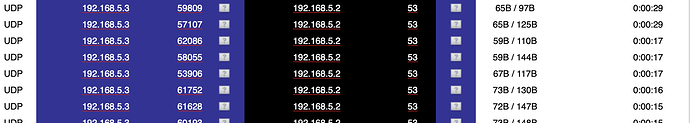
TLS works. Why countless UDP 53 Requests?
SAMPLE
I’m not sure I understand… Why is that bad? (I see the same thing on my WebGUI connections page)
This are normal (non tls) requests from a client in your blue network the unbound of the IPFire. The unbound will resolve it via tls and answer it.
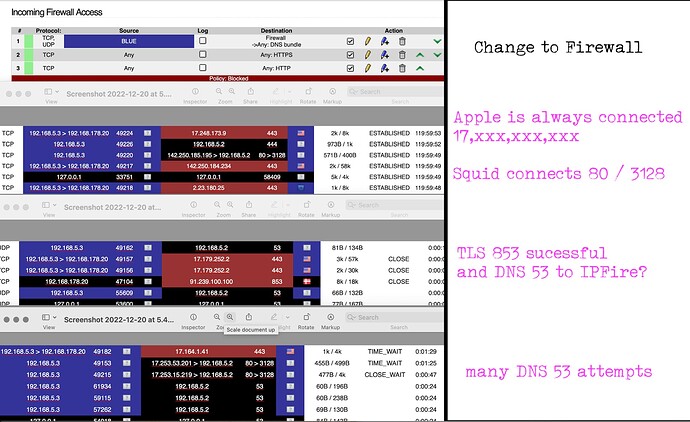
Jon. The idea extends the Hardening the Firewall quest. That is, as TLS uses 853 what function or feature is using 53? Could the use of 53 category be a Leak or revealing some information: just because a DNS 853 is encrypted what good is that if the request is also sent out DNS 53? At least I hope that clears the inquiry.
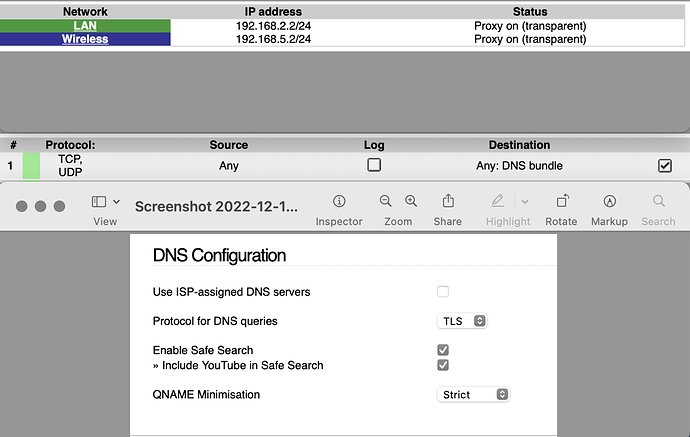
Understands that your IPFire, DNS configuration is set to TLS
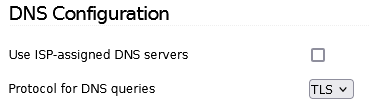
What DNS is the host 192.168.5.3 set to?
You have configured unbound to use TLS for the requests that go outside. But your internal client use normal DNS to ask the unbound on the IPFire.
That Host is the Blue Wireless. All connections are routed through TLS and DNS bundle is TCP, UDP and TLS.
That is what I read, would explain the 53. And the internal client BLACK can only work with 53?
This is not true.
Your clients would need be set to use DOT
The question is best directed at the notion of privacy. That is, does the UDP53 connection reveal information to the outside since IPFire is configured TLS, to limit unnecessary chatter.
If you are using TLS with unbound then your DNS queries out to the internet are encrypted. The UDP traffic is only on your green lan and into unbound on the green0 interface.
If all people accessing computers on your green lan are trusted then privacy won’t be a problem. If you have untrusted people accessing computers on your green lan then you may have a problem.
I am not 100% certain but I believe that the way that unbound is set up in IPFire means that you can’t use TLS communication to it from your green lan clients.
Hopefully someone else more knowledgeable on how unbound is set up can comment on this.
TLS is checked. Green is available but only Blue wireless is used. That means Unbound is used all the time because Green is not accessed. Is it correct that Unbound is not accessing Squid Proxy?
If in the Blue section of the dhcp page you have entered the IPFire blue ip address or the IPFire green ip address into the Primary DNS: entry then all the clients will get told to use the IPFire DNS server (unbound) via the dhcp communication to them.
As long as the clients using the blue lan accept and use that dns address then your blue clients will use the IPFire Unbound as their DNS source.
If your blue clients ignore the dns information provided by dhcp, as many mobile clients do, then you will need to follow the wiki page about forcing clients to use the IPFire DNS AServer
https://wiki.ipfire.org/configuration/firewall/dns
The squid proxy is a web proxy which is used to support web browsing activities, not DNS server activities. Squid proxy is used to cache content to reduce bandwidth and load web pages more quickly.
Ive made that change for a Test. Which Log will validate its effectiveness? Regarding the DHCP interface the primary DNS remains the same = 192.168.5.2 and start address remains the same = 192.168.5.3.