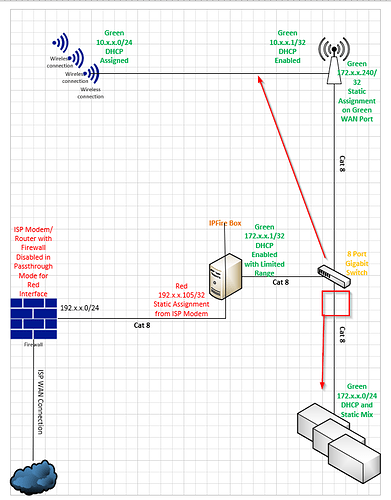
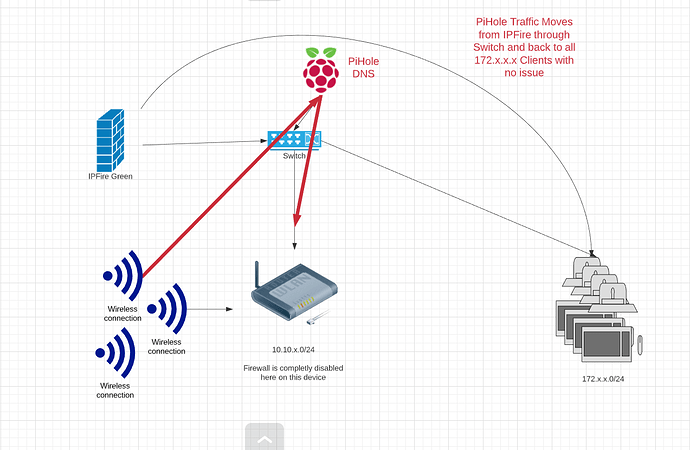
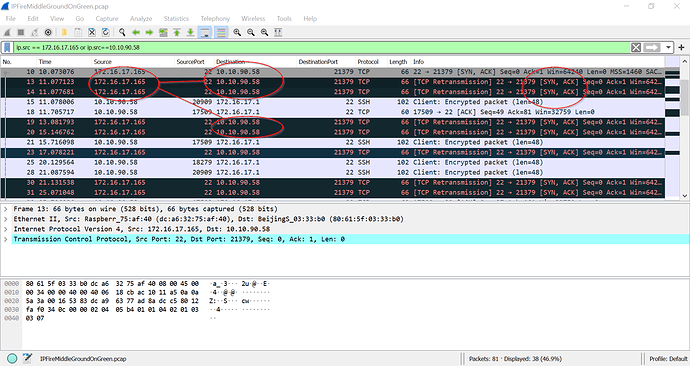
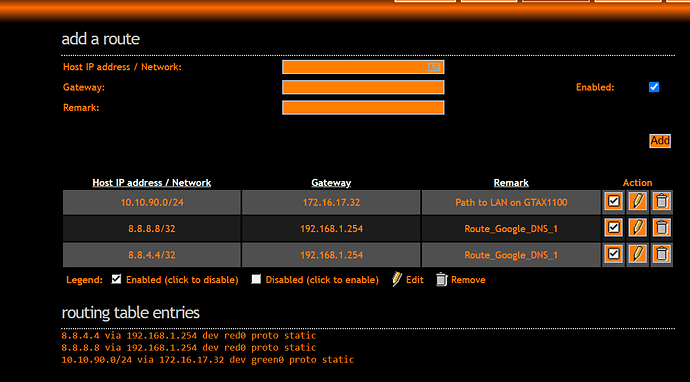
As Bernhard mentioned in an adjacent thread, I have 2 adjacent logical networks on Green, as you can see in the image. I am now toying around with PiHole.
I took a Raspberry Pi 4b, installed Rasbian latest revision on it, installed PiHole through scripts provided on their website and assigned it to a static IP address in my 172.x.x.165/32 network with the Green Interface 172.x.x.1 being the gateway, and plugged it into the switch just above the red box on the right in the below image.
Here is the trippy thing. I can get to PiHole from any computer in the 172.x.x.0/24 network, at its Web UI http://ip/admin and it loads, browses and acts absolutely normal. Fully functional might I add… except for 1 thing.
When I jump on any other computer in my logical 10.x.x.0/24 network segment, I can’t hit it with SSH, ICMP, HTTP or anything else successfully.
