Hi,
I found the thread here and as I have the same issue and theres no real solution I want to discuss this again.
To try to block it I set an input drop rule for port 22 on red.
- What does your IPFire setup look like (if possible, draw a simple diagram of it)?
The IPFire is a mini pc with 4 LAN ports located between the internet router on red and two subnets (green - the internal server network and blue (wifi and ethernet clients bridged over 2 ports))
- How is IPFire’s RED interface connected to the internet?
It’s a Fritzbox which forwards all ports to IPFire (Exposed Host)
- Which IPFire version are you running on?
Installed Core 185, Imported our template config and updated to Core 186.
- Are there any 3rd party scripts or modifications to IPFire in place? If so, which ones?
No, there aren’t.
- What (vulnerability) scanner did you use to spot the issue? What did it display precisely?
I simply tried to connect port 22 of the public IP and succeeded.
- On IPFire, what is the output of
iptables -L -n -v?
I cropped some parts (forward/output/empty chains) to not reach the post limit.
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 IPSBYPASS 0 -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0xc0000000/0xc0000000
65579 21M BADTCP 6 -- * * 0.0.0.0/0 0.0.0.0/0
75573 22M CUSTOMINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
75573 22M HOSTILE 0 -- * * 0.0.0.0/0 0.0.0.0/0
70474 21M BLOCKLISTIN !1 -- * * 0.0.0.0/0 0.0.0.0/0
72235 22M GUARDIAN 0 -- * * 0.0.0.0/0 0.0.0.0/0
0 0 OVPNBLOCK 0 -- tun+ * 0.0.0.0/0 0.0.0.0/0
72235 22M IPS_INPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xc0000000
23623 2839K IPTVINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
23623 2839K ICMPINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
23623 2839K LOOPBACK 0 -- * * 0.0.0.0/0 0.0.0.0/0
17695 2393K CAPTIVE_PORTAL 0 -- * * 0.0.0.0/0 0.0.0.0/0
17695 2393K CONNTRACK 0 -- * * 0.0.0.0/0 0.0.0.0/0
1310 134K DHCPGREENINPUT 0 -- green0 * 0.0.0.0/0 0.0.0.0/0
4037 263K DHCPBLUEINPUT 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0
5315 387K TOR_INPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
5315 387K LOCATIONBLOCK 0 -- * * 0.0.0.0/0 0.0.0.0/0
5315 387K IPSECINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
5315 387K GUIINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
5209 380K WIRELESSINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW
5198 377K OVPNINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
5198 377K INPUTFW 0 -- * * 0.0.0.0/0 0.0.0.0/0
943 109K REDINPUT 0 -- * * 0.0.0.0/0 0.0.0.0/0
943 109K POLICYIN 0 -- * * 0.0.0.0/0 0.0.0.0/0
Chain BADTCP (2 references)
pkts bytes target prot opt in out source destination
3930 215K RETURN 0 -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x29
0 0 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x37
4 240 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x3F
0 0 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x01
0 0 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x06
0 0 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x03/0x03
1 60 PSCAN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x00
17 1222 NEWNOTSYN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:!0x17/0x02 ctstate NEW
Chain CAPTIVE_PORTAL_CLIENTS (0 references)
pkts bytes target prot opt in out source destination
0 0 RETURN 17 -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 limit: up to 3kb/s burst 1mb mode srcip
0 0 RETURN 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 limit: up to 3kb/s burst 1mb mode srcip
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0
Chain CONNTRACK (3 references)
pkts bytes target prot opt in out source destination
244K 113M ACCEPT 0 -- * * 0.0.0.0/0 0.0.0.0/0 ctstate ESTABLISHED
9 716 CTINVALID 0 -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
8 2244 ACCEPT 1 -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED
Chain CTINVALID (1 references)
pkts bytes target prot opt in out source destination
9 716 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4 prefix "DROP_CTINVALID "
9 716 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_CTINVALID */
Chain CUSTOMFORWARD (1 references)
pkts bytes target prot opt in out source destination
Chain CUSTOMINPUT (1 references)
pkts bytes target prot opt in out source destination
Chain CUSTOMOUTPUT (1 references)
pkts bytes target prot opt in out source destination
Chain DHCPBLUEINPUT (1 references)
pkts bytes target prot opt in out source destination
3933 253K DHCPINPUT 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0
Chain DHCPBLUEOUTPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 DHCPOUTPUT 0 -- * blue0 0.0.0.0/0 0.0.0.0/0
Chain DHCPGREENINPUT (1 references)
