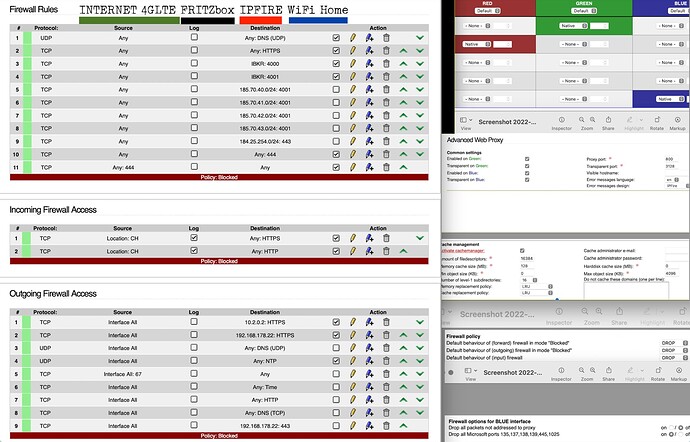
Version 171. Works smoothly. But is the Firewall hardened or complacent? Internet accessed via 4G LTE FritzBox then IPFIRE RED then BLUE Wireless to Home Computers. Use of GREEN from Desk. Policy is Blocked/Dropped. DNS is UDP. Note checked boxes HTTP and HTTPS. Is Squid maximized?
Firewall rules 10 and 11?
This looks like you may have opened your WUI to the red network.
Perhaps sources network green to 444
You can reed about network groups.
You could consolidate rule 5,6,7,8
Into a network group and have 1 firewall rule.
The Proxy is not my area of expertise.
If I have one in networking?
But block all not addressed to proxy sounds
Like hardening to me.
Incoming firewall access.
Don’t think you should need this.
If you do than limit it to the firewall itself.
This looks like you have a open port from the internet no port 80, and 443
I would suggest changing your DNS communication to use TLS protocol as this means any queries are encrypted.
IPFire TLS works well but it does not connect VPN/Wireguard. In the future, I may drop VPN/Wireguard and rely on TLS/DNSSEC.
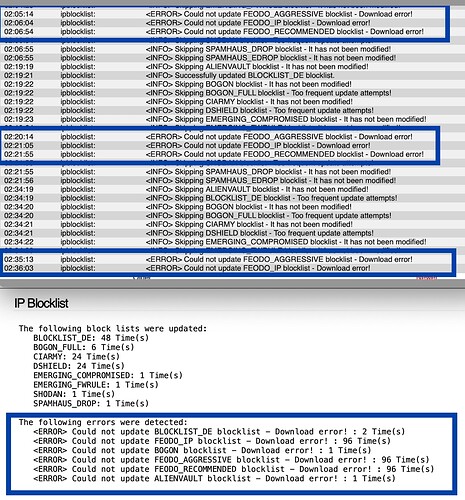
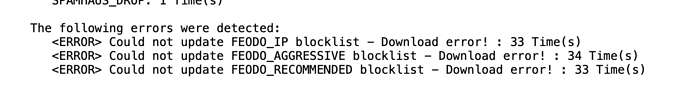
The problem with the Firewall is an error updating the Block List. What might cause that?*
This error message indicates that the attempt to download from the URL for those specific blocklists had some form of download error. It indicates that a connection was made to the URL but that during the download some issue happened.
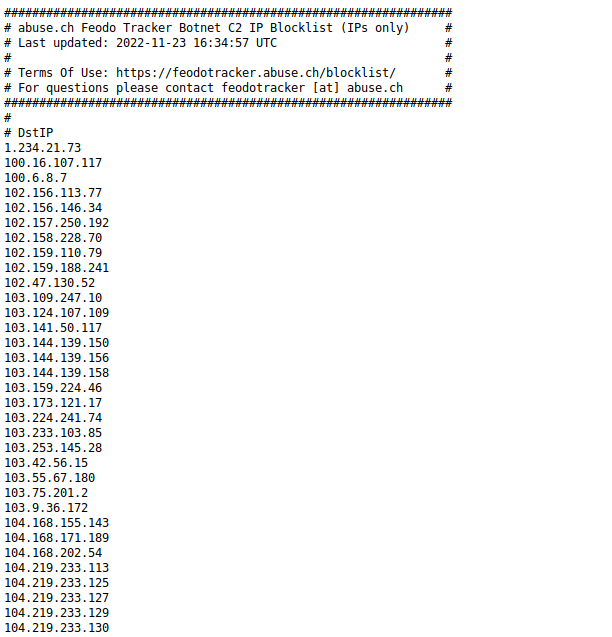
I just tried one of the URL’s and I was able to successfully access the blocklist.
