roberto
16 June 2022 08:31
1
Hi again guys!!!.
Looking at the LOGs, I see that there is a certain difference between what is displayed and what it says it has detected:
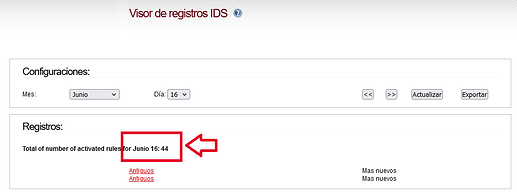
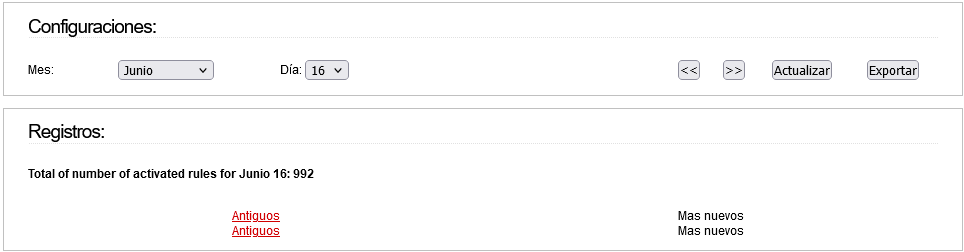
If I click on “Antiguos”, the following appears:
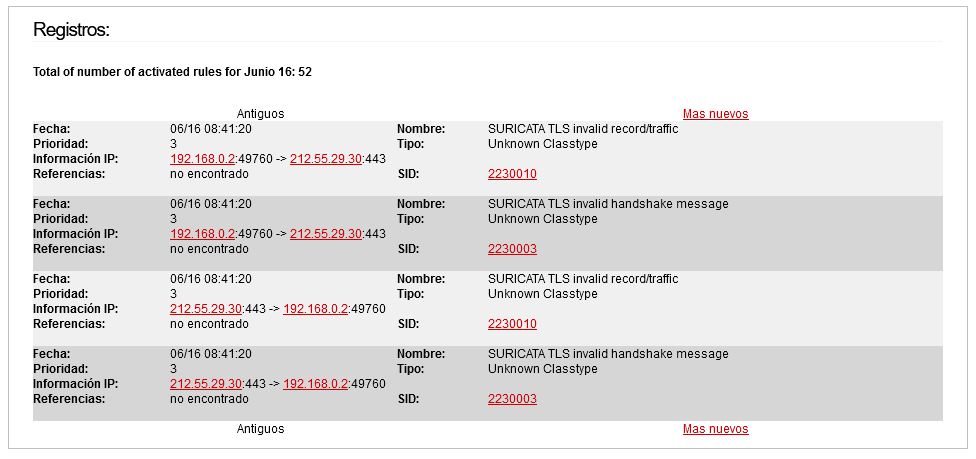
If I click on “Más nuevos”, the following appears:
(It seems that it has detected more, which are not displayed).
This shouldn’t happen, right?
Greetings.
I would not expect that to happen but I cannot duplicate the effect on my production CU168 system.
Mine shows:-
and pressing Older 6 times it always shows the same number.
What rulesets and which rules in them do you have selected. I can then try and duplicate your setup on my vm system and see if I can duplicate it.
If you do a grep for suricata in the messages log and for a date of June 16 how many entries do you find from that.
roberto
16 June 2022 13:21
3
Hi @bonnietwin thanks for your reply.
The problem is not the fact that there are a number of different detections, but the fact that nothing appears in the LOG.
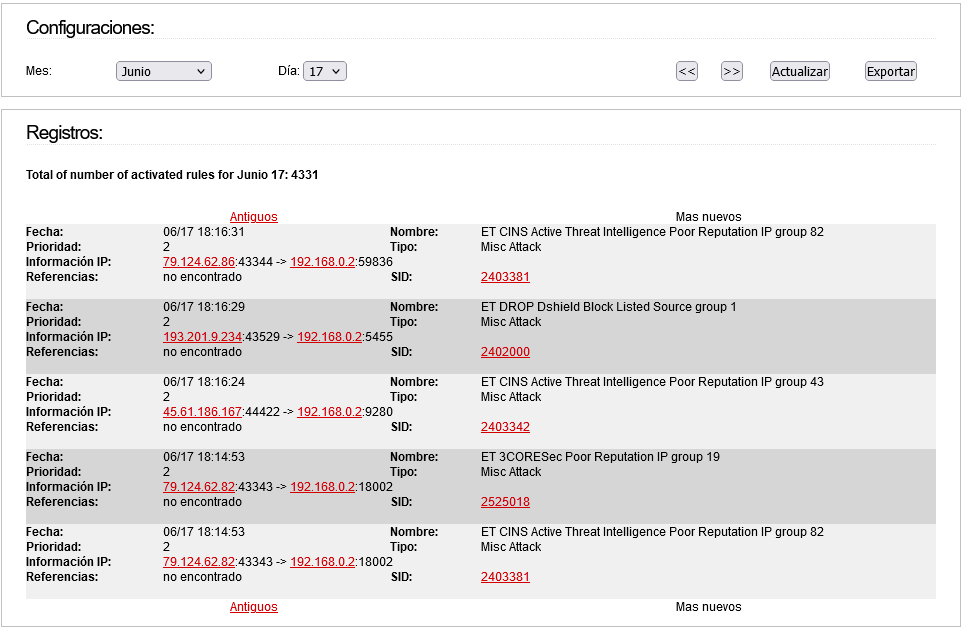
The number of detections is because when I took the screenshot, it varied.
