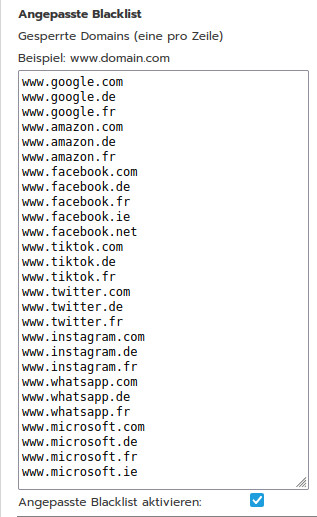
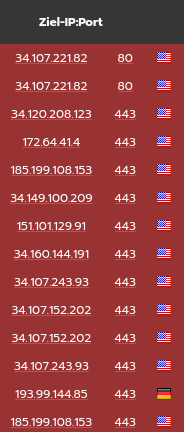
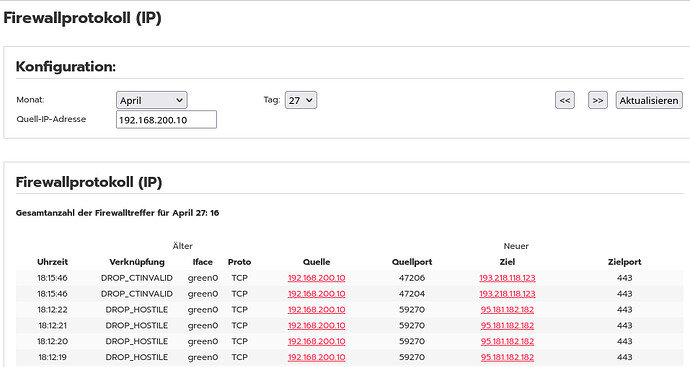
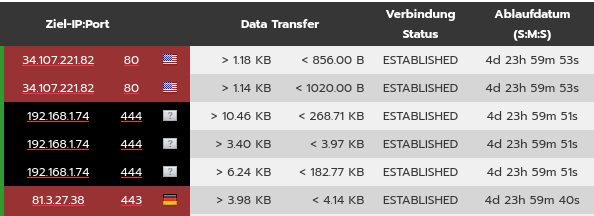
Thanks. Leave RUS/UKR outside - I just wanted to show that my log has no sign of Google.
Kyberio does not appear, either, in the firewall protocol…
“ESTABLISHED” now for more > 4 days - earlier that period was much shorter. But what does that term actually mean? Is it “captured” or put in custody?
Yes, G. is also a hoster - pityful enough. My issue is that sites like
welt.de are “fetching” external applications to grasp data with their help.
Even when I look into the source code, I can only find a few of them.
My understanding is that I = my firewall has no chance to block “Mother’s little helpers” because
they have coded them, so, their “ranking” is so
as if I would have “invited” them. However, I just wanted to surf on a URL - and had no intention to become a victim of their spy activities.
Thank you for the gorgeous list of URL-ranges.
No, I am not in the position to block “all” of them - even it I wanted to.
G is an evil, and I want to keep all of their “services” as far as possible from my PCs, laptops and hard disks. I use neither “smart” phones nor tablets because they are
not compatible with my “sausage” fingers and I would feel lost and entirely w/o any shield, shelter and protection.
“these will also be shown in the Firewall Logs as long as the logging for the involved rules was enabled. If not enabled then no information is shown in the logs.”
Yes, I strive at making use of all blocking possibilities IPF is offering, and I did see very few IPs “ending up” in the protocol. By why does G not appear there, despite of the fact that it has been “ESTABLISHED”?