I’ trying to setup a wireguard Net2Net VPN. the first thing i notice is that the firewall blocks incoming requests.I have tried to create a firewall rule from Red to FW or to Wireguard peer but it didn’t make any difference.
Can somebody tell me what the firewall rule should be?
You must have an error in your n2n configuration then. I have set up a wireguard n2n with no additional firewall rules at all and it works fine. Mine is between two IPFire systems.
Any firewall rules required for the n2n wireguard tunnel to operate are automatically created by the IPFire code.
Is your n2n between two IPFire systems or is IPFire just at one end only?
If you can show a screenshot of your wireguard n2n configuration, with any privacy related things redacted.
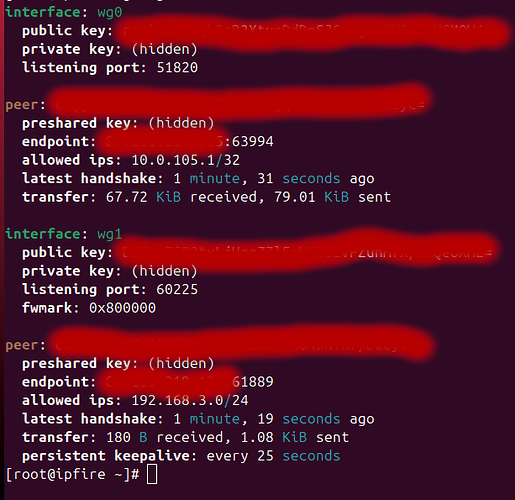
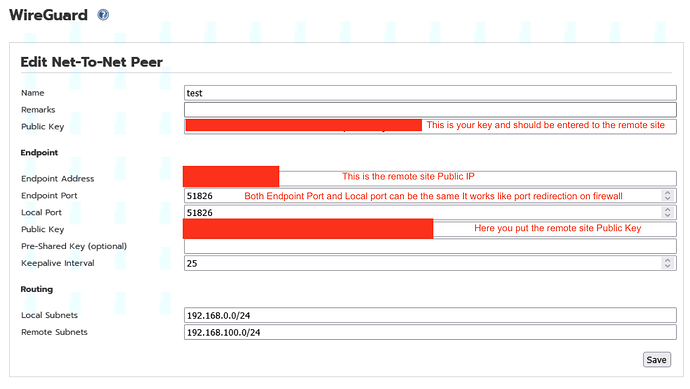
Here are the screenshots of the config.
THe remote Firewall is an OPNsense. I have several other WireGuard tunnels there with other routers and they work without issue.
What i dont understand is that on OPNsense you setup an Instance and a Peer along with firewall rules so that you allow traffic from the tunnel port to reach the system. Here there are no such settings.
The main thing I see is that you have the same port for both ends of the net2net tunnel.
I have a different port defined for the endpoint as for the local port.
You could have shown the local and remote subnets because those should be private address ranges anyway.
Those two subnets must not overlap.
As you are using OPNsense for the other end of the tunnel, I can’t help with what should be entered where. With my other IPFire end I imported the configuration that I created at the first end and it puts all the right bits into the right places.
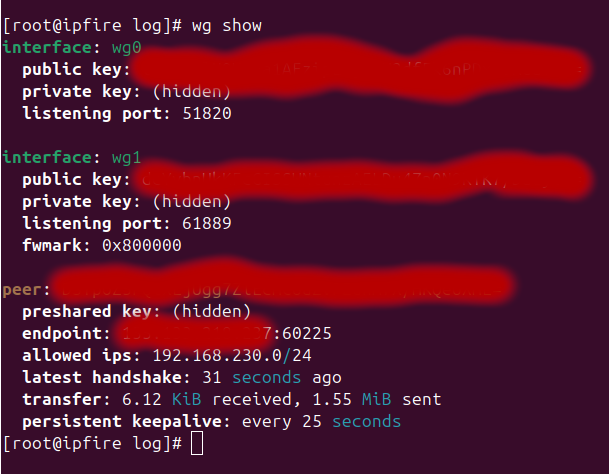
My other IPFire end has the following peer definition.
The Public Key at the top and in the Endpoint section for my skrymir system should be swapped around on your other end system.
because the firewall rules are defined by the code created by the IPFire devlopers so that you don’t have to worry about figuring out what firewall rules are needed.
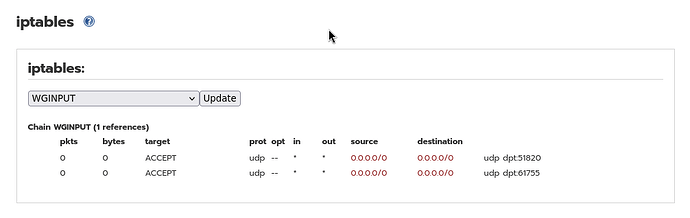
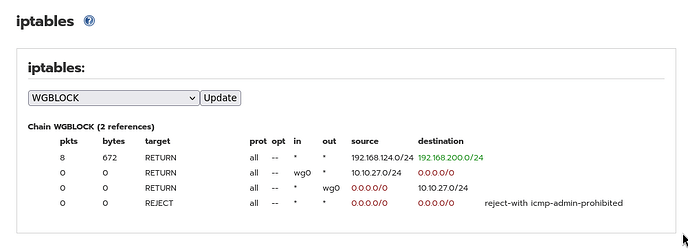
You can find out what rules have been defined by looking in the WUI menu Firewall - iptables and selecting WGBLOCK and WGINPUT in the iptables: section at the top and pressing the update button.