pkts bytes target prot opt in out source destination
1297 133K DHCPINPUT 0 -- green0 * 0.0.0.0/0 0.0.0.0/0
Chain DHCPGREENOUTPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 DHCPOUTPUT 0 -- * green0 0.0.0.0/0 0.0.0.0/0
Chain DHCPINPUT (2 references)
pkts bytes target prot opt in out source destination
32 10526 ACCEPT 17 -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:68 dpt:67
0 0 ACCEPT 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:68 dpt:67
Chain DHCPOUTPUT (2 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT 17 -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68
0 0 ACCEPT 6 -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:67 dpt:68
Chain GUIINPUT (1 references)
pkts bytes target prot opt in out source destination
106 6360 ACCEPT 6 -- green0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:444
Chain HOSTILE (3 references)
pkts bytes target prot opt in out source destination
31 1380 HOSTILE_DROP_IN 0 -- red0 * 0.0.0.0/0 0.0.0.0/0 match-set XD src
0 0 HOSTILE_DROP_OUT 0 -- * red0 0.0.0.0/0 0.0.0.0/0 match-set XD dst
Chain HOSTILE_DROP_IN (1 references)
pkts bytes target prot opt in out source destination
3338 149K DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_HOSTILE */
Chain HOSTILE_DROP_OUT (1 references)
pkts bytes target prot opt in out source destination
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_HOSTILE */
Chain ICMPINPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT 1 -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
Chain INPUTFW (1 references)
pkts bytes target prot opt in out source destination
0 0 DROP 6 -- red0 * 0.0.0.0/0 192.168.100.2 tcp dpt:22
0 0 ACCEPT 6 -- * * 192.168.1.240/29 192.168.1.1 tcp dpt:444
0 0 ACCEPT 6 -- * * 192.168.10.240/29 192.168.1.1 tcp dpt:444
0 0 ACCEPT 6 -- * * 192.168.1.240/29 192.168.10.1 tcp dpt:444
0 0 ACCEPT 6 -- * * 192.168.10.240/29 192.168.10.1 tcp dpt:444
0 0 ACCEPT 6 -- green0 * 192.168.1.0/24 192.168.1.1 multiport dports 139,444
0 0 ACCEPT 17 -- green0 * 192.168.1.0/24 192.168.1.1 multiport dports 53,137:138,123
0 0 ACCEPT 6 -- blue0 * 192.168.10.0/24 192.168.10.1 multiport dports 139,444
34 2074 ACCEPT 17 -- blue0 * 192.168.10.0/24 192.168.10.1 multiport dports 53,137:138,123
0 0 ACCEPT 6 -- * * 10.16.1.8/30 0.0.0.0/0 tcp dpt:444
0 0 ACCEPT 17 -- red0 * 0.0.0.0/0 192.168.100.2 udp dpts:1194:1198
0 0 ACCEPT 6 -- * * 192.168.1.5 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.1.15 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.1.10 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.1.4 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.1.11 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 17 -- * * 192.168.1.5 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.1.15 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.1.10 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.1.4 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.1.11 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 1 -- * * 192.168.1.5 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.1.15 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.1.10 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.1.4 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.1.11 0.0.0.0/0
0 0 ACCEPT 6 -- * * 192.168.1.5 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 6 -- * * 192.168.1.15 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 6 -- * * 192.168.1.10 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 6 -- * * 192.168.1.4 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 6 -- * * 192.168.1.11 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 0 -- * * 192.168.1.11 192.168.10.0/24
0 0 ACCEPT 0 -- * * 192.168.1.10 192.168.10.0/24
0 0 ACCEPT 0 -- * * 192.168.1.15 192.168.10.0/24
0 0 ACCEPT 6 -- * * 192.168.10.128/26 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 17 -- * * 192.168.10.128/26 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 1 -- * * 192.168.10.128/26 0.0.0.0/0
0 0 ACCEPT 6 -- * * 192.168.10.128/26 0.0.0.0/0 multiport dports 143,993,25,465,587,995,110
0 0 ACCEPT 17 -- blue0 * 192.168.10.0/24 0.0.0.0/0 udp dpts:1194:1198
0 0 ACCEPT 6 -- * * 192.168.10.52 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.51 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.53 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.54 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.55 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.71 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.81 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.72 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.82 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.56 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.57 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.58 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.59 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.73 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 6 -- * * 192.168.10.83 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 17 -- * * 192.168.10.52 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.51 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.53 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.54 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.55 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.71 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.81 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.72 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.82 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.56 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.57 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.58 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.59 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.73 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 17 -- * * 192.168.10.83 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 1 -- * * 192.168.10.52 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.51 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.53 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.54 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.55 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.71 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.81 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.72 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.82 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.56 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.57 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.58 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.59 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.73 0.0.0.0/0
0 0 ACCEPT 1 -- * * 192.168.10.83 0.0.0.0/0
0 0 ACCEPT 0 -- * * 192.168.1.240/29 192.168.10.0/24
0 0 ACCEPT 0 -- * * 192.168.1.240/29 192.168.1.0/24
0 0 ACCEPT 0 -- * * 192.168.10.240/29 192.168.10.0/24
0 0 ACCEPT 0 -- * * 192.168.10.240/29 192.168.1.0/24
0 0 ACCEPT 0 -- * * 10.16.1.8/30 0.0.0.0/0
0 0 ACCEPT 6 -- * * 192.168.10.101 0.0.0.0/0 multiport dports 21,20,80,443,990,989,4434
0 0 ACCEPT 17 -- * * 192.168.10.101 0.0.0.0/0 udp dpt:123
0 0 ACCEPT 1 -- * * 192.168.10.101 0.0.0.0/0
0 0 ACCEPT 6 -- * * 192.168.10.101 0.0.0.0/0 tcp dpt:4001
0 0 ACCEPT 6 -- * * 192.168.10.103 0.0.0.0/0 tcp dpt:40001
Chain IPSBYPASS (3 references)
pkts bytes target prot opt in out source destination
0 0 CONNMARK 0 -- * * 0.0.0.0/0 0.0.0.0/0 CONNMARK save mask 0x7fffffff
Chain IPS_FORWARD (1 references)
pkts bytes target prot opt in out source destination
0 0 NFQUEUE 0 -- red0 red0 0.0.0.0/0 0.0.0.0/0 NFQUEUE balance 0:3 bypass cpu-fanout
Chain IPS_INPUT (1 references)
pkts bytes target prot opt in out source destination
48612 19M NFQUEUE 0 -- red0 * 0.0.0.0/0 0.0.0.0/0 NFQUEUE balance 0:3 bypass cpu-fanout
Chain IPS_OUTPUT (1 references)
pkts bytes target prot opt in out source destination
49695 5169K NFQUEUE 0 -- * red0 0.0.0.0/0 0.0.0.0/0 NFQUEUE balance 0:3 bypass cpu-fanout
Chain LOG_DROP (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0
Chain LOG_REJECT (0 references)
pkts bytes target prot opt in out source destination
0 0 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4
0 0 REJECT 0 -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain LOOPBACK (3 references)
pkts bytes target prot opt in out source destination
5928 446K ACCEPT 0 -- lo * 0.0.0.0/0 0.0.0.0/0
5928 446K ACCEPT 0 -- * lo 0.0.0.0/0 0.0.0.0/0
0 0 SPOOFED_MARTIAN 0 -- * * 127.0.0.0/8 0.0.0.0/0
0 0 SPOOFED_MARTIAN 0 -- * * 0.0.0.0/0 127.0.0.0/8
Chain NEWNOTSYN (1 references)
pkts bytes target prot opt in out source destination
17 1222 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4 prefix "DROP_NEWNOTSYN "
17 1222 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_NEWNOTSYN */
Chain OVPNBLOCK (3 references)
pkts bytes target prot opt in out source destination
0 0 RETURN 1 -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED
Chain OVPNINPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT 17 -- red0 * 0.0.0.0/0 0.0.0.0/0 udp dpt:1196
Chain POLICYFWD (1 references)
pkts bytes target prot opt in out source destination
0 0 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4 prefix "DROP_FORWARD "
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_FORWARD */
Chain POLICYIN (1 references)
pkts bytes target prot opt in out source destination
0 0 DROP 17 -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:514
11 1294 ACCEPT 0 -- green0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0
0 0 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4 prefix "DROP_INPUT "
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_INPUT */
Chain POLICYOUT (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT 0 -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_OUTPUT */
Chain PSCAN (7 references)
pkts bytes target prot opt in out source destination
5 300 LOG 6 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 /* DROP_TCP PScan */ LOG flags 0 level 4 prefix "DROP_TCP Scan "
0 0 LOG 17 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 /* DROP_UDP PScan */ LOG flags 0 level 4 prefix "DROP_UDP Scan "
0 0 LOG 1 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 /* DROP_ICMP PScan */ LOG flags 0 level 4 prefix "DROP_ICMP Scan "
0 0 LOG 0 -f * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 /* DROP_FRAG PScan */ LOG flags 0 level 4 prefix "DROP_FRAG Scan "
5 300 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_PScan */
Chain REDINPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 SPOOFED_MARTIAN 0 -- red0 * 192.168.100.2 0.0.0.0/0
Chain SPOOFED_MARTIAN (3 references)
pkts bytes target prot opt in out source destination
0 0 LOG 0 -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 10/sec burst 5 LOG flags 0 level 4 prefix "DROP_SPOOFED_MARTIAN "
0 0 DROP 0 -- * * 0.0.0.0/0 0.0.0.0/0 /* DROP_SPOOFED_MARTIAN */
Chain WIRELESSFORWARD (1 references)
pkts bytes target prot opt in out source destination
6875 433K RETURN 0 -- blue0 * 192.168.10.0/24 0.0.0.0/0
0 0 LOG 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0 LOG flags 0 level 4 prefix "DROP_Wirelessforward "
0 0 DROP 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0 /* DROP_Wirelessforward */
Chain WIRELESSINPUT (1 references)
pkts bytes target prot opt in out source destination
3994 249K RETURN 0 -- blue0 * 192.168.10.0/24 0.0.0.0/0
11 3626 LOG 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0 LOG flags 0 level 4 prefix "DROP_Wirelessinput "
11 3626 DROP 0 -- blue0 * 0.0.0.0/0 0.0.0.0/0 /* DROP_Wirelessinput */
- On IPFire, what is the output of
ifconfig?
blue0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.1 netmask 255.255.255.0 broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 59207 bytes 17884966 (17.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 51396 bytes 8086875 (7.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
blue0p0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 4611 bytes 622489 (607.8 KiB)
RX errors 0 dropped 1 overruns 0 frame 0
TX packets 1165 bytes 153748 (150.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device memory 0x81600000-816fffff
blue0p1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 55782 bytes 18169645 (17.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 50230 bytes 7933073 (7.5 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device memory 0x81300000-813fffff
green0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.1 netmask 255.255.255.0 broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 55205 bytes 40454916 (38.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 86078 bytes 44589286 (42.5 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device memory 0x81900000-819fffff
imq0: flags=195<UP,BROADCAST,RUNNING,NOARP> mtu 1500
ether xx:xx:xx:xx:xx:xx txqueuelen 32 (Ethernet)
RX packets 219488 bytes 69190421 (65.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 219488 bytes 69190421 (65.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 5858 bytes 438046 (427.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5858 bytes 438046 (427.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
red0: flags=67<UP,BROADCAST,RUNNING> mtu 1500
inet 192.168.100.2 netmask 255.255.255.0 broadcast 0.0.0.0
ether xx:xx:xx:xx:xx:xx txqueuelen 1000 (Ethernet)
RX packets 219490 bytes 69193277 (65.9 MiB)
RX errors 0 dropped 48752 overruns 0 frame 0
TX packets 137785 bytes 60705800 (57.8 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device memory 0x81c00000-81cfffff
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1400
inet 10.16.1.1 netmask 255.255.255.255 destination 10.16.1.2
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
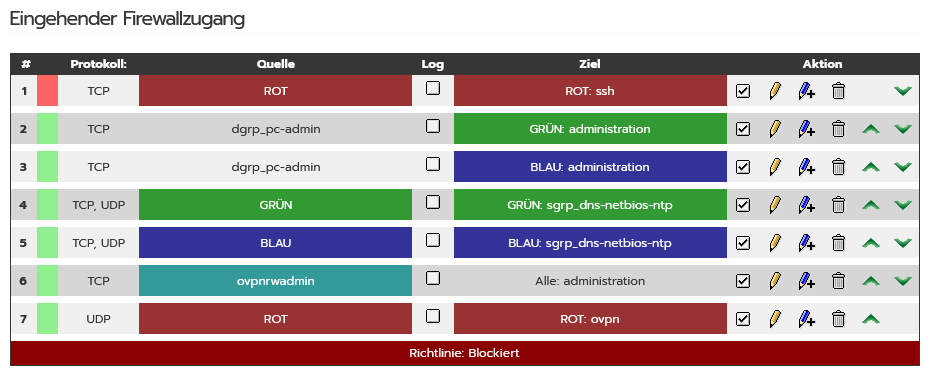
- What does your firewall ruleset look like (screenshot of it)?
I set rule 1 to drop ssh requests but this has no effect. Also rules 2,3 and 7 seem not to be required as these services are allowed by default… Can I change this?
- When did the problem occur? Is it reproducible? If so, which steps are needed to be taken?
Everytime when the ssh service is enabled.