hi
Why if I activate log-destaddr and log-queries in unbound log i see udp 0.0.0.0 53
we shouldn’t see the ip of destination and the port ?
ty
0.0.0.0 port 53 is unbound listen.
Could you show us an example for such a message?
The clients should address the DNS server directly, with the IP address of your IPFire system.
What is the source address of those packets?
You have added two extra entries into your unbound configuration (hopefully via a conf file in /etc/unbound/local.d/somename.conf)
and the unbound.conf man entry for log-destaddr says
log-destaddr: (yes or no)
Prints the destination address, port and type in the log-replies output. This disambiguates what type of traffic, eg. UDP or TCP, and to what local port the traffic was sent to.
Default: no
which tells you that you will now get log messages that have the destination address (IP), port and type.
and for log-queries it says
log-queries: (yes or no)
Prints one line per query to the log, with the log timestamp and IP address, name, type and class. Note that it takes time to print these lines which makes the server (significantly) slower. Odd (nonprintable) characters in names are printed as ‘?’.
Default: no
I’m looking to display the domains and their ip port in a log table.
I thought it was possible with log-destaddr and log-queries in unbound
the believe that it would be possible with
Resolve a Name
ty
That link you provide shows a basic c program to resolve a name but it requires both unbound and ldns to be installed. ldns is not installed in IPFire.
Was your aim to take the data from the unbound log with the addition of those two logging functions and feed it into a program that uses the principles in that basic example?
Note that at the end of that page it says that the basic program does not have any security checks implemented for dealing with untrusted data, that would need to be separately added.
I just noticed that there are 5 more example programs and the third one does give an example of supplying the url to the program on the command line so that could be used as a starting point to create a program.
If you are looking to log all the DNS queries that the users are making on your network, then those two additional log configs will provide that, from what I have found in my searching but I think you might have to also increase the verbosity value in your local.conf unbound file. IPFire does not specify the verbosity so it is at the default value of 1 which from the man file means
verbosity: (number)
The verbosity level.Level 0
No verbosity, only errors.Level 1
Gives operational information.Level 2
Gives detailed operational information including short information per query.Level 3
Gives query level information, output per query.Level 4
Gives algorithm level information.Level 5
Logs client identification for cache misses.The verbosity can also be increased from the command line and during run time via remote control. See unbound(8) and unbound-control(8) respectively.
Default: 1
I suspect you would need to have Verbosity at level 2 or 3 to get the information you want.
The higher the verbosity level the more info provided per query to the logs and the quicker the logs will grow.
The verbosity level
Thank you for your help I’ll test this.
I tested all the verbositer levels of its not giving the ip domains.
I tried to make the kernel lines with the lines of unbound But these complicate to fall just
ty
What do want to achieve?
With your log-.... settings I can see the queries and responses. First field is the requesting client IP, the URL to resolve is also contained in the logs.
The end of the log-replies messages is ‘on 0.0.0.0 53’, which means it is sent on the standard port to the default network.
If I interpret your list right, it lists requests of the proxy ( Squid ). The domains are generated by rDNS ( unbound ) (?).
You do not need a log analysis for this, IMO.
I don’t use squid for this log.
I’d like to use that unbound to solve domain ip if possible.
would allow them to know as in the log of squid them ip contact but without squid
dhcp logs would show some of it, but not names in the hosts file,
and the arp command shows the whole DNS map
For looking at dhcp logs, you would use this:
cat /var/log/messages | grep -Ei 'dhcpd: execute_statement'
I tried the command in a terminal but it doesn’t display the ip of domains.
appearly unbound cannot display the ip of domains it does not do rdns
domain + ip would be displayed when:
arp -a command is ran at the ssh or at the terminal on the IPFire server.
Unbound is just a sever process and not a command invoked on the command line.
rdns is handled a few ways on Linux depending on the connection.
Thank you for the explication.
if I want to display the ip of domains in the log how to do it correctly?
have an example of a code that I can integrate it into the log code?
ty
Perhaps a tcpdump command could give you the result you’re looking for.
