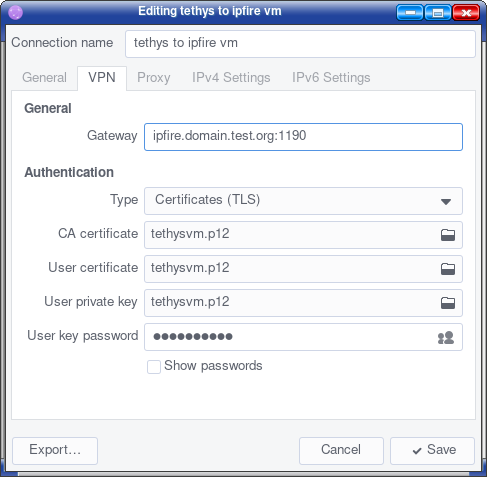
I have found the commands to run openvpn directly from the command line on your client and I have confirmed it by making a successful connection that showed up as CONNECTED in green on the IPFire OpenVPN status table.
First let’s confirm that you do have openvpn installed on your client.
Run the following command on your client
openvpn --version
you should see something similar to
OpenVPN 2.6.4 [git:makepkg/b4f749f14a8edc75+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO] built on May 11 2023
library versions: OpenSSL 3.0.8 7 Feb 2023, LZO 2.10
DCO version: N/A
Originally developed by James Yonan
Copyright (C) 2002-2023 OpenVPN Inc sales@openvpn.net
Compile time defines:
That shows that on my Arch Linux system OpenVPN-2.6.4 is installed.
If OpenVPN is not installed then you will just get a message that vthe command openvpn is not recognised.
Then extract all the files from your IPFire zip file into some location.
I used /etc/openvpn/client
Then you will need to edit the .ovpn file to add a path to the pkcs12 and tls-auth lines.
In my case I changed
pkcs12 tethysvm.p12
tls-auth ta.key
to
pkcs12 /etc/openvpn/client/tethysvm.p12
tls-auth /etc/openvpn/client/ta.key
Then run the following command
openvpn --config /etc/openvpn/client/your-ipfire-connection-file-name.ovpn
You may need to do this as sudo depending on the permissions in the directory that you have saved the files into. I had to use sudo for mine.
I then had the messages
2023-05-23 15:57:51 Note: Kernel support for ovpn-dco missing, disabling data channel offload.
2023-05-23 15:57:51 OpenVPN 2.6.4 [git:makepkg/b4f749f14a8edc75+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO] built on May 11 2023
2023-05-23 15:57:51 library versions: OpenSSL 3.0.8 7 Feb 2023, LZO 2.10
2023-05-23 15:57:51 DCO version: N/A
Enter Private Key Password: **********
I entered the password that I had entered when I set up the connection on the IPFire.
I then got a whole lot more messages which near the end included
2023-05-23 15:58:20 Initialization Sequence Completed
At that point when I looked at the IPFire OpenVPN server page that connection was showing as connected.