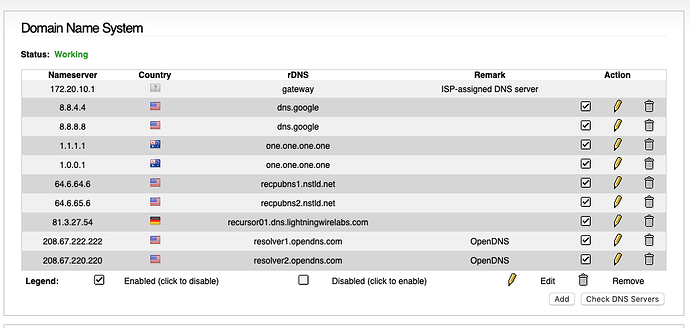
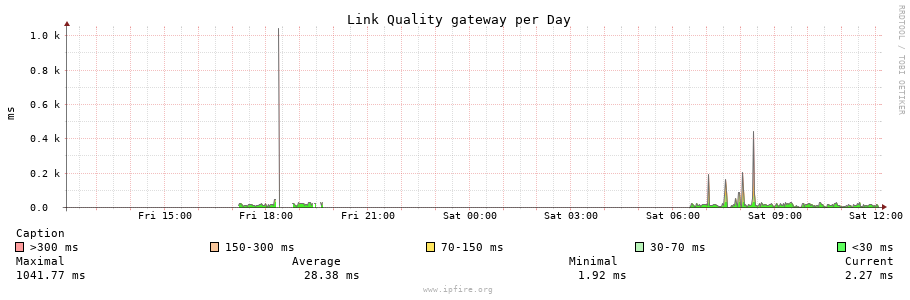
| 11:30:03 |
unbound: [11122:0] |
error: SERVFAIL <trouter-neu-a.cloudapp.net. AAAA IN>: all the configured stub or forward servers failed, at zone . |
| 11:30:01 |
unbound: [11122:0] |
error: SERVFAIL <gateway.fe.apple-dns.net. A IN>: all the configured stub or fo rward servers failed, at zone . |
| 11:29:59 |
unbound: [11122:0] |
error: SERVFAIL <11-courier.push.apple.com. A IN>: all the configured stub or f orward servers failed, at zone . |
| 11:29:58 |
unbound: [11122:0] |
error: SERVFAIL <45-courier.push.apple.com. A IN>: all the configured stub or f orward servers failed, at zone . |
| 11:29:38 |
unbound: [11122:0] |
info: generate keytag query _ta-4a5c-4f66. NULL IN |
| 11:29:36 |
unbound: [11122:0] |
info: start of service (unbound 1.10.1). |
| 11:29:36 |
unbound: [11122:0] |
notice: init module 1: iterator |
| 11:29:36 |
unbound: [11122:0] |
notice: init module 0: validator |
| 11:29:36 |
unbound: [11122:0] |
notice: Restart of unbound 1.10.1. |
| 11:29:36 |
unbound: [11122:0] |
info: 1.000000 2.000000 4 |
| 11:29:36 |
unbound: [11122:0] |
info: 0.524288 1.000000 7 |
| 11:29:36 |
unbound: [11122:0] |
info: 0.262144 0.524288 14 |
| 11:29:36 |
unbound: [11122:0] |
info: 0.131072 0.262144 3 |
| 11:29:36 |
unbound: [11122:0] |
info: 0.065536 0.131072 1 |
| 11:29:36 |
unbound: [11122:0] |
info: 0.000000 0.000001 5 |
| 11:29:36 |
unbound: [11122:0] |
info: lower(secs) upper(secs) recursions |
| 11:29:36 |
unbound: [11122:0] |
info: [25%]=0.240299 median[50%]=0.411941 [75%]=0.694185 |
| 11:29:36 |
unbound: [11122:0] |
info: histogram of recursion processing times |
| 11:29:36 |
unbound: [11122:0] |
info: average recursion processing time 0.528054 sec |
| 11:29:36 |
unbound: [11122:0] |
info: server stats for thread 0: requestlist max 12 avg 3.5 exceeded 0 jostled 0 |
| 11:29:36 |
unbound: [11122:0] |
info: server stats for thread 0: 35 queries, 1 answers from cache, 34 recursion s, 0 prefetch, 0 rejected by ip ratelimiting |
| 11:29:36 |
unbound: [11122:0] |
info: service stopped (unbound 1.10.1). |
| 11:29:30 |
unbound: [11122:0] |
error: SERVFAIL <init-p01st.push.apple.com. A IN>: all the configured stub or f orward servers failed, at zone . |
| 11:29:26 |
unbound: [11122:0] |
error: SERVFAIL <browser.pipe.aria.microsoft.com. A IN>: all the configured stu b or forward servers failed, at zone . |
| 11:29:23 |
unbound: [11122:0] |
error: SERVFAIL <mmx-ds.cdn.whatsapp.net. A IN>: all the configured stub or for ward servers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <pagead2.googlesyndication.com. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <ads.yieldmo.com. A IN>: all the configured stub or forward ser vers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
info: validation failure <tpc.googlesyndication.com. A IN>: SERVFAIL no DS for DS googlesyndication.com. while building chain of trust |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <googleads.g.doubleclick.net. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
info: validation failure <play.google.com. A IN>: SERVFAIL no DS for DS google. com. while building chain of trust |
| 11:29:21 |
unbound: [11122:0] |
info: validation failure <www.google.com. A IN>: SERVFAIL no DS for DS google.c om. while building chain of trust |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <hbopenbid.pubmatic.com. A IN>: all the configured stub or forw ard servers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
