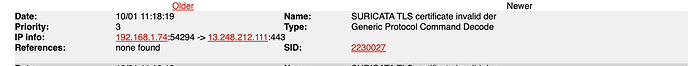
After a fresh install of IPFire 2.27 (x86_64) - core179 and following a restore, I have noticed my IPS log is flooded with the following message
Googling the error it appears to be related to a Suricata issue
Is there a way around this at them moment other than disable IPS on RED interface ?
=====
11:18:14 suricata: rule reload complete
11:18:14 suricata: cleaning up signature grouping structure... complete
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.PS.Download' is checked but not se t. Checked in 2032169 and 3 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.bit.do.shortener' is checked but n ot set. Checked in 2029550 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'http.dottedquadhost' is checked but n ot set. Checked in 2021076 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.JavaArchiveOrClass' is checked but not set. Checked in 2017768 and 9 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.http.PK' is checked but not set. C hecked in 2019835 and 3 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'min.gethttp' is checked but not set. Checked in 2023711 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.autoit.ua' is checked but not set. Checked in 2019165 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.Socks5.OnionReq' is checked but no t set. Checked in 2027704 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.smb.binary' is checked but not set . Checked in 2027402 and 4 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.armwget' is checked but not set. C hecked in 2024241 and 1 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.WinHttpRequest.no.exe.request' is checked but not set. Checked in 2022653 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MCOFF' is checked but not set. Che cked in 2019837 and 1 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.XMLHTTP.no.exe.request' is chec ked but not set. Checked in 2022053 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.XMLHTTP.ip.request' is checked but not set. Checked in 2022050 and 1 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.wininet.UA' is checked but not set . Checked in 2021312 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.MSSQL' is checked but not set. Che cked in 2020569 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.ELFDownload' is checked but not se t. Checked in 2019896 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.http.javaclient.vulnerable' is che cked but not set. Checked in 2013036 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'is_proto_irc' is checked but not set. Checked in 2002029 and 4 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'exe.no.referer' is checked but not se t. Checked in 2020500 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'HTTP.UncompressedFlash' is checked bu t not set. Checked in 2018428 and 1 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.WinHttpRequest' is checked but not set. Checked in 2019823 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'dcerpc.rpcnetlogon' is checked but no t set. Checked in 2030870 and 6 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.gocd.auth' is checked but not set. Checked in 2034333 and 0 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.IE7.NoRef.NoCookie' is checked but not set. Checked in 2023671 and 9 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.http.javaclient' is checked but no t set. Checked in 2017181 and 11 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.pdf.in.http' is checked but not se t. Checked in 2017150 and 3 other sigs
11:18:01 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.JS.Obfus.Func' is checked but not set. Checked in 2017247 and 0 other sigs
11:18:01 suricata: 28526 signatures processed. 1054 are IP-only rules, 4901 are inspecting packet p ayload, 22367 inspect application layer, 108 are decoder event only
11:18:00 suricata: Threshold config parsed: 0 rule(s) found
11:18:00 suricata: 48 rule files processed. 28526 rules successfully loaded, 114 rules failed
11:17:55 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop tls $EXT ERNAL_NET any -> $HOME_NET any (msg:"ET JA3 HASH - Possible RustyBuer Server Res ponse"; flowbits:isset,ET.rustybuer; ja3s.hash; content:"f6dfdd25d1522e4e1c7cd09 bd37ce619"; reference:md5,ea98a9d6ca6f5b2a0820303a1d327593; classtype:bad-unknow n; sid:2032960; rev:1; metadata:attack_target Client_Endpoint, created_at 2021_0 5_13, deployment Perimeter, former_category JA3, malware_family RustyBuer, perfo rmance_impact Low, signature_severity Major, updated_at 2021_05_13;)" from file /var/lib/suricata/emerging-ja3.rules at line 245
11:17:55 suricata: [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3(s) support is not enabled
11:17:55 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "alert tls $HO ME_NET any -> $EXTERNAL_NET any (msg:"ET JA3 Hash - Suspected Cobalt Strike Mall eable C2 M1 (set)"; flow:established,to_server; ja3.hash; content:"eb88d0b3e1961 a0562f006e5ce2a0b87"; ja3.string; content:"771,49192-49191-49172-49171"; flowbit s:set,ET.cobaltstrike.ja3; flowbits:noalert; classtype:command-and-control; sid: 2028831; rev:1; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_B it, attack_target Client_Endpoint, created_at 2019_10_15, deployment Perimeter, former_category JA3, malware_family Cobalt_Strike, signature_severity Major, upd ated_at 2019_10_15, mitre_tactic_id TA0011, mitre_tactic_name Command_And_Contro l, mitre_technique_id T1001, mitre_technique_name Data_Obfuscation;)" from file /var/lib/suricata/emerging-ja3.rules at line 41
11:17:55 suricata: [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3 support is not enabled
11:17:54 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop udp ![$S MTP_SERVERS,$DNS_SERVERS] any -> $DNS_SERVERS 53 (msg:"ET DNS DNS Lookup for loc alhost.DOMAIN.TLD"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|09|localhost"; fast_pattern; nocase; cl asstype:bad-unknown; sid:2011802; rev:6; metadata:created_at 2010_10_13, updated _at 2019_09_03;)" from file /var/lib/suricata/emerging-dns.rules at line 91
11:17:54 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - Complete IP space negated. Rule addres s range is NIL. Probably have a !any or an address range that supplies a NULL ad dress range
11:17:35 suricata: Including configuration file /var/ipfire/suricata/suricata-used-rulesfiles.yaml.
