I’m back again. I thought about my firewall rules which caused my remote syslog problem. And now I consider it being a firewall problem. For testing I setup virtual machines sinnce I didn’t want to do testing on my production IPFire.
My test bed is the LAN-side of a ZyXEL USG 60. Its LAN 172.16.1.0/24 is my virtual Internet.
The virtual IPFire has 172.16.1.4 on RED and 192.168.4.0/24 on GREEN.
The rsyslog (also a MTA) has its own global address. I configured an ALIAS in IPFire and setup SNAT and DNAT rules. So, the rsyslog server has 172.16.1.201 ON RED and 192.168.4.201 on GREEN. For easier testing with nmap I enabled TCP port 514 for rsyslog.
From the internet only the SSH port of the rsyslog should be reachable and not port 514 for rsyslog!
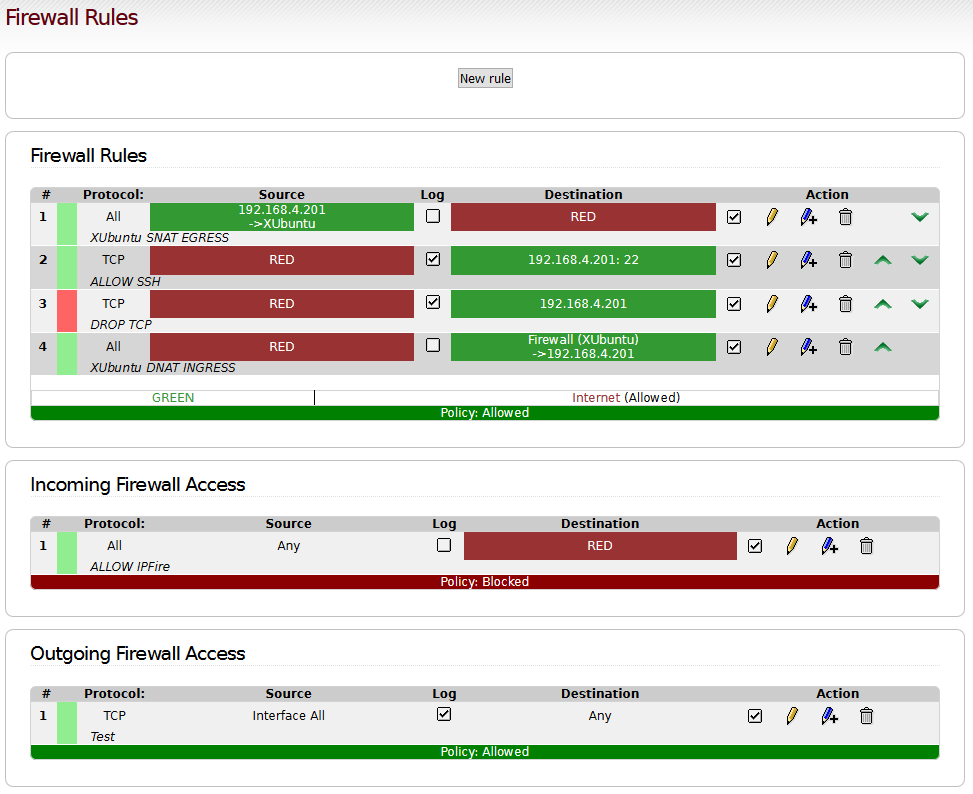
Firewall rules
Protocol Source Destination Comment
TCP RED 192.168.4.201:22 ALLOW SSH
Protocol Source Destination Comment
TCP RED 192.168.4.201 DROP ANY TCP
Well, my DROP ANY TCP rule is meant to prevent TCP access from the Internet (RED) to my server (GREEN). I do an nmap form the internet side (RED) to my server (ALIAS). As expected, 22 is open and 514 is closed 
root@u2004s:~# nmap 172.16.1.201 -sT -p 22,514
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-09 10:53 UTC
Nmap scan report for 172.16.1.201
Host is up (0.00065s latency).
PORT STATE SERVICE
22/tcp open ssh
514/tcp filtered shell
MAC Address: 08:00:27:F5:1D:C1 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.34 seconds
And that is the moment where IPFire no longer feeds the rsyslog daemon 
I do an nmap from within the IPFire:
[root@vipfire ~]# nmap 192.168.4.201 -sT -p 22,514
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-09 13:00 CEST
Nmap scan report for 192.168.4.201
Host is up (0.00034s latency).
PORT STATE SERVICE
22/tcp filtered ssh
514/tcp filtered shell
MAC Address: 08:00:27:3F:24:72 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.31 seconds
Port 514 is filtered, hence the rsyslog is no longer feeded by IPFire!
The solution: I configured “Outgoing Firewall Access”:
Protocol Source Destination Comment
TCP Interface All Any ALLOW ANY TCP
Okay so far. The strange thing is, the “Default firewall behaviour” is “Allowd”. Which means, I configued an ALLOW RULE on the top of the default ALLOW 
–
Rainer