For example
tcpdump -i green0 -v src port 53 or src port 853
Configure according to your needs.
But this can’t be used continuously if there are many users on your network.
I don’t think there is a log file like that were all of that info is in one log file.
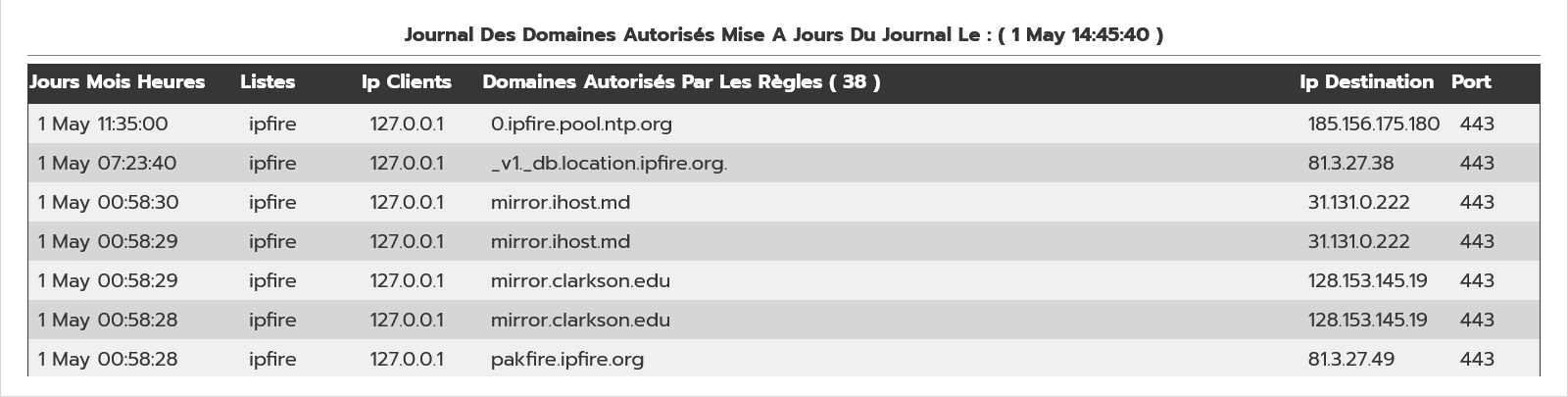
to do it I test the two-lined dropup.
open(my $fh4, '<', '/var/log/messages') or die "Impossible d'ouvrir le fichier: $!";
my @linepassthru = ();
while (my $line = <$fh4>) {
if ($line =~ /rpz-passthru/) {
# Supprimer les crochets "["
$line =~ s/\[|\]//g;
# Supprimer "@\d+" (suivi d'un nombre)
$line =~ s/@\d+//;
# Supprimer les types de requêtes DNS
$line =~ s/. A IN|. HTTPS IN|. AAAA IN//g;
# Séparer les informations dans une liste
my @parts = split /\s+/, $line;
while (my $line2 = <$fh4>) {
if ($line2 =~ /kernel: .+DST=(\S+).+DPT=(\S+)/) {
chomp($line2);
# Séparer les informations dans une liste
my @parts2 = split /\s+/, $line2;
my $dst = $1;
my $dpt = $2;
push @linepassthru, <<END;
<tr>
<td>$parts[1] $parts[0] $parts[2]</td>
<td><div style="max-width: 100px; word-wrap: break-word; overflow: hidden; text-overflow: ellipsis;">$parts[9]</div></td>
<td>$parts[12]</td>
<td><div style="max-width: 400px; word-wrap: break-word; overflow: hidden; text-overflow: ellipsis;">$parts[13]</div></td>
<td>$dst</td>
<td>$dpt</td>
</tr>
END
;
last;
}
}
}
}
@linepassthru = reverse @linepassthru;
foreach my $line (@linepassthru) {
print $line;
}
print <<END;
</table>
</div>
</script>
END
;
close($fh4);
may lack treatment lines
This code assumes, you use the RPZ addon by @jon.
This isn’t standard functionality of unbound in IPFire, yet.