11:17:35 suricata: Including configuration file /var/ipfire/suricata/suricata-http-ports.yaml.
11:17:35 suricata: Including configuration file /var/ipfire/suricata/suricata-dns-servers.yaml.
11:17:35 suricata: Including configuration file /var/ipfire/suricata/suricata-homenet.yaml.
11:17:35 suricata: rule reload starting
11:17:35 suricata: Signature(s) loaded, Detect thread(s) activated.
11:17:35 suricata: rule reload complete
11:17:35 suricata: cleaning up signature grouping structure... complete
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.PS.Download' is checked but not se t. Checked in 2032169 and 3 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.bit.do.shortener' is checked but n ot set. Checked in 2029550 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'http.dottedquadhost' is checked but n ot set. Checked in 2021076 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.JavaArchiveOrClass' is checked but not set. Checked in 2017768 and 9 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.http.PK' is checked but not set. C hecked in 2019835 and 3 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'min.gethttp' is checked but not set. Checked in 2023711 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.autoit.ua' is checked but not set. Checked in 2019165 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.Socks5.OnionReq' is checked but no t set. Checked in 2027704 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.smb.binary' is checked but not set . Checked in 2027402 and 4 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.armwget' is checked but not set. C hecked in 2024241 and 1 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.WinHttpRequest.no.exe.request' is checked but not set. Checked in 2022653 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MCOFF' is checked but not set. Che cked in 2019837 and 1 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.XMLHTTP.no.exe.request' is chec ked but not set. Checked in 2022053 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.MS.XMLHTTP.ip.request' is checked but not set. Checked in 2022050 and 1 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.wininet.UA' is checked but not set . Checked in 2021312 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.MSSQL' is checked but not set. Che cked in 2020569 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.ELFDownload' is checked but not se t. Checked in 2019896 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.http.javaclient.vulnerable' is che cked but not set. Checked in 2013036 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'is_proto_irc' is checked but not set. Checked in 2002029 and 4 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'exe.no.referer' is checked but not se t. Checked in 2020500 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'HTTP.UncompressedFlash' is checked bu t not set. Checked in 2018428 and 1 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.WinHttpRequest' is checked but not set. Checked in 2019823 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'dcerpc.rpcnetlogon' is checked but no t set. Checked in 2030870 and 6 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.gocd.auth' is checked but not set. Checked in 2034333 and 0 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.IE7.NoRef.NoCookie' is checked but not set. Checked in 2023671 and 9 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.http.javaclient' is checked but no t set. Checked in 2017181 and 11 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.pdf.in.http' is checked but not se t. Checked in 2017150 and 3 other sigs
11:17:00 suricata: [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.JS.Obfus.Func' is checked but not set. Checked in 2017247 and 0 other sigs
11:17:00 suricata: 28526 signatures processed. 1054 are IP-only rules, 4901 are inspecting packet p ayload, 22367 inspect application layer, 108 are decoder event only
11:16:59 suricata: Threshold config parsed: 0 rule(s) found
11:16:59 suricata: 48 rule files processed. 28526 rules successfully loaded, 114 rules failed
