Hi
as the topic…
I am fully using proxy (authentication method: Windows Active Directory (samba), clamv, url filter itd.)
After blocking ports 80 and 443, some sites are down (max 20%).
no matter if they are https or http.
I’ve run out of ideas …
can anyone help ?
Hi,
according to the screenshot you supplied, your firewall rules are misconfigured.
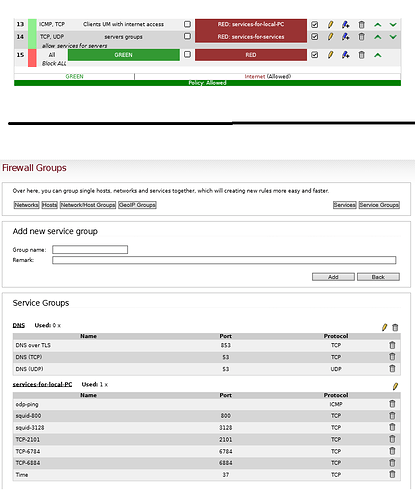
Rule 13 permits connections to destination ports 800, 3128 et al. within any IP address related RED, which most likely is the public internet in your case. This is wrong, the destination of that connections should be the GREEN interface of your IPFire machine.
I urgently recommend to read the firewall documentation before using IPFire further, as you does not seem to have understood how the firewall rule GUI works.
No offense intended, but nobody can read the docs for you. See also:
Thanks, and best regards,
Peter Müller
thank you very much for your answer
and of course I’m not offended.
read it again and understand my mistake.
I created the rule as in the picture.
unfortunately it works the same.
Hi,
sorry for the late reply.
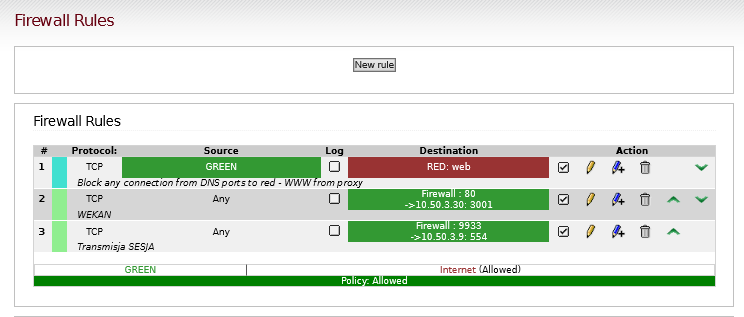
According to your screenshot, those rules still contain some quirks:
- Rule 1 rejects any traffic from your GREEN network to a service (port) group called “web” - I assume it contains ports 80 and 443 - within RED. This means clients within GREEN will not be able to talk to web services within RED at all, and get an ICMP reject quickly instead of running into a timeout.
- Rules 2 and 3 allow any traffic from any source to the GREEN firewall interface on port 80 (rule 2) and 9933 (rule 3 - not sure what your intention is), and they will be NATted to
10.50.3.30or10.50.3.9.
This looks pretty much like an overkill. 
My suggestions are as follows:
-
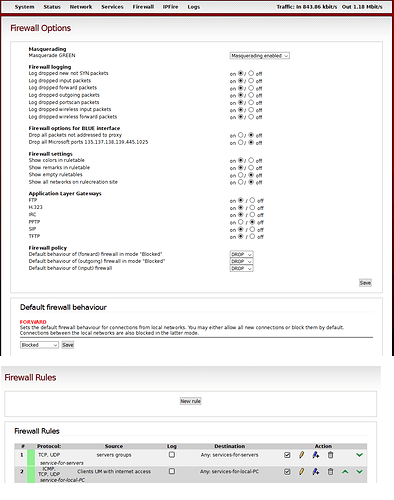
First, change the EDIT: forward firewall default policy to “blocked” so any traffic from internal networks (excluding the firewall system itself) to RED will be dropped. You only need to configure firewall rules for traffic you want to allow then, which most probably makes your ruleset more lean.
-
Configure your clients to use IPFire’s proxy. They should be able to reach it if they are within GREEN, as traffic from there to the firewall itself is permitted by default. You can test that by running a
telnetconnection against the configured proxy port (800 or 3128 in most cases). -
Your clients should be able to reach web services within RED now, if they pass proxy authentication. Since the firewall itself is opening up a new TCP connection to RED, which is also permitted by default, this should work.
Ultimately, I am pretty sure you do not even need to configure any firewall rule for this - that is, if I have not overlooked something… 
Thanks, and best regards,
Peter Müller
Hello Peter,
i think you mean Forward Firewall “blocked”.
Hi,
sh*t, thanks for spotting that. Yes, I meant “forward firewall”… :-/
Thanks, and best regards,
Peter Müller
I changed the rules.