https://feodotracker.abuse.ch/downloads/ipblocklist.txt
If you try this out in a browser only try it once and then not again for at least 5 minutes otherwise you will get your IP blocked by that blocklist provider as there rate limit is set to no more than every 5 minutes.
When I tried that url I got the following page.
The fcron updater runs every 15 minutes. If you look in the System Logs page and select the IP Address Blocklists entry from the dropdown box are you still seeing the error messages if you get a similar page shown as in the above screenshot.
If you don’t see the list of IP’s what message is being shown in the browser?
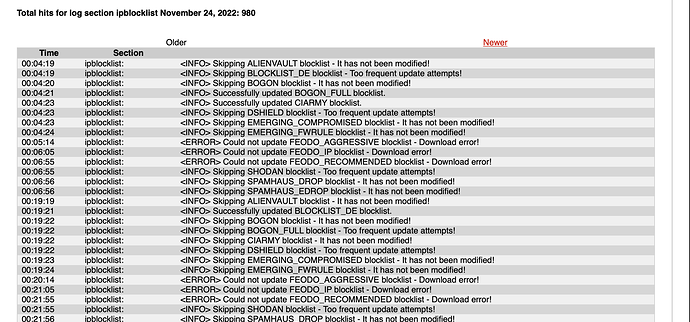
The computer connected to the https feodotracker immediately. The System log as before shows errors, and 800 hits.
If you are able to access the url via a browser then I don’t understand why it is not working with the IPFire code.
Those FEODO lists were all successfully downloaded for me when I tested them yesterday.
Just to check can you confirm that the urls for the three FEODO lists are as follows
FEODO Recommended - ‘url’ => ‘https://feodotracker.abuse.ch/downloads/ipblocklist_recommended.txt’,
FEODO IP - ‘url’ => ‘https://feodotracker.abuse.ch/downloads/ipblocklist.txt’,
FEODO Aggressive - ‘url’ => ‘https://feodotracker.abuse.ch/downloads/ipblocklist_aggressive.txt’,
These can be checked in the file /var/ipfire/ipblocklist/sources
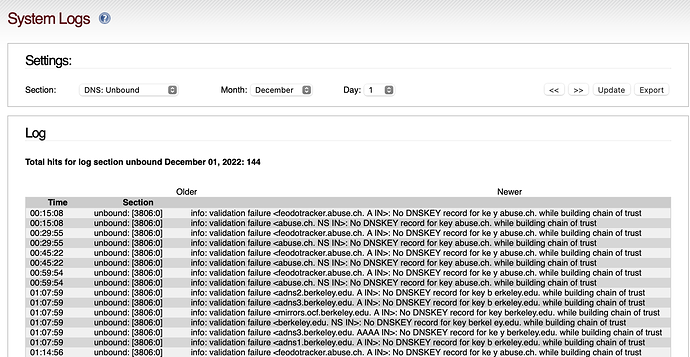
putting those three URLs into the browser connects. The next check is to remove the TLS configuration on the Fritz box. Additional the Firewall log is blank, The IPS Log is blank, URL Blacklist does update, And System Log DNS Unbound reports more than 50 failures:
info: validation failure <feodotracker.abuse.ch. A IN>: No DNSKEY record for ke y abuse.ch. while building chain of trust
00:27:12 unbound: [3840:0] info: validation failure <feodotracker.abuse.ch. A IN>: No DNSKEY record for ke y abuse.ch. while building chain of trust
00:42:10 unbound: [3840:0] info: validation failure <feodotracker.abuse.ch. A IN>: No DNSKEY record for ke y abuse.ch. while building chain of trust
openDNS was a DNS Server. After removing it, the pages connect from the IP Address Blocklists area of IPfire which they did not do aprior - though they connected from the browser.
