Hello, I have the same problem - I have almost identical problems in my post. After the update to 151, NtN dials in to the opposite party, green = connected, but it is no longer possible to get through. I noticed it when I restarted … Provider changes my IP only once a week (for whatever reason … different topic). Nevertheless, although I thought I had solved my problems with firewall release and routing, zack … restart after update and nothing works anymore.
the xx.ddns.net address is not automatically resolved for me … then just remains red and nothing is displayed.
Greetings M
EDIT:
You have the same error in your log!
09:22:02 YYYn2n [25687]: ERROR: Linux route delete command failed: external program exited with error status: 2
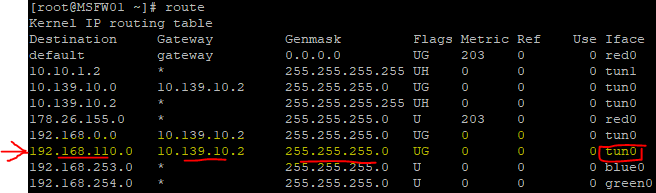
Check out my post, there is a route inside that is wrong … so that’s how it was for me …
Vielleicht hilft Ihnen auch mein Post hier etwas…? Post…klick