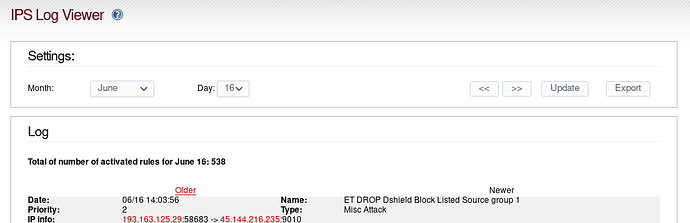
Now looks this:
I attach the entire LOG:
fast.zip (10,1 KB)
It is as if the pattern was not applied correctly to show it in the LOG.
Bye.
My apologies, I misunderstood the problem you are having.
Is there any message in the /var/log/httpd/error_log file for when the IPS Logs are accessed. Hopefully yes, as that would then give some clue as to why it is not showing them for you.
roberto
16 June 2022 18:21
5
Hi @bonnietwin .
Don´t worry.
In the LOG file I don’t see any related events. Just in case, I’m attaching it.error_log.zip (2,8 KB)
Regards
There are quite a few permissions problem messages related to pakfire.cgi but nothing related to ids.cgi in the log file.
Have you tried disabling the Intrusion Prevention System and then re-enabling it again.
roberto
17 June 2022 05:41
7
Hi again.
Neither reboots nor IPS disable/enable have any effect.
Let’s check that your ids.cgi file has not been modified in some way.
Run ls -hal /srv/web/ipfire/cgi-bin/ids.cgi and you should get the following line.
-rwxr-xr-x 1 root root 61K Jun 5 20:52 /srv/web/ipfire/cgi-bin/ids.cgi
If the permissions or the date are different then something has been modified somehow.
The b2sum hash for my production version is
e55c1e52493d11bc60a9e439465fd907034c0569cde42bd62dc09be2fb55679dae3d6a81638de5d62c8828aa0e7381e09a2dfb43043ff2ce27cdad0768b837ae
roberto
17 June 2022 16:08
9
Hi @bonnietwin
I have this version:
[root@bs ~]# ls -hal /srv/web/ipfire/cgi-bin/ids.cgi
-rwxr-xr-x 1 root root 61K Jun 5 20:11 /srv/web/ipfire/cgi-bin/ids.cgi
[root@bs ~]#
[root@bs cgi-bin]# b2sum ids.cgi
e55c1e52493d11bc60a9e439465fd907034c0569cde42bd62dc09be2fb55679dae3d6a81638de5d62c8828aa0e7381e09a2dfb43043ff2ce27cdad0768b837ae ids.cgi
[root@bs cgi-bin]#
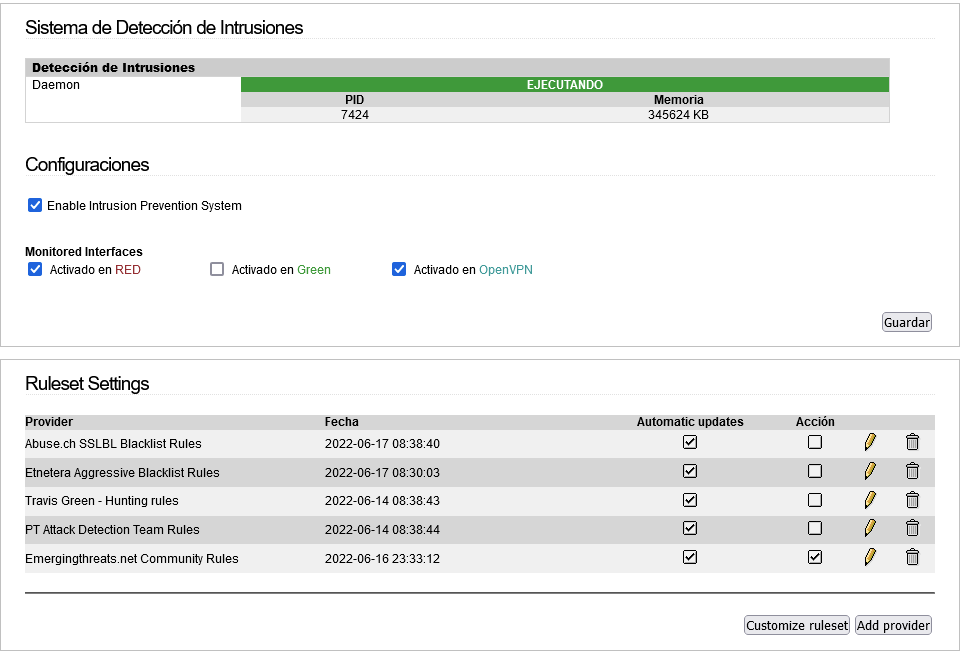
I am going to try to put another IPS provider to see if it is not capable of putting the information through filters. I tell you this, because in the old days, with Emerging Threats, the LOGs appeared, but since it consumed a lot of memory, I decided to try other providers, but although they consume less memory, they do not show anything in the LOGs.
