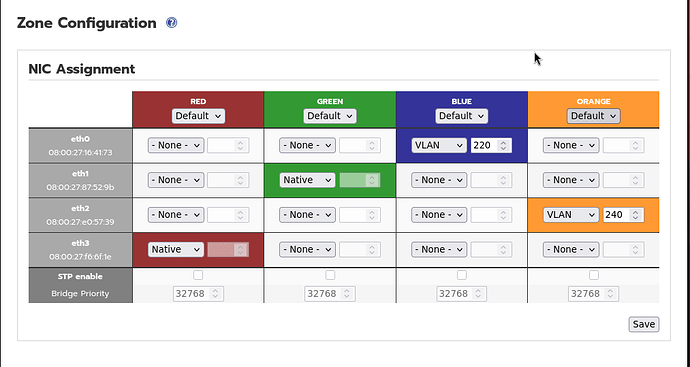
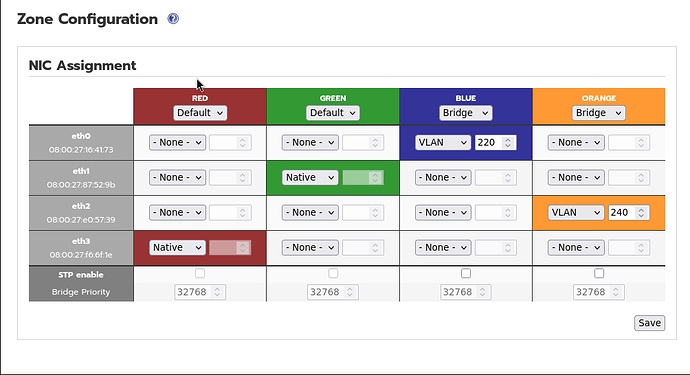
The normal way that vlans are set on IPFire is via the WUI menu Network - Zone Configuration.
Here is an example with the blue and orange networks set with a vlan id.
The settings for this page are defined in the file
/var/ipfire/ethernet/vlans
and these give the following vlan configurations
2: red0: <BROADCAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:f6:6f:1e brd ff:ff:ff:ff:ff:ff
inet 192.168.26.200/24 brd 192.168.26.255 scope global dynamic noprefixroute red0
valid_lft 863933sec preferred_lft 755933sec
3: green0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:87:52:9b brd ff:ff:ff:ff:ff:ff
inet 192.168.200.254/24 scope global green0
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:16:41:73 brd ff:ff:ff:ff:ff:ff
5: eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:e0:57:39 brd ff:ff:ff:ff:ff:ff
6: blue0@eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 02:04:b5:7c:bc:3c brd ff:ff:ff:ff:ff:ff
inet 192.168.220.254/24 scope global blue0
valid_lft forever preferred_lft forever
7: orange0@eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 02:4f:3e:0d:12:1f brd ff:ff:ff:ff:ff:ff
inet 192.168.240.254/24 scope global orange0
valid_lft forever preferred_lft forever
As your vlan settings have the syntax of blue0px and the syntax for IPFire should be blue0@ethx it looks like your technician set up those vlans via the command line in a different way to how IPFire would do it. To understand what he did and why your best bet would be to ask the tech to explain it.
As the tech set things up via the command line which is not how things are set up in IPFire, which uses the WUI menu system, you also need to be careful not to change and save anything on that WUI Zone Configuration menu otherwise it could end up changing your existing setup as it is configured in a different way to the normal IPFire way of defining vlans.
You need to be careful not to create a hole that ends up bypassing the firewall protection.
It needs to be remembered that IPFire is not a firewall setup on top of some existing Operating System. IPFire is its own OS/Distribution and it has been configured and setup to meet the requirements of the IPFire firewall system.