The equivalent will be required at the other end. As OPNsense doesn’t create the firewall rules for you, you will need to set up the equivalent versions on that system.
These are the two tables that I get from my vm testbed setup.
I have 2 ipfire: the Roadwarrior works both in the left network and in the right network with Wireguard without any problems. Adolf’s configurations are the same for me in terms of logic.
I just can’t get a Net2Net connection between the two networks, although the Adolf screens are identical in terms of logic. There are fixed public IP addresses on both sides. The IPtables are also identical - but there is no traffic to be seen. Both sites show connected in the WUI.
Where else can I look for my errors?
Can someone please help me? I have set up Wireguard net2net and both sides are connected. But I cannot route to the other network.
We have been using OpenVPN for the Net2Net connection.
OpenVPN was switched off on both sides for the test.
Wireguard shows connected on both sides.
Is there anything else to consider with a net2Net connection?
Zentrale:
Department:
Thanks
For anybody that is interested to setup wireguard with other system than iPfire, here is my setup that worked fine with OPNsense. On the front page of WireGuard section you have to check the “enable” option. This one here doesn’t work like roadwarriors on OPENvpn where you can uncheck the roadwarriors but the server keeps running. Here if you don’t check the enable option the whole WireGuard won’t come up.
When you first create the N2N peer on the Endpoint section it creates a public Key and a Pre-shared Key. Those you can overwrite with the ones from your Instance configuration on the OPNsense server.
I’ve just tried it and can’t get it to work either.I have just tried it and can’t get it to work either. I wanted to replace IPsec with Wireguard. In both Ipfires the connection is green, but there is no traffic over it.
@bonnietwin
The documentation is not very informative for this scenario, but did I do it right to create the config on Ipfire1 and import this config into Ipfire2?
A moment ago I did a test. I created a connection on IPFire1 and downloaded the configuration file.
On IPFire2, I imported the configuration file.
As a result, I was able to connect to a remote internal network ![]()
![]()
That’s exactly what I did, but it doesn’t work. I will try again today or tomorrow and delete the existing IPSec connection and not just deactivate it and restart both ipfires. Just a guess, but I believe that the internal routing is not deleted correctly if you only deactivate the IPSec connection.
With my first attempt I did it by taking the appropriate parts from one end and then editing them into the other end of the n2n.
Initially that did not work, if I remember correctly because I did not have WireGuard enabled on the main WUI page.
Unlike for OpenVPN where the RW server does not have to be enabled for n2n to work, with WireGuard, it needs to be enabled as the same WireGuard capability is used in both cases.
I did then do a repeat installation from scratch and using the import of the config file from the first end into the second end and that worked very easily for me.
I also had OpenVPN and IPSec enabled but using different subnets and with different endpoints.
I am not sure what happens if you have the same endpoint accessed by two or more VPN approaches coming from a single system.
I will look at doing some updates to the n2n Wireguard documentation when I can get some time.
I did some simple tests
1.I enabled IPsec, WireGuard connection between IPFire1 and IPFire2
2. then additionally from a computer in GREEN IPFire1 network I enabled WireGuard connection to IPFire2
In both tests I was able to connect to resources on the GREEN IPFire2 network.
![]()
Regards
Many thanks for the information! I also haphazardly generated the WG N2N twice on one side and imported it on the second side. Unfortunately this was not successful after switching off the openVPN N2N on both sides.
I will test this with new test hardware and report back.
I think that WG N2N cannot be operated in parallel to openVPN in an N2N constellation.
I agree that the documentation is still not quite perfect as far as the N2N WG VPN is concerned.
Since openVPN has been used on all our systems so far, it is not so easy to test on productive systems on WG N2N.
best regards
Addendum: Is there a way to completely delete the Wireguard N2N configuration in Releases 195 and start from scratch with an N2N WG Vpn?
If you have other protocols working between the two ipfires (ipsec for example) then it might be a problem of routing. What i would do, is to stop other protocols services on both ends and then create new configuration for wireguard.
Delete all client configurations in the WireGuard WUI page. That will take the peers file back to an empty state and you will be at the state of a scratch start.
I have now got it to work. I disabled the IPSec-N2N-Setup and completely disabled and re-enabled IPSec (on both sides). Then I created my WG-N2N and imported the config on the other and it worked immediately.
I think the important step here was to completely disable and re-enable IPSec once after disabled the setup so that the old routing is deleted. It will be the same with OpenVPN.
Hello to everyone who helped solve my problem.
We had been using openVPN with IpFire on both sites for years.
I did another test today and proceeded as follows.
-
deactivated the net2net connection on both sites and then stopped the openVPN server on both sites.
-
Set up a new Wiregard net2net connection on one side but did not activate it yet.
-
Loaded the WG config onto a USB stick and travelled to the other site and installed it there
-
then called someone on the other side who pressed ‘done’ and lo and behold the Net2Net tunnel is up and running. You can also route from A to B.
I was surprised that you can route a network segment like blue even after the fact.
A big thank you to the developers and supporters and I apologise if I was annoying because I didn’t understand the instructions properly.
Best regards Frank
Just for information
Notice.
The Net-to-Net connection works independently of the status (running|stopped) of the OpenVPN Server.