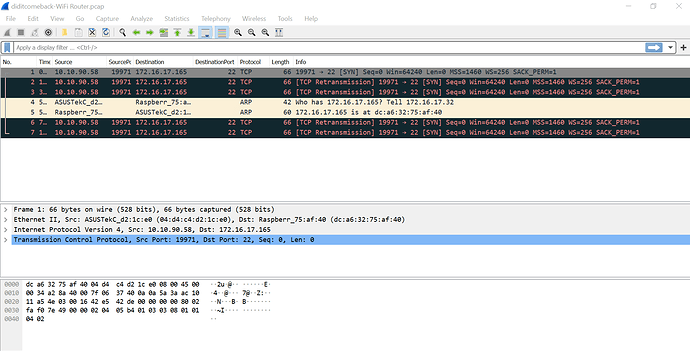
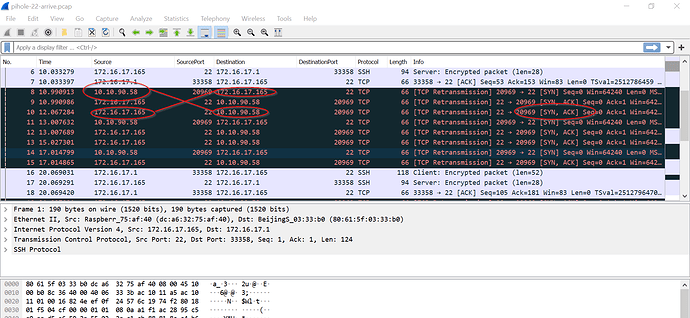
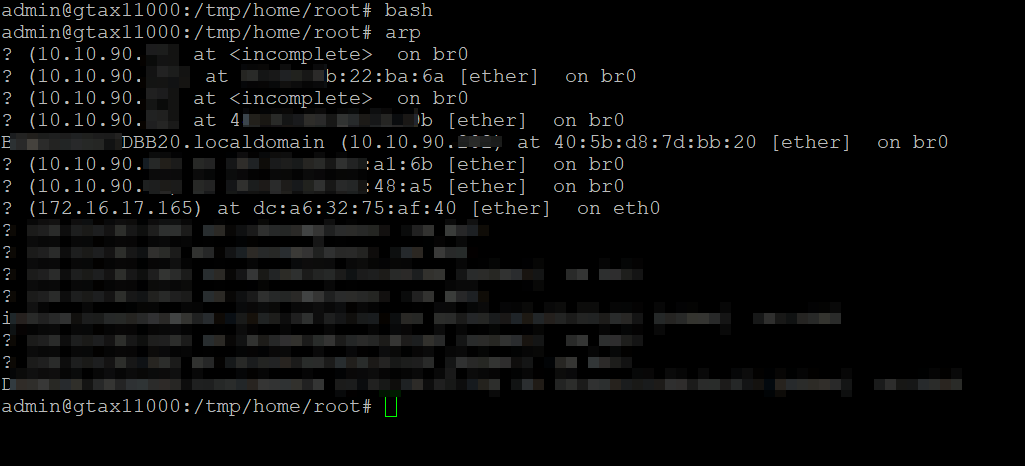
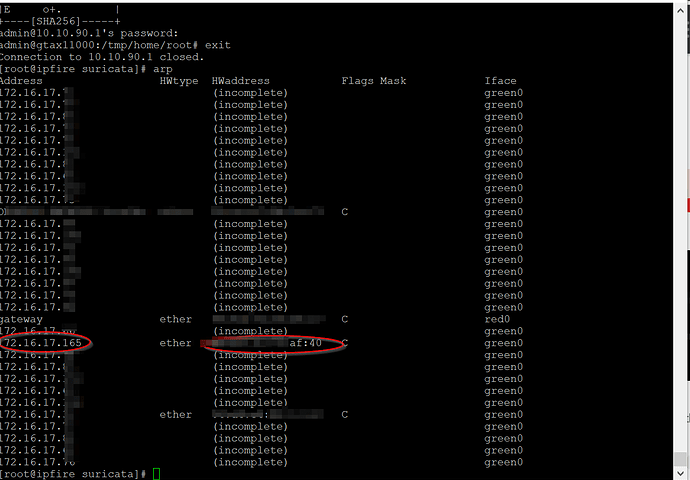
Now to address that piece. I run tcpdump -XXnni any on the IPFire SSH and I can see inbound traffic heading to the PiHole. I then jump to SSH on PiHole at 172.x.x.165 and I can see the traffic arriving…however the return traffic never crosses IPFire on the way back across the network segment. I can say I have a ton of traffic crossing that segment successfully, but apparently I am missing something basic here. I have been about 8 straight hours with hands on keyboard, ssh, and pondering wth may be going on with this.
The Options in the IPFire firewall can be confusing.
Since my logical network on Wifi is upstream from my switch, I assume something may be getting blocked on its way back to its origin, but I had thought requested traffic from point A to B, if it makes it, would be stateful on the way back.
I can also say that IPFire, even though logically I am still on the Green Network, I am not fully in Green or my entry upstream wouldn’t be black in the color scheme. Not sure on that one, but thought I would mention it.
As only an example of color scheme, this is what happens when I add my 10.x.x.x network segment in, although technically logical.
Any ideas?
Eric