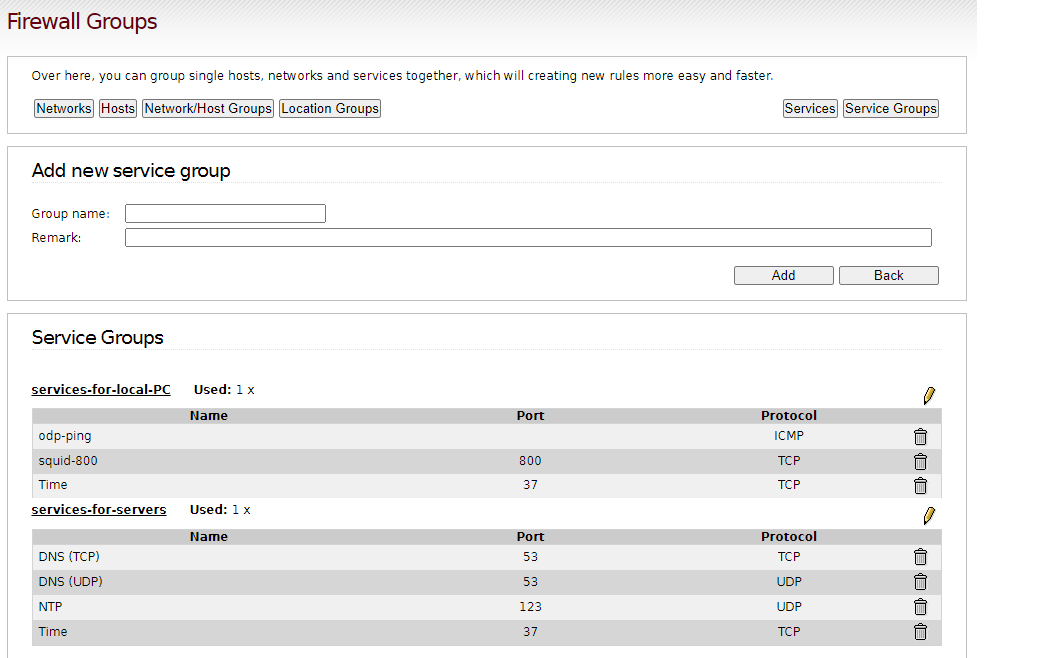
only allow ports: squid 800, dns 52 and time 37.
firefox has its proxy set to ipfire port 800
it works !
unfortunately very slowly - entering a website takes 10-15 seconds.
When it unblocks port 80/443 it comes in in no time.
you probably need to add some more loop/redirect 80/443 ?
Peter, will you help?
Hi,
only allow ports: squid 800, dns 52 and time 37.
hm, could you post screenshots of those firewall rules as well? Based on your last post, I think they are still using the wrong destination, but I am not sure.
Personally, I have not seen port 37 to be in usage for ages. Time synchronisation is done by NTP (destination port: UDP 123) virtually everywhere, including IPFire systems.
unfortunately very slowly - entering a website takes 10-15 seconds.
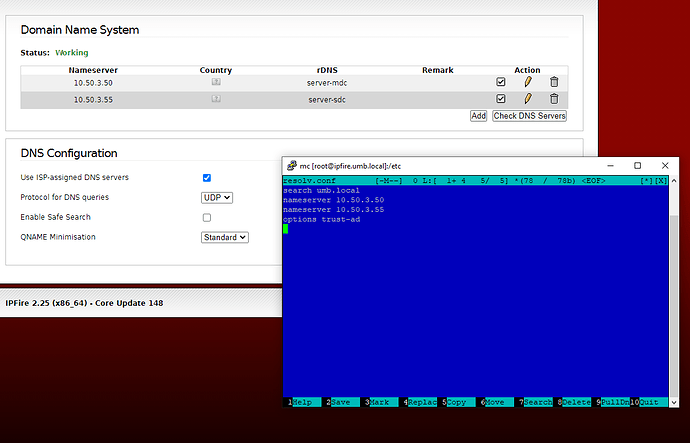
Are you using slow DNS resolvers? Those might be the root cause for this, as Squid has to look up any given destination, which takes more time. Is the system resolver of your client configured correctly?
you probably need to add some more loop/redirect 80/443 ?
Normally, this should not be necessary.
Thanks, and best regards,
Peter Müller
I learned a lot about ipfire from the beginning of this post
generally it wants to pass everything through the proxy for 3 reasons.
1 - the company does not have the resources for professional UTM, so it strives to increase safety as much as possible
2 - wants to cut team vievera dwservice and other rdp’s
3 - wants to use antivirus on entry
I think that as soon as it solves the problem of very slow opening of websites, ipfire can safely work in large companies (in the Active Directory + proxy + snort + geoblock + website filter option [in my case I based the filter on the kaspersky KES12 antivirus - it works great with AD] + tcpdump with loging script in cron)
=======================================
tcpdump-based network traffic logging script
#!/bin/bash
killall tcpdump
mv /var/-DATA-/logi/tcp.dmp /var/-DATA-/logi/date +%Y-%m-%d.dmp
tcpdump -i green0 tcp [13] == 2 -w /var/-DATA-/logi/tcp.dmp &
tar cvfz /var/-DATA-/logi/date +%Y-%m-%d.tar.gz /var/-DATA-/logi/date +%Y-%m-%d.dmp
rm /var/-DATA-/logi/date +%Y-%m-%d.dmp"
=======================================
Any news on the topic? Slowdowns?
What is the best way (firewall rules) to enforce the use of the proxy?