Hello everyone,
I am currently trying to figure out how to implement Routing with multiple IPSec Gateways.
I am struggling with the implementation, as I already tried a few things with limited success.
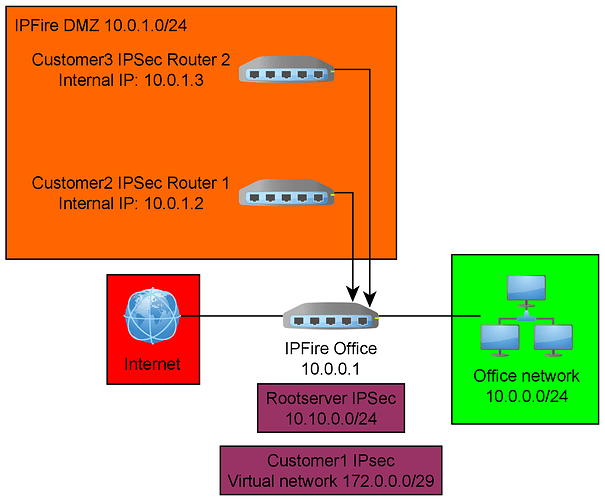
First of all, here is an image on how things should look like
Now, here are my questions:
First of all, is a constellation like the picture even possible? Can I add multiple distinctive IPSec routers behind a single IPFire, while IPFire itself is also handling IPSec tunnels? We need to do this, because some of our customers want to use their preconfigured hardware to establish IPSec tunnels.
I am thinking about a CUSTOMPREROUTING and CUSTOMPOSTROUTING rule in firewall.local to redirect traffic from Customer2 and Customer3 to the corresponding IPSec router.
I tried this already in a test case, but it didn’t work.
I tested with:
Firewall rule RED -> Red (firewall) allow all (just to test)
Network RED -> redirect all to ipsec router (just to test)
Image (new users can only post one image…): https://i.imgur.com/cIOW0ae.png
That didn’t work, the router couldn’t establish an ipsec link with a timeout error.
Then I tried adding custom IPTables rules:
iptables -t nat -A CUSTOMPREROUTING -i red0 -s Customer -j DNAT --to IPSec Router
iptables -t nat -A CUSTOMPOSTROUTING -o red0 -d Customer -j SNAT --to IPSec Router
That didn’t work either, the rules didn’t even get a hit when I looked in the iptables tab in the webUI.
So my question is “how can I redirect IPSec traffic from a specific IP addres / customer while IPFire is also handling IPSec itself?”
My second question is, how does IPSec with a virtual network work in IPfire?
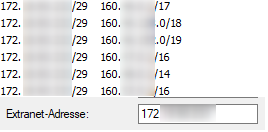
We have one customer, cutomer1 in the first image, who uses a “virtual transfer network” for the IPSec tunnel. IPSec config looks something like this:
Image: https://i.imgur.com/H2zIJsY.png
Note that Local subnet is NOT our 10.0.0.0/24 office network.
“Local subnet” MUST be the “virtual network”, or else the link doesn’t establish. The target IPSec device is a Cisco device.
The link does come up, but IPFire can’t route packets through it, traceroute tells me either “Target network not reachable” or “send not allowed”.
I also tried several things with custom IPTables rules to SNAT the packets to the right IPs, but to no avail.
So here is my second question:
How can I route traffic through an IPSec tunnel if the customer demands a different local subnet in the IPSec tunnel than we physically have in our network?
Thanