hi
I’ve been using this mode for several months and I think it works well.
if you want to test here’s the information
in the unbound case
1: creates the local file.d folder
2: Creates the zonefiles folder
in the file unbound local.d
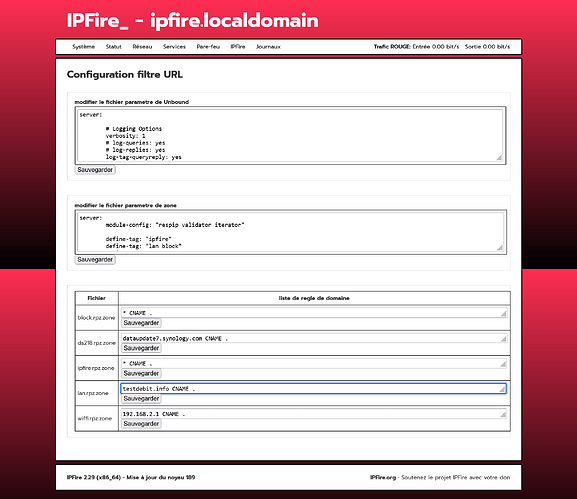
Create the setting.conf file
server:
# Logging Options
verbosity: 1
# log-queries: yes
# log-replies: yes
log-tag-queryreply: yes
# Randomise any cached responses
rrset-roundrobin: yes
# Harden against receiving dnssec-stripped data
harden-dnssec-stripped: yes
# Harden against queries that fall under dnssec-signed nxdomain names.
harden-below-nxdomain: yes
# Sent minimum amount of information to upstream servers to enhance
# privacy. Only sent minimum required labels of the QNAME and set QTYPE
# to A when possible.
qname-minimisation: yes
# if yes, Unbound doesn't insert authority/additional sections
# into response messages when those sections are not required.
minimal-responses: yes
# if yes, the above default do-not-query-address entries are present.
# if no, localhost can be queried (for testing and debugging).
# block cname ads using stub-zone
do-not-query-localhost: yes
# If yes, deny queries of type ANY with an empty response.
# Default is no. If disabled, unbound responds with a short list
# of resource records if some can be found in the cache and makes
# the upstream type ANY query if there are none.
deny-any: yes
# Configure a local zone. The type determines the answer to give
# if there is no match from local-data. The types are deny,
# refuse, static, transparent, redirect, nodefault, typetranspar-
# ent, inform, inform_deny, inform_redirect, always_transparent,
# always_refuse, always_nxdomain, noview, and are explained below.
# After that the default settings are listed. Use local-data: to
# enter data into the local zone. Answers for local zones are
# authoritative DNS answers. By default the zones are class IN.
# local-zone: "pc.localdomain" deny
# Will trust glue only if it is within the servers authority.
# Default is on.
harden-glue: yes
# Configure local data, which is served in reply to queries for it.
# The query has to match exactly unless you configure the local-zone
# as redirect. If not matched exactly, the local-zone type determines
# further processing. If local-data is configured that is not a subdomain
# of a local-zone, a transparent local-zone is configured. For record types
# such as TXT, use single quotes, as in local-data: 'example. TXT "text"'.
#local-data: "pc.localdomain A 0.0.0.0"
# number of threads to create
# of CPU cores in the machine
num-threads: 4
msg-cache-slabs: 8
rrset-cache-slabs: 8
infra-cache-slabs: 8
key-cache-slabs: 8
# Faster UDP with multithreading (only on Linux).
so-reuseport: yes
# Should additional section of secure message also be kept clean of
# unsecure data. Useful to shield the users of this validator from
# potential bogus data in the additional section. All unsigned data
# in the additional section is removed from secure messages.
val-clean-additional: yes
# DNS Rebinding
# For DNS Rebinding prevention
private-address: 127.0.0.0/8
private-address: 10.0.0.0/8
private-address: 169.254.0.0/16
private-address: 172.16.0.0/12
private-address: 192.168.0.0/16
then creates the filters.conf file
server:
module-config: "respip validator iterator"
define-tag: "ipfire block"
define-tag: "lan block"
define-tag: "nas block"
define-tag: "wiffi block"
# Per client IP
access-control-tag: 127.0.0.1/32 "ipfire block"
access-control-tag: 192.168.1.2/32 "lan block"
access-control-tag: 192.168.1.15/32 "nas block"
access-control-tag: 192.168.2.0/24 "wiffi block"
rpz:
# The name of the RPZ authority zone
name: ipfire
# The location of the remote RPZ zonefile.
# url: http://www.example.com/example.org.zone (not a real RPZ file)
#zonefile: zonefiles/ipfire.rpz.zone
zonefile: /etc/unbound/zonefiles/ipfire.rpz.zone
tags: "ipfire"
# Always use this RPZ action for matching triggers from this zone.
# Possible action are: nxdomain, nodata, passthru, drop, disabled,
# and cname.
rpz-action-override: passthru
# Log all applied RPZ actions for this RPZ zone. Default is no.
rpz-log: yes
# Specify a string to be part of the log line.
rpz-log-name: ALLOW-IPFIRE
rpz:
# The name of the RPZ authority zone
name: nas
# The location of the remote RPZ zonefile.
# url: http://www.example.com/example.org.zone (not a real RPZ file)
#zonefile: zonefiles/nas.rpz.zone
zonefile: /etc/unbound/zonefiles/nas.rpz.zone
tags: "nas"