11:16:55 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop tls $EXT ERNAL_NET any -> $HOME_NET any (msg:"ET JA3 HASH - Possible RustyBuer Server Res ponse"; flowbits:isset,ET.rustybuer; ja3s.hash; content:"f6dfdd25d1522e4e1c7cd09 bd37ce619"; reference:md5,ea98a9d6ca6f5b2a0820303a1d327593; classtype:bad-unknow n; sid:2032960; rev:1; metadata:attack_target Client_Endpoint, created_at 2021_0 5_13, deployment Perimeter, former_category JA3, malware_family RustyBuer, perfo rmance_impact Low, signature_severity Major, updated_at 2021_05_13;)" from file /var/lib/suricata/emerging-ja3.rules at line 245
11:16:55 suricata: [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3(s) support is not enabled
11:16:55 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "alert tls $HO ME_NET any -> $EXTERNAL_NET any (msg:"ET JA3 Hash - Suspected Cobalt Strike Mall eable C2 M1 (set)"; flow:established,to_server; ja3.hash; content:"eb88d0b3e1961 a0562f006e5ce2a0b87"; ja3.string; content:"771,49192-49191-49172-49171"; flowbit s:set,ET.cobaltstrike.ja3; flowbits:noalert; classtype:command-and-control; sid: 2028831; rev:1; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_B it, attack_target Client_Endpoint, created_at 2019_10_15, deployment Perimeter, former_category JA3, malware_family Cobalt_Strike, signature_severity Major, upd ated_at 2019_10_15, mitre_tactic_id TA0011, mitre_tactic_name Command_And_Contro l, mitre_technique_id T1001, mitre_technique_name Data_Obfuscation;)" from file /var/lib/suricata/emerging-ja3.rules at line 41
11:16:55 suricata: [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3 support is not enabled
11:16:54 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop udp ![$S MTP_SERVERS,$DNS_SERVERS] any -> $DNS_SERVERS 53 (msg:"ET DNS DNS Lookup for loc alhost.DOMAIN.TLD"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|09|localhost"; fast_pattern; nocase; cl asstype:bad-unknown; sid:2011802; rev:6; metadata:created_at 2010_10_13, updated _at 2019_09_03;)" from file /var/lib/suricata/emerging-dns.rules at line 91
11:16:54 suricata: [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - Complete IP space negated. Rule addres s range is NIL. Probably have a !any or an address range that supplies a NULL ad dress range
11:16:39 suricata: Including configuration file /var/ipfire/suricata/suricata-used-rulesfiles.yaml.
11:16:39 suricata: Including configuration file /var/ipfire/suricata/suricata-http-ports.yaml.
11:16:39 suricata: Including configuration file /var/ipfire/suricata/suricata-dns-servers.yaml.
11:16:39 suricata: Including configuration file /var/ipfire/suricata/suricata-homenet.yaml.
11:16:39 suricata: rule reload starting
11:16:39 suricata: all 4 packet processing threads, 2 management threads initialized, engine starte d.
11:16:39 suricata: fail-open mode should be set on queue
11:16:39 suricata: setting nfnl bufsize to 6144000
11:16:39 suricata: setting queue length to 4096
11:16:39 suricata: binding this thread 3 to queue '3'
11:16:39 suricata: fail-open mode should be set on queue
11:16:39 suricata: setting nfnl bufsize to 6144000
11:16:39 suricata: setting queue length to 4096
11:16:39 suricata: binding this thread 2 to queue '2'
11:16:39 suricata: fail-open mode should be set on queue
11:16:39 suricata: setting nfnl bufsize to 6144000
11:16:39 suricata: setting queue length to 4096
11:16:39 suricata: binding this thread 1 to queue '1'
11:16:39 suricata: fail-open mode should be set on queue
11:16:39 suricata: setting nfnl bufsize to 6144000
11:16:39 suricata: setting queue length to 4096
11:16:39 suricata: binding this thread 0 to queue '0'
11:16:39 suricata: Packets will start being processed before signatures are active.
11:16:39 suricata: fast output device (regular) initialized: fast.log
11:16:39 suricata: dropped the caps for main thread
11:16:39 suricata: NFQ running in REPEAT mode with mark 2147483648/2147483648
11:16:39 suricata: Enabling fail-open on queue
11:16:39 suricata: HTTP memcap: 268435456
11:16:39 suricata: CPUs/cores online: 4
11:16:39 suricata: This is Suricata version 6.0.13 RELEASE running in SYSTEM mode
11:16:39 suricata: Signal Received. Stopping engine.
11:16:39 suricata: Signature(s) loaded, Detect thread(s) activated