Sorry for resurrecting this old thread, but I have solved the issue, it still requires tidying up which is also why I’m posting for some further advice, and maybe some closure.
I had given up with the Vuescan and HP printer, after a firmware update locked the printer, however after getting a new toy I had to come back to this again. This particular situation was that I was not able to communicate with my BlueSound unit on the wired network (Green) from my mobile devices on the wireless network (Blue), the app uses mDNS for the device discovery.
mDNS-Repeater was working out of the box, and could see in the debug mode packets being repeated but with nothing really happening, so I started to dive into the logs and the workings of IPTables.
The first repeating error in the log was;
DROP_Wirelessinput from Blue0 to 224.0.0.251
This would be the returning traffic from my Bluesound unit to the mobile devices, and it was getting stopped by IPFire, so after some playing I added this to IPTables;
#iptables -I WIRELESSINPUT 1 -p udp --dport 5353 -i blue0 -j ACCEPT
That cleared the error in the log, but now I was getting a new one;
DROP_Forward from my wireless device to my BlueSound unit
and it was the same for all the wireless devices, so after some more playing this is what I added to get to IPTables;
#iptables -I POLICYFWD 5 -d 192.168.212.82 -s 192.168.222.0/24 -j ACCEPT
position 5 being the third from the bottom of the list, the IP address is that of my BlueSound unit and the range of my Blue0 network. With both of these applied to IPTables the mobile app can find and connect to the BlueSound unit without issue, what was interesting from the start without these being added to the IPTables I could from any wireless device access the http portal of the BlueSound unit without issue.
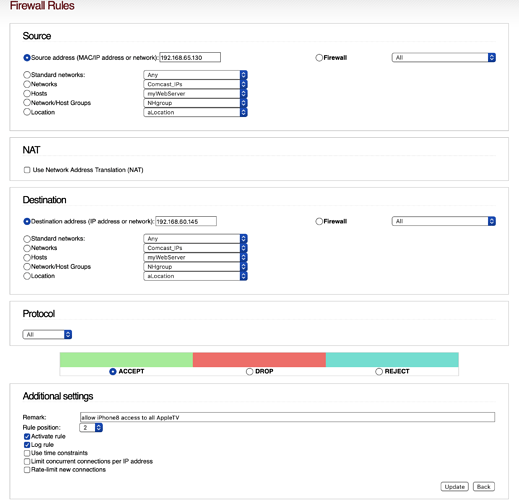
So that is where I am now, the next issue is if I make any changes to the firewall setting in the IPFire GUI or reboot, they get wiped. Then I have to SSH back in and re-apply them, bit of a pain. I have tried many combinations in the GUI to add the rules, but with no luck.
From what I have read so far it is possible to manually force these changes to the IPTables, not sure how yet. However as a matter of learning, it would be good to know what has to be entered in the GUI for IPFire to apply these changes. I’ve learnt a lot on the functions of IPTables, they are very logical, making them simple to work with, and even simpler to get then really wrong. But I cannot work out how IPFire maps from the GUI to IPTables.
Hope this is of some use to people, and once there is a permanent solution to a non-erasing IPTable entry I’ll get back and update with the new information, hopefully quicker than four years.