# Always use this RPZ action for matching triggers from this zone.
# Possible action are: nxdomain, nodata, passthru, drop, disabled,
# and cname.
rpz-action-override: passthru
# Log all applied RPZ actions for this RPZ zone. Default is no.
rpz-log: yes
# Specify a string to be part of the log line.
rpz-log-name: ALLOW-NAS
rpz:
# The name of the RPZ authority zone
name: wiffi
# The location of the remote RPZ zonefile.
# url: http://www.example.com/example.org.zone (not a real RPZ file)
#zonefile: zonefiles/wiffi.rpz.zone
zonefile: /etc/unbound/zonefiles/wiffi.rpz.zone
tags: "wiffi"
# Always use this RPZ action for matching triggers from this zone.
# Possible action are: nxdomain, nodata, passthru, drop, disabled,
# and cname.
rpz-action-override: passthru
# Log all applied RPZ actions for this RPZ zone. Default is no.
rpz-log: yes
# Specify a string to be part of the log line.
rpz-log-name: ALLOW-WIFI
rpz:
# The name of the RPZ authority zone
name: lan
# The location of the remote RPZ zonefile.
# url: http://www.example.com/example.org.zone (not a real RPZ file)
#zonefile: zonefiles/lan.rpz.zone
zonefile: /etc/unbound/zonefiles/lan.rpz.zone
tags: "lan"
# Always use this RPZ action for matching triggers from this zone.
# Possible action are: nxdomain, nodata, passthru, drop, disabled,
# and cname.
rpz-action-override: passthru
# Log all applied RPZ actions for this RPZ zone. Default is no.
rpz-log: yes
# Specify a string to be part of the log line.
rpz-log-name: ALLOW-LAN_1
rpz:
# The name of the RPZ authority zone
name: block
# The location of the remote RPZ zonefile.
# url: http://www.example.com/example.org.zone (not a real RPZ file)
#zonefile: block.rpz.zone
zonefile: /etc/unbound/zonefiles/block.rpz.zone
tags: "block"
# Always use this RPZ action for matching triggers from this zone.
# Possible action are: nxdomain, nodata, passthru, drop, disabled,
# and cname.
rpz-action-override: nxdomain
# Log all applied RPZ actions for this RPZ zone. Default is no.
rpz-log: yes
# Specify a string to be part of the log line.
rpz-log-name: BLOK-ALL
in define-tag: definish your tag
in access-control-tag: definish your ip
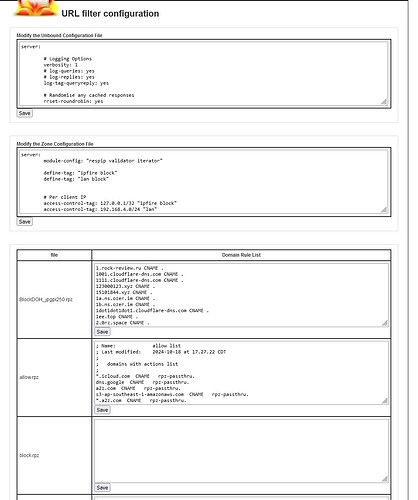
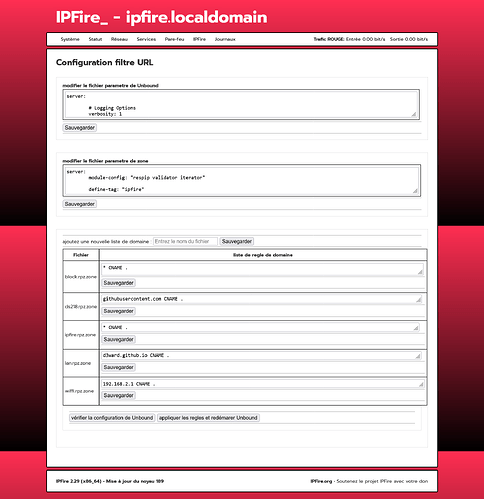
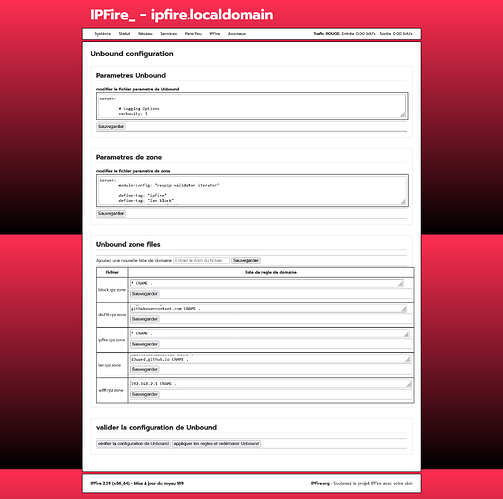
in the unbound zonefiles folder
1: creates the file ipfire.rpz.zone
Edit file ipfire.rpz.zone
* CNAME .
2: creates the block.rpz.zone file
Edit file block.rpz.zone file
* CNAME .
3: creates the file lan.rpz.zone
in the file write to you your url address in the syntax surport by unbound
e.g.
*.site.com
site.com
www.site.com
(in the zonefiles folder you create an more than ever of areas that you veil and name them as you want)
and to block the ip configure the ipfire in block mode
in mode you to clear the rules for each ip that you want to allow
ty