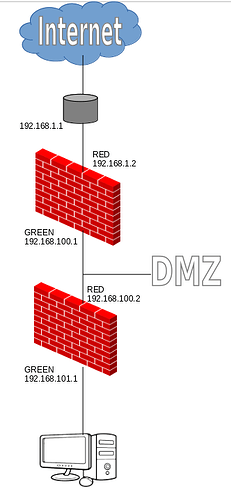
I want to connect from an external network to my LAN network located on the second firewall. I can access with VPN from external network to the first firewall (DMZ) or from the first firewall to the second firewall (LAN), but I can’t access from an external network to the second firewall (LAN). I have tried to do N2N and Roadwarrior but I can’t get it to work.
How many NAT do you do? Three?
Yes, I have 3 NAT’s
My head is spinning by the stratification of networks. Anyhow, this is what it comes to mind:
- IPFire1:
I assume OpenVPN is correctly installed here, - IPFire2:
Did you configure the necessary firewall rules on IPFire2 to allow incoming VPN traffic from IPFire1 to access Ipfire2-Green0? - Network Routing:
Maybe you need to establish a site-to-site VPN tunnel between IPFire1 and IPFire2 in order for a client from red0-IPFire1 to access IPFire2-Green0
In IPFire1 I have:
- OpenVPN Server N2N with IPFire1
- OpenVPN RoadWarrior
In IPFire2 I have: - OpenVPN Client N2N with IPFire2
Right now I can VPN connect with IPFire1 but not with IPFire2.
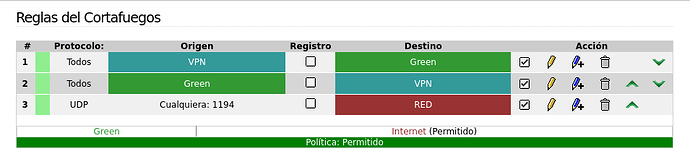
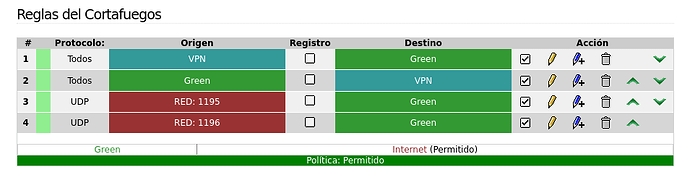
IPFire1 Firewall rules:
Let’s see if I understood: you have one OpenVPN-1 server running on IPFire1 and a second OpenVPN-2 server running on IPFire2, both servers have an N2N with each other; The road warriors of OpenVPN-1 coming from red0-IPFire1 can connect to IPFire-1 and access the DMZ (of IPFire1), but cannot access IPFIre2-green0. Did I get it?
In IPFire2 is client, not server, and is connected with IPFire1. The rest of message is fine.
Ok, I think you have a routing problem. You need to route the traffic from IPFire1-VPN to IPFire2-green0. From the point of view of IPFire1, it has no knowledge of the routing table of IPFire2. It cannot send anything specific to a host on IPFIre2-green0. It can only forward everything to its gateway, which is IPFire2. On the other side of the equation, IPFire 2 is receiving this traffic, what is supposed to do with that? You could DNAT, but where? That’s why the only solution (I can see) is to create a route from IPFire1 to IPFire2 with a second OpenVPN server on IPFire2 establishing an N2N Tunnel with OpenVPN-1.
EDIT: to clarify, with this setting properly configured you have something like this:
Network1 Network2
+------------+ +------------+
| | | |
| Road | | Road |
| Warrior | | Warrior |
| Client | | Client |
| | | |
+------+-----+ +-----+------+
| |
| tunnel1 (RW) | tunnel3 (RW)
| |
+------+-----+ +-----+------+
| | | |
| OpenVPN | Tunnel2 (N2N) | OpenVPN |
| Server +----------------------+ Server |
| (Network1) | | (Network2) |
| | | |
+------------+ +------------+
192.168.100.1 192.168.100.2
from boths sides of tunnel2, the clients (on one side using tunnel1, while on the other side using tunnel3) will be able to see each other. In other words, clients coming from the red interface of IPFire1 can see the OpenVPN-2 clients, but not IPFire2-green0.