See this wiki link that mentions issues with opendns
https://wiki.ipfire.org/dns/dnssec/hosted-blacklists
They are on the Not Recommended list in the wiki.
Actually I had read that but gave Iffier and OpenDNS a chance with v171! However, once again the Feodo are blocked. Turned Intrusion Protection off and Feodo connected (through IPFire). Turned the IP on and still Feodo connected. Conclusion: a fault in IPFire. As of now Feodo connects but the conclusion is Feodo will not connect tomorrow.
Turned Intrusion Protection off and Feodo connected
Did you check IPS logs and settings?
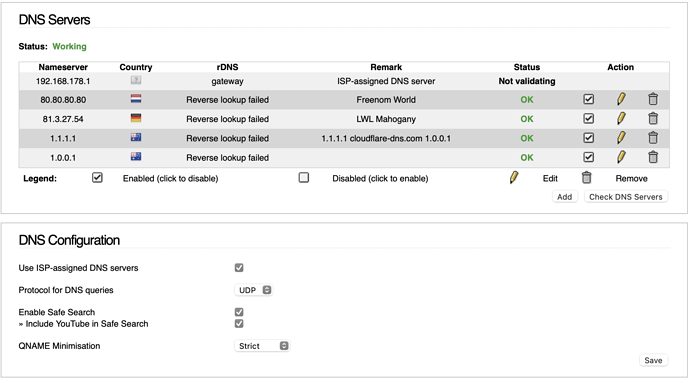
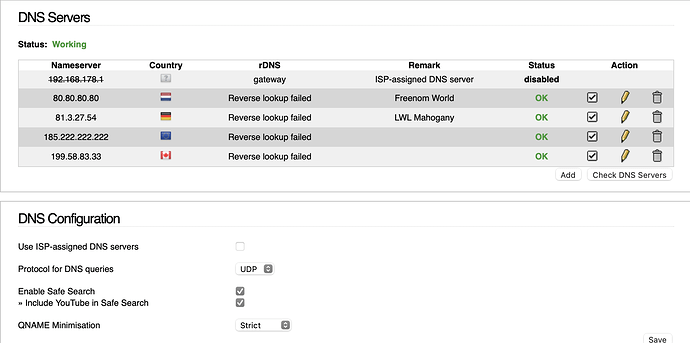
The log is empty and the settings normal. Turned off Strict DNSSEC and Feodo from IPFore connected. Will check again tomorrow. DNS Servers are
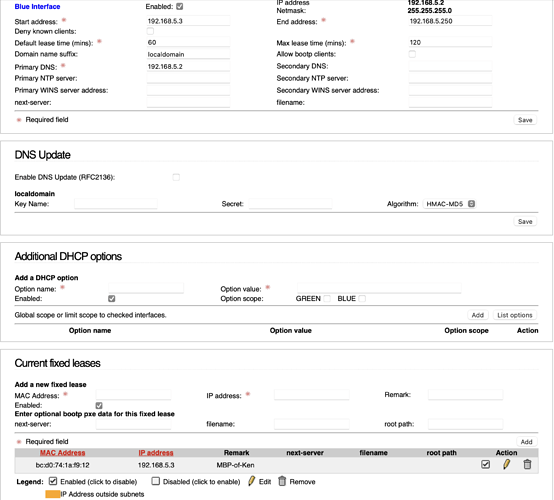
The next day. That did not work either. However the failure rate was 33 tries previously it was 90. Next try will remove all DNS server and let IPFire contact the ISP directly. That defeats the entire purpose. The image:
Do you mean IPFire’s blue IP?
It is element of the blue network 192.168.5.0/24! And not an element of the dynamic range for blue of the DHCP server, what is good!
Your BLUE network (192.168.5.0/24):
network address 192.168.5.0
broadcast address 192.168.5.255
IPFire address 192.168.5.2
DHCP dynamic pool {192.168.5.3 ... 192.168.5.250}
IPs for fixed leases {192.168.5.1, 192.168.5.251 ... 192.168.5.254}
‘not validating’ just means, that the DNS server doesn’t use DNSSEC.
See wiki.ipfire.org - List of Public DNS Servers ( bottom of page ) and wiki.ipfire.org - DNSSEC.
Also recommended Michaels blog article ( from 2020! ).