@hvacguy
Hi Shaun,
this is already done automatically while hitting Save.
I’ll just add a few screenshots to demonstrate:
- The patched
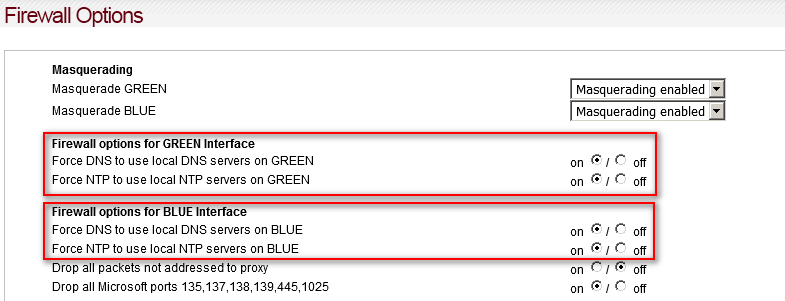
optionsfw.cgilooks like this. I added DNS, NTP-switches. And: options for BLUE are only shown if BLUE exists:
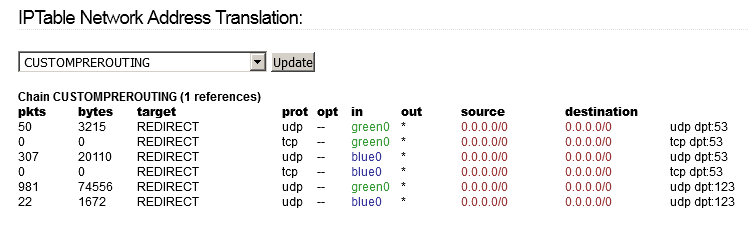
- These switches (should!) add a few REDIRECT rules - or delete them, if they exist - in the CUSTOMPREROUTING chain:
- The adding - or deleting - of these rules has to be done with the command
/etc/rc.d/init.d/firewall restart- and I like to trigger this through an addedSave and Restartbutton at the end ofoptionsfw.cgi:
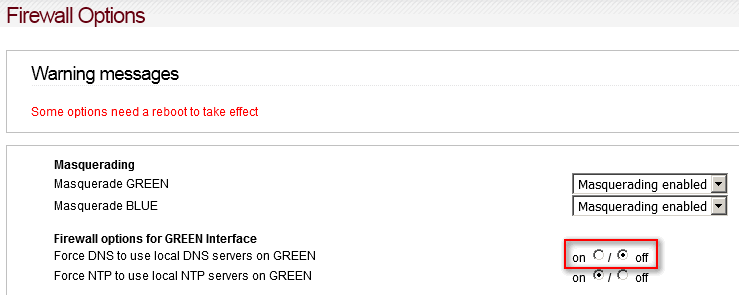
So when hitting Save not only the page settings are saved - as before - but additionally the firewall settings should be restarted “for changes to take effect”…
And because its the same procedure as before - plus a “few” tuning measures - the usual message appears after choosing Save And Restart:
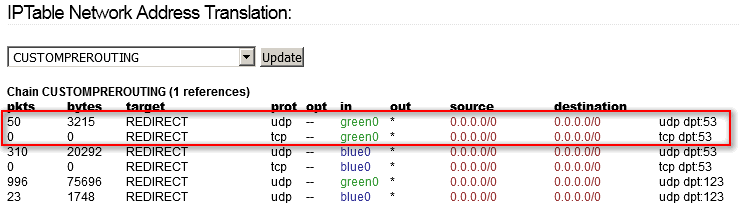
Note that I changed the Force DNS on GREEN option.
But the CUSTOMPREROUTING chain isn’t changed, the rules for GREEN are still there:
And I’d like to avoid a complete reboot…
Doing exactly the same through a root console with executing /usr/local/bin/optionsfwctrl restart - a newly added program - works.