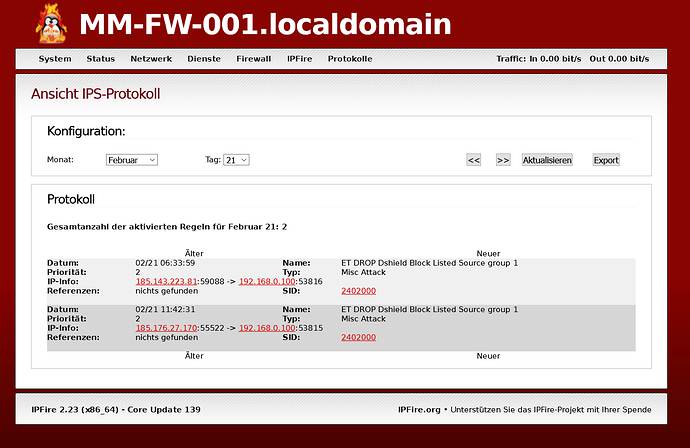
Hi @timf, I just tried the test against the http://www.eicar.org/download/eicar.com.txt file and it did not trigger an event. I am using the Talos VRT Subscribed rules, I have the policy-other rules enabled for all six of the EICAR rules within policy-other. I have policy set to “policy security-ips”
egrep “^drop|^alert” /var/lib/suricata/*.rules | wc -l – shows that 16124 are active/enabled
I do get events for other rules – such as these from /var/log/suricata/fast.log:
02/23/2020-01:46:30.181140 [Drop] [] [1:28556:3] PROTOCOL-DNS DNS query amplification attempt [] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 45.139.239.5:59217 → xx.xx.xxx.xx:53
02/23/2020-06:57:36.214406 [Drop] [] [1:28556:3] PROTOCOL-DNS DNS query amplification attempt [] [Classification: Attempted Denial of Service] [Priority: 2] {UDP} 172.105.216.159:60851 → xx.xx.xxx.xx:53
Could you try the EICAR antivirus test message to see if that is working as you would expect?
When I ran it, the download made it to my Windows PC – triggering an event in Windows anti virus
[Edit] rules enabled for EICAR antivirus test:
[root@ipfire suricata]# grep -i eicar /var/lib/suricata/policy-other.rules
drop tcp any any → any any (msg:“POLICY-OTHER eicar test string download attempt”; flow:to_client,established; file_data; content:“7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:37732; rev:3;)
drop tcp any any → any any (msg:“POLICY-OTHER eicar file detected”; flow:established; file_data; content:“|CB 68 9E 19 5D 89 56 55 DB ED 56 ED D9 4B D2 60 DC 0B E2 9E 17 8C D3 70 16 C6 D3 C4 4B FB 49 EA|”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop, service ftp-data, service http, service imap, service pop3; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:42376; rev:3;)
drop tcp any any → any any (msg:“POLICY-OTHER eicar file detected”; flow:established; file_data; content:“|08 43 1F A6 84 67 40 39 48 76 D3 FE 4B 3C 80 07 33 EF 32 83 6D 24 F4 B2 3D 48 15 90 BA E2 5C 40|”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop, service ftp-data, service http, service imap, service pop3, service smtp; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:42375; rev:3;)
drop tcp any any → any any (msg:“POLICY-OTHER eicar file detected”; flow:established; file_data; content:“|44 54 CD 3C BA 76 BF 75 53 47 28 94 1E 72 15 04 41 3B 9A B6 32 85 89 31 84 81 83 A6 42 DA 42 95|”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop, service ftp-data, service http, service imap, service pop3, service smtp; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:42374; rev:3;)
drop tcp any any → any any (msg:“POLICY-OTHER eicar file detected”; flow:established; file_data; content:“|CB 68 9E 19 5D 89 56 55 DB ED 56 ED D9 4B D2 60 DC 0B E2 9E 17 8C D3 70 16 C6 D3 C4 4B FB 49 EA|”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop, service ftp-data, service http, service imap, service pop3, service smtp; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:42373; rev:3;)
drop tcp any any → any any (msg:“POLICY-OTHER eicar file detected”; flow:established; file_data; content:“X5O!P%@AP[4|5C|PZX54(P^)7CC)7}-STANDARD-ANTIVIRUS-TEST-FILE!+H*”; fast_pattern:only; metadata:policy balanced-ips drop, policy max-detect-ips drop, policy security-ips drop, service ftp-data, service http, service imap, service pop3, service smtp; reference:url,www.eicar.org/86-0-Intended-use.html; classtype:misc-activity; sid:42372; rev:3;)
[root@ipfire suricata]#
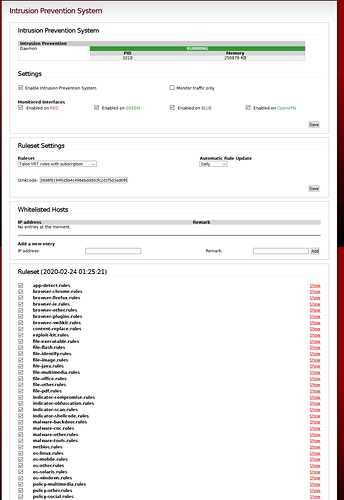
[Edit 2] screen snap of IPS settings: