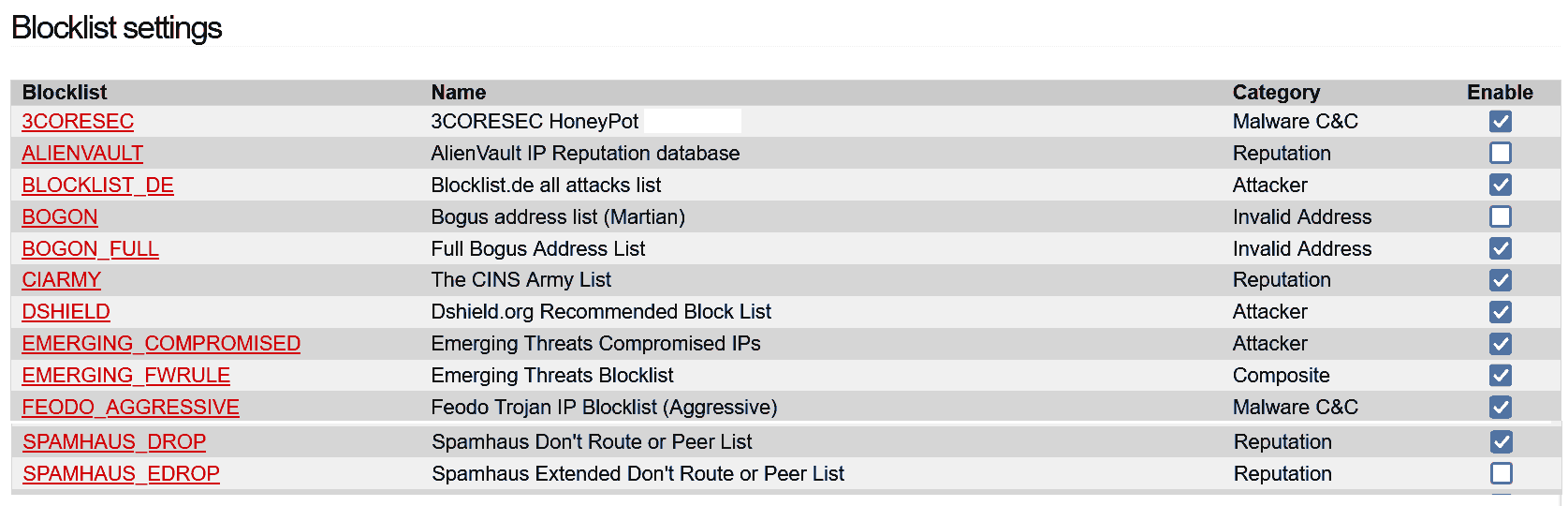
I have a question regarding the IPFire Blocklist
What does this line in the ‘EMERGING_FWRULE’ do exactly?
'disable' => ['FEODO_RECOMMENDED', 'FEODO_IP', 'FEODO_AGGRESSIVE', 'SPAMHAUS_DROP', 'DSHIELD'] },
Does the ‘disable’ field actually “effectively” disable other 5 lists in the “background” even if they are enabled in the front end?
Would the disabled status be indicated by being unchecked or just ignored in the backend even if the 5 lists ?
This would be probably best answered by @Timf himself but I don’t think he’s been around lately.
The reason for my question is that the Emerging Rules are only updated 1 per day and 4-5 times a week but the FEODO, DROP and DSHIELD lists are updated much more often so that would not make sense to disable them even if they are included in the Emerging lists.
/var/ipfire/.ipblocklist/settings
/var/ipfire/.ipblocklist/sources
############################################################################
# #
# IP Address blocklists for IPFire #
# #
# This file contains a list of blocklist sources that will replace the one #
# internal to the updated if it is found at /var/ipfire/blocklist/sources. #
# The intention is to provide a common source of information for both the #
# updater and WUI. #
# #
# The chains created in the packet filter will be named by the top level #
# key and this will also be used in the log message to identify the reason #
# for the dropped packet. #
# #
# The fields are: #
# #
# name The blocklist's full name #
# url URL of the file containing the list #
# info URL giving information about the source #
# parser The parser function used to extract IP addresses from the #
# downloaded list #
# rate Minimum period between checks for updates. Can be specified in #
# days (d), hours (h) or minutes (m) #
# category Used for documentation on the WUI. Can be one of the following #
# 'application' Potentially unwanted applications #
# 'attacker' Generic source of malicious packets #
# 'c and c' Malware Command and Control source #
# 'composite' Composite of other lists #
# 'invalid' Invalid addresses on the public internet #
# 'scanner' Port scanner that is not initself malicious #
# disable Name of another list to disable if this one is enabled. Used #
# when the other list is a subset of this one. #
# #
# The info and category fields are purely for documentation. #
# #
############################################################################
package IPblocklist::List;
our %sources = ( 'EMERGING_FWRULE' => { 'name' => 'Emerging Threats Blocklist',
'url' => 'https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt',
'info' => 'https://doc.emergingthreats.net/bin/view/Main/EmergingFirewallRules',
'parser' => 'ip-or-net-list',
'rate' => '1h',
'category' => 'composite',
'disable' => ['FEODO_RECOMMENDED', 'FEODO_IP', 'FEODO_AGGRESSIVE', 'SPAMHAUS_DROP', 'DSHIELD'] },