Haven’t used it for years, but with IoT the need comes back:
I need to access from the GREEN network to webservers of devices settled on the BLUE network.
All my default policies are “blocked”, so without any firewall rule I couldn’t even ping any device in BLUE.
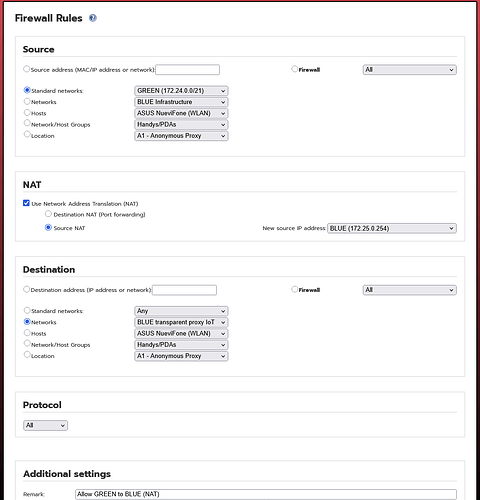
So I created a simple source NAT fw rule and I can ping the devices, but still can’t access the webservers.
Any idea what’s missing?
nickh
7 April 2025 13:32
2
You don’t want NAT, just a FORWARD ALLOW rule.
1 Like
hvacguy
7 April 2025 13:53
3
It is true you do not need NAT
Really? I thought source IPs that are Not member of the target Network range will be dropped by the target. Thats why i thought NAT will be necessary.
The wiki documentation on creating a pinhole from blue to green can be used as an example. Just swap around the source and destination to deal with the fact that the direction you want is the opposite one, ie source will be green and destination blue.
https://www.ipfire.org/docs/configuration/firewall/rules/bg-holes
As shown in that page, NAT is not used.
Another example would be the pinhole to the orange dmz.
https://www.ipfire.org/docs/configuration/firewall/rules/dmz-holes
1 Like
That’s what I have, when not using NAT. I tried that, may still ping, but won’t reach the webif of the targets.
pscar13
7 April 2025 15:32
7
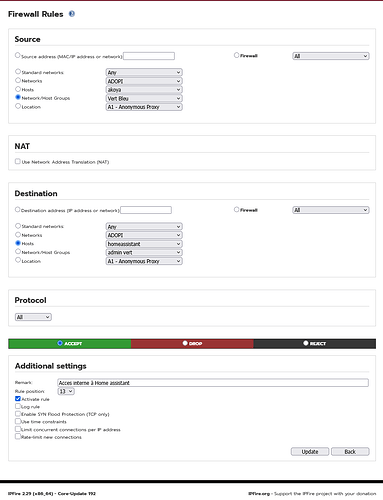
Here’s the rule I use to access my “Home Assistant” server on blue from my PCs on green.
Edit : All my default policies are “blocked”
Does not work for me. Can’t even reach the webif of the WIFI AP.
pscar13
7 April 2025 15:45
9
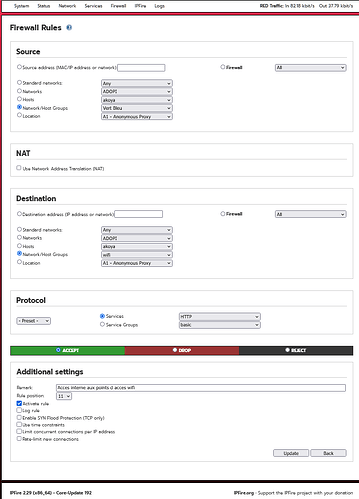
I have another rule for that
Edit : My WiFi access points are also in a group
In the end, it’s always the same and not much to make wrong. But however, for me, it’s not working and I don’t know why…
pscar13
7 April 2025 15:56
11
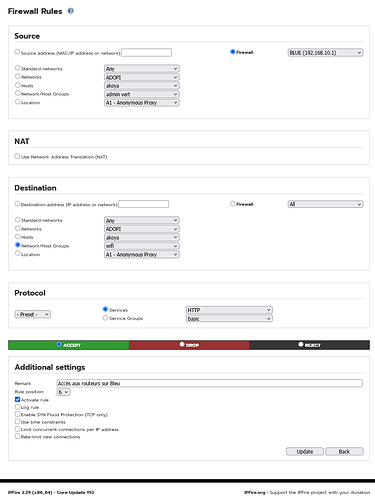
But I had to add this rule too.
Edit : I don’t use the proxy on Blue
1 Like
bloater99
7 April 2025 15:57
12
I know this is not a solution for you, but I don’t mess with the Blue network at all. I let my AP handle it. Create standard and guest networks in the AP, and connect IoT devices to the guest. I also give them static addresses and map hostnames to them in Network->Edit Hosts in the IPFire webif.
1 Like
Hm I don’t know what’s the purpose of that rule but it’s working!
pscar13
7 April 2025 16:08
14
Also
1 Like
pscar13
7 April 2025 16:10
15
I guess because the Blue interface is the gateway from Green to Blue, but experts could certainly explain it better.
I use here Captive Portal
I do the same, but for all devices, also on GREEN.
1 Like