I’ll try again with Emerging and I’ll tell you.
Greetings and thanks.
ag
17 June 2022 16:19
10
@roberto I had similar issues mentioned in Here but after disabling The PT Attack Detection Team ruleset, the issue was resolved.
It might be worth a try if you haven’t already
roberto
17 June 2022 16:21
11
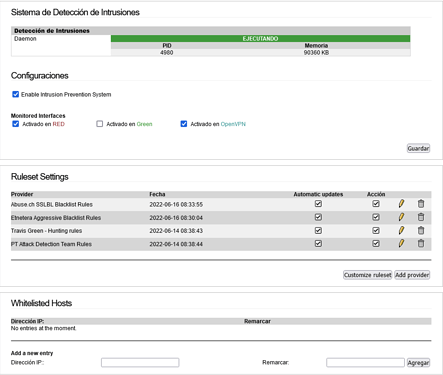
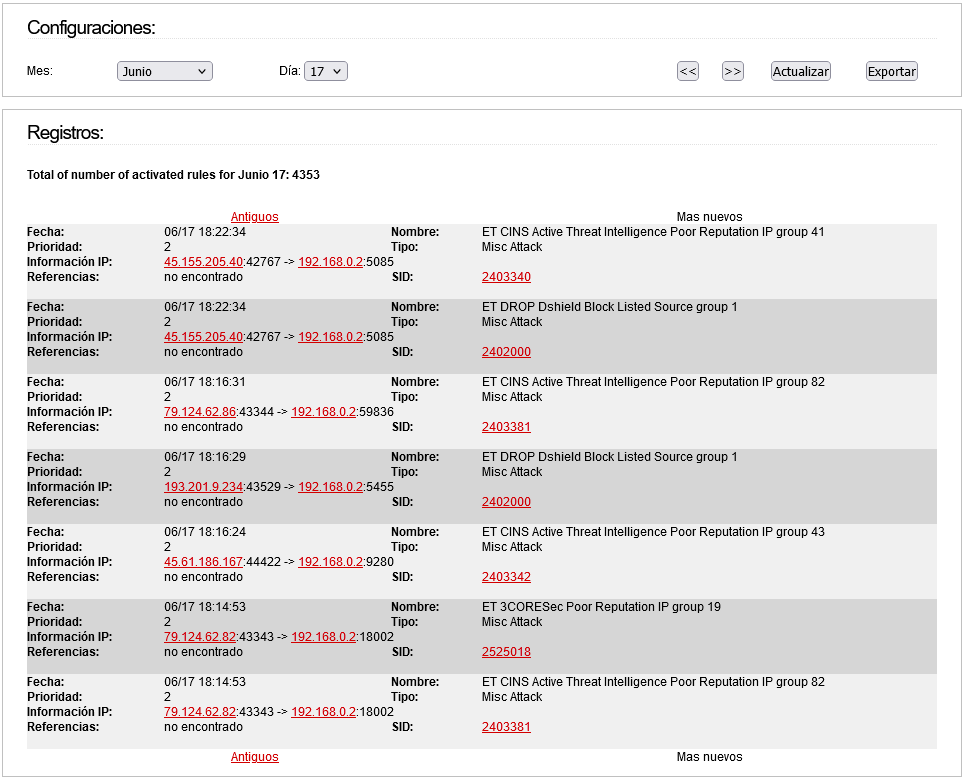
Yesss, with this configuration:
Appears this in LOGs (in two minutes):
Apparently, it only shows information in the LOG when it is Emerging.
roberto
17 June 2022 16:24
12
Hi @ag .
Thanks for your comment. I will try this.
P.D.: Unlucky.
roberto
7 July 2022 06:29
13
1 Like