I have this log when I enter my password, but I don’t know that the connection is well:
2023-04-10 18:59:32 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). OpenVPN ignores --cipher for cipher negotiations.
2023-04-10 18:59:32 OpenVPN 2.6.2 [git:v2.6.2/3577442530eb7830] Windows-MSVC [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] [DCO] built on Mar 24 2023
2023-04-10 18:59:32 Windows version 10.0 (Windows 10 or greater), amd64 executable
2023-04-10 18:59:32 library versions: OpenSSL 3.0.8 7 Feb 2023, LZO 2.10
2023-04-10 18:59:32 DCO version: v0
2023-04-10 18:59:32 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
2023-04-10 18:59:32 Need hold release from management interface, waiting...
2023-04-10 18:59:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:62950
2023-04-10 18:59:33 MANAGEMENT: CMD 'hold off'
2023-04-10 18:59:33 MANAGEMENT: CMD 'hold release'
2023-04-10 18:59:39 MANAGEMENT: CMD 'password [...]'
2023-04-10 18:59:39 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.0.107:1194
2023-04-10 18:59:39 ovpn-dco device [OpenVPN Data Channel Offload] opened
2023-04-10 18:59:39 UDP link local: (not bound)
2023-04-10 18:59:39 UDP link remote: [AF_INET]192.168.0.107:1194
2023-04-10 18:59:39 MANAGEMENT: CMD 'state on'
2023-04-10 18:59:39 MANAGEMENT: CMD 'log on all'
2023-04-10 18:59:39 MANAGEMENT: >STATE:1681174779,AUTH,,,,,,
2023-04-10 18:59:40 TLS: Initial packet from [AF_INET]192.168.0.107:1194, sid=e1b382d3 f44864a1
2023-04-10 18:59:40 VERIFY OK: depth=1, C=CR, ST=San Carlos, L=Costa Rica, O=tec, OU=Pruebas, CN=tec CA, emailAddress=prueba@gmail.com
2023-04-10 18:59:40 VERIFY KU OK
2023-04-10 18:59:40 Validating certificate extended key usage
2023-04-10 18:59:40 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2023-04-10 18:59:40 VERIFY EKU OK
2023-04-10 18:59:40 VERIFY X509NAME OK: C=CR, ST=San Carlos, O=tec, OU=Pruebas, CN=ipfire.localdomain
2023-04-10 18:59:40 VERIFY OK: depth=0, C=CR, ST=San Carlos, O=tec, OU=Pruebas, CN=ipfire.localdomain
2023-04-10 18:59:40 MANAGEMENT: CMD 'echo on all'
2023-04-10 18:59:40 MANAGEMENT: CMD 'bytecount 5'
2023-04-10 18:59:40 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA256
2023-04-10 18:59:40 [ipfire.localdomain] Peer Connection Initiated with [AF_INET]192.168.0.107:1194
2023-04-10 18:59:40 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
2023-04-10 18:59:40 TLS: tls_multi_process: initial untrusted session promoted to trusted
2023-04-10 18:59:40 MANAGEMENT: CMD 'state'
2023-04-10 18:59:41 MANAGEMENT: >STATE:1681174781,GET_CONFIG,,,,,,
2023-04-10 18:59:41 SENT CONTROL [ipfire.localdomain]: 'PUSH_REQUEST' (status=1)
2023-04-10 18:59:41 PUSH: Received control message: 'PUSH_REPLY,route 10.100.189.1,topology net30,route 192.168.1.0 255.255.255.0,ifconfig 10.100.189.6 10.100.189.5,peer-id 0,cipher AES-256-CBC'
2023-04-10 18:59:41 OPTIONS IMPORT: --ifconfig/up options modified
2023-04-10 18:59:41 OPTIONS IMPORT: route options modified
2023-04-10 18:59:41 interactive service msg_channel=872
2023-04-10 18:59:41 MANAGEMENT: >STATE:1681174781,ASSIGN_IP,,10.100.189.6,,,,
2023-04-10 18:59:41 INET address service: add 10.100.189.6/30
2023-04-10 18:59:41 IPv4 MTU set to 1400 on interface 63 using service
2023-04-10 18:59:41 MANAGEMENT: >STATE:1681174781,ADD_ROUTES,,,,,,
2023-04-10 18:59:41 C:\Windows\system32\route.exe ADD 10.100.189.1 MASK 255.255.255.255 10.100.189.5 METRIC 200
2023-04-10 18:59:41 Route addition via service succeeded
2023-04-10 18:59:41 C:\Windows\system32\route.exe ADD 192.168.1.0 MASK 255.255.255.0 10.100.189.5 METRIC 200
2023-04-10 18:59:41 Route addition via service succeeded
2023-04-10 18:59:41 Error: negotiated cipher not allowed - AES-256-CBC not in AES-256-GCM:AES-128-GCM
2023-04-10 18:59:41 OPTIONS ERROR: failed to import crypto options
2023-04-10 18:59:41 Failed to open tun/tap interface
2023-04-10 18:59:41 C:\Windows\system32\route.exe DELETE 10.100.189.1 MASK 255.255.255.255 10.100.189.5
2023-04-10 18:59:41 Route deletion via service succeeded
2023-04-10 18:59:41 C:\Windows\system32\route.exe DELETE 192.168.1.0 MASK 255.255.255.0 10.100.189.5
2023-04-10 18:59:41 Route deletion via service succeeded
2023-04-10 18:59:41 Closing DCO interface
2023-04-10 18:59:41 IPv4 dns servers deleted using service
2023-04-10 18:59:41 INET address service: remove 10.100.189.6/30
2023-04-10 18:59:41 SIGUSR1[soft,process-push-msg-failed] received, process restarting
2023-04-10 18:59:41 MANAGEMENT: >STATE:1681174781,RECONNECTING,process-push-msg-failed,,,,,
2023-04-10 18:59:41 Restart pause, 1 second(s)
2023-04-10 18:59:59 MANAGEMENT: Client disconnected
2023-04-10 18:59:59 ERROR: could not read Private Key username/password/ok/string from management interface
2023-04-10 18:59:59 Exiting due to fatal error
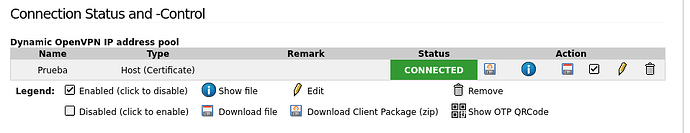
In the IPFire i have this status:
But how can I test so that a user can connect to the network through that service and it appears that it is a computer within the internal IPFIRE network.