info: validation failure <dmx.districtm.io. A IN>: SERVFAIL no DS for DS distri ctm.io. while building chain of trust |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <fastlane.rubiconproject.com. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:29:21 |
unbound: [11122:0] |
error: SERVFAIL <bidder.criteo.com. A IN>: all the configured stub or forward s ervers failed, at zone . |
| 11:29:20 |
unbound: [11122:0] |
error: SERVFAIL <securepubads.g.doubleclick.net. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:29:03 |
unbound: [11122:0] |
info: generate keytag query _ta-4a5c-4f66. NULL IN |
| 11:29:02 |
unbound: [11122:0] |
info: start of service (unbound 1.10.1). |
| 11:29:02 |
unbound: [11122:0] |
notice: init module 1: iterator |
| 11:29:02 |
unbound: [11122:0] |
notice: init module 0: validator |
| 11:29:02 |
unbound: [11122:0] |
notice: Restart of unbound 1.10.1. |
| 11:29:02 |
unbound: [11122:0] |
info: 4.000000 8.000000 1 |
| 11:29:02 |
unbound: [11122:0] |
info: 2.000000 4.000000 1 |
| 11:29:02 |
unbound: [11122:0] |
info: 1.000000 2.000000 2 |
| 11:29:02 |
unbound: [11122:0] |
info: 0.524288 1.000000 3 |
| 11:29:02 |
unbound: [11122:0] |
info: 0.262144 0.524288 4 |
| 11:29:02 |
unbound: [11122:0] |
info: 0.000000 0.000001 9 |
| 11:29:02 |
unbound: [11122:0] |
info: lower(secs) upper(secs) recursions |
| 11:29:02 |
unbound: [11122:0] |
info: [25%]=5.55556e-07 median[50%]=0.32768 [75%]=0.841429 |
| 11:29:02 |
unbound: [11122:0] |
info: histogram of recursion processing times |
| 11:29:02 |
unbound: [11122:0] |
info: average recursion processing time 0.770515 sec |
| 11:29:02 |
unbound: [11122:0] |
info: server stats for thread 0: requestlist max 5 avg 0.8 exceeded 0 jostled 0 |
| 11:29:02 |
unbound: [11122:0] |
info: server stats for thread 0: 21 queries, 1 answers from cache, 20 recursion s, 0 prefetch, 0 rejected by ip ratelimiting |
| 11:29:02 |
unbound: [11122:0] |
info: service stopped (unbound 1.10.1). |
| 11:28:58 |
unbound: [11122:0] |
error: SERVFAIL <init-p01st.push.apple.com. A IN>: all the configured stub or f orward servers failed, at zone . |
| 11:28:58 |
unbound: [11122:0] |
error: SERVFAIL <mobile.events.data.trafficmanager.net. A IN>: all the configur ed stub or forward servers failed, at zone . |
| 11:28:58 |
unbound: [11122:0] |
error: SERVFAIL <mobile.events.data.trafficmanager.net. AAAA IN>: all the confi gured stub or forward servers failed, at zone . |
| 11:28:56 |
unbound: [11122:0] |
error: SERVFAIL <trouter-neu-a.cloudapp.net. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:28:56 |
unbound: [11122:0] |
error: SERVFAIL <trouter-neu-a.cloudapp.net. AAAA IN>: all the configured stub or forward servers failed, at zone . |
| 11:28:54 |
unbound: [11122:0] |
error: SERVFAIL <ocsp.apple.com. A IN>: all the configured stub or forward serv ers failed, at zone . |
| 11:28:53 |
unbound: [11122:0] |
error: SERVFAIL <time-ios.apple.com. AAAA IN>: all the configured stub or forwa rd servers failed, at zone . |
| 11:28:53 |
unbound: [11122:0] |
error: SERVFAIL <time-ios.apple.com. A IN>: all the configured stub or forward servers failed, at zone . |
| 11:28:53 |
unbound: [11122:0] |
error: SERVFAIL <community.learningequality.org. A IN>: all the configured stub or forward servers failed, at zone . |