Hi All,
Running IPFire 2.29 (x86_64) - Core-Update 184 here as an internal network.
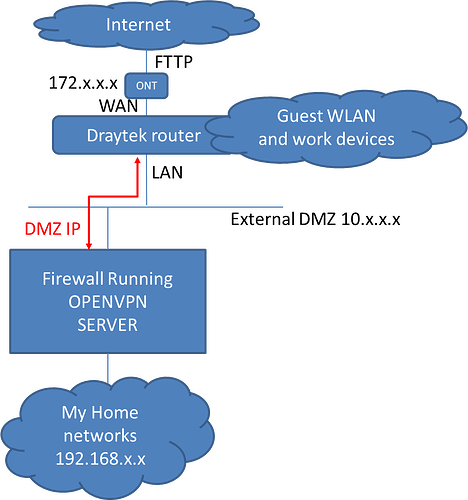
the high level setup is depicted below:
We cutover from legacy DOCSIS cable last week to Direct Fibre. The new ISP router was seriously AWFUL! so we replaced it with a Draytek which seems to have fixed all of the immediate problems like the DMZ not working in the ISP provided router.
I noticed that UDP traffic from green to red was working for several services, but not for 2 others.
Tcpdump’ing red I could see the traffic outbound but the issue didn’t dawn on me at the time as in my mind, I was still inside the firewall and before iptables but with hindsight it should have been obvious (my bad).
For the one service, I contacted the server owner who said nothing but mysteriously 10 minutes later everything started working again there so I suspect the problem was their end…
But I couldn’t initially resolve the second one.
I enabled a monitor port on the draytek and fired up wireshark.on a laptop connected directly to that draytek monitor port
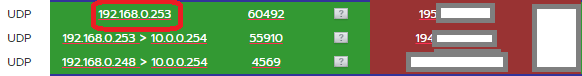
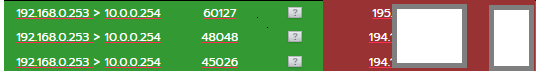
To my surprise, I saw 192.168 traffic being pushed from green out into the red subnet without NATing - but only for this one service…
The upstream Draytek behaved correctly and dropped the traffic as the source IP was not in the 10.x.x.x network
I rebooted IPFire and the problem went away, so I dont believe it to be repeatable without multiple reboots /swapouts of the ISP router.
I can only conclude that this is a feature / bug in IPfire ?
Anyone seen this before?
if so , is there a workaround to prevent it occurring again please ?
Regards
“The relieved to have found it but perplexed that it happened”
BB