Hello everyone,
I have always been very proud to see all ports on my IPFIRE firewall closed. External NMAP tests, the GRC Shields-Up logs, Shodan, etc. always showed all doors closed, beautifully.
A few days ago I received a notification that DNS port 53 (IPFIRE unbound) was open on the red network (!?). The people who manage the network infrastructure above my IP did some periodic scans and noticed that this port was open, and that it could be used as an open resolver (recursively) for third-party DNS attacks. Despite this notification, I did not notice anything wrong (in logs, graphs, whatsoever).
The notification worried me a lot, as I thought the firewall would have been hacked somehow, with some rootkit. But (I guess) this is not the case.
After better analysis, I noticed that both DNS port 53 and Virtual host HTTPD port 1013 (captive portal) were open and accepting connections from the red side! Nmap, Shodan, confirmed this. GRC Shields-Up curiously showed a lot of closed ports (blue dots on FTP, TELNET and other common ports), along with the stealth and the two open ports. This is very strange, since all ports were usually reported as stealth before.
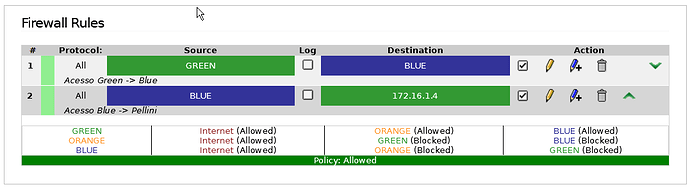
At this time I had only two firewall rules related to blue to green communications, and nothing else.
I don`t know what triggered this. As I recall, the only change I did on the IPFIRE was last month, when I tryed to enable the IPS service, but it apparently failed to go up. I did not further investigate what happened, and leaved the IPFIRE as it was, since everything else was working as usual.
I guess IPS service injected some iptables rules during the ‘enable’ process, but failed to accomplish the remaining configurations and quit. I don`t know how to deal with iptables, but I can get every info or log someone else may need, to help me understand what happened.
I saw previous posts on the community forum related to similar problems. But I still did not find the origin of the problem.
To solve the open red ports, I manually changed the unbound and httpd configuration to make the daemons listen to traffic only on the green and blue internal interfaces. It worked for know (all ports are stealth), but this is nasty.
I’m worried I would need to do a plain installation. And the importing of previous configuration backups may bring back all the misconfigured rules.
Any comment are greatly appreciated.
Pellini
PS: IPFIRE is running on a legacy 586