New log-entries also available for green. So some trigger seem to be working.
But the problem told while starting the thread is the same: The IPS seems not to be reliable because the tested trigger doesn’t lead to a log-entry.
Doesn’t work anymore …
Tested again:
- Activated IPS on green with TALOS VRT: https://i.imgur.com/S1vUAHc.png
- Activated Rule FILE-EXECUTABLE download of executable content (Description: https://www.snort.org/rule-docs/1-16313): https://i.imgur.com/JP2ucWz.png
- Downloaded .exe (especially without SSL for testing): https://i.imgur.com/LJR6bmh.png
- Result: Nothing is logged https://i.imgur.com/zKzNjM3.png
Seems, that IPS doesn’t do what it should do on green interface …
Any ideas?
I wonder how the ips will work with encrypted http connections to trigger any rules.
@xperimental: Tested without encrypted connection as written.
This checkboxes specify which traffic should analyzed. To protect green clients you have to enable it on “red” and “green”.
If you choose only green it will not match that traffic.
@arne_f: As shown via hardcopy while opening the thread red was activated too. Without log-entries. But will try it again and give feedback …
Edit: Same result with activated red & green: https://i.imgur.com/FlFaGlY.png
-> Log is empty: https://i.imgur.com/qT1A17g.png
Ok. Also check if there is a wpad or other proxy setting if the proxy is enabled. If it runs via proxy the rules may not trigger on green becuase it runs via a different port.
But it should trigger on red in every case (except you have also configured an upstream proxy in squid).
Have you waited log enough before you have run the test. On my Maschine suricata needs some minutes to parse the rules.
OK. Proxy ist set transparent on green.
As you wrote, it should trigger on red in every case.
There is no upstreaming proxy activated.
@timf @stevee Isn’t this interesting? When I download http://www.eicar.org/download/eicar.com.txt from my web browser, no rule is triggered and the file is downloaded. However, when I try to download the file with curl, I do indeed get a rule triggered
02/29/2020-20:13:55.845800 [Drop] [] [1:37732:3] POLICY-OTHER eicar test string download attempt [] [Classification: Misc activity] [Priority: 3] {TCP} 213.211.198.62:80 → 192.168.x.x:54464
Same problem here. Setup a new ipfire 2.25 update 142 to test this behavior and the system allows the Eicar test file to pass. No clamav, no web proxy.
Same on ipfire update 141. 2 days before my Eicar test, Suricata detected a trojan virus in update 141, no configuration changes done.
The only difference to what stevee reports above:
curl https://www.eicar.org/download/eicar.com.txt on an Ubunutu machine lets the Eicar test file pass.
When I try curl to the http address, the Eicar server responds that it cannot find the filfe and points you to the https URL.
curl http://www.eicar.org/download/eicar.com:
301 Moved PermanentlyMoved Permanently
The document has moved here.
Apache/2.4.10 (Debian) Server at [www.eicar.org](http://www.eicar.org) Port 80
Is it possible that Suricata cannot determine the Eicar test virus in https and the Eicar server redirects http requests to https?
https traffic is ssl encrypted. Off course suricata cannot see it.
Me again.
IPFire 2.25 147.
IDS/IPS activated for monitoring on green and red.
IDS/IPS is running.
Using Talos VRT with Update 2020-08-07 09:44:42.
Activated some rules like:
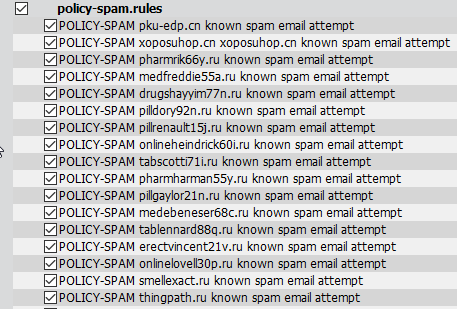
Tried ping to pku-edp.cn (first entry)
Tried http:// pku-edp.cn (first entry)
Both are working, but no Log-Entry!
So what is Suricata doing?
Edit: https://www.linkedin.com/pulse/test-case-suricata-vs-snort-ids-jesse-kurrus-m-s-it-ia/
Greetz,
Jan
ping or http is not mail traffic. The rules will not triggered by this.
They are for smtp or pop traffic.
@arne_f
OK, so it only works if there is the URL inside an E-Mail, but not, if someone tries to open the URL, for example from an E-Mail-Link?
Is there a best-practice-rule for testing IDS works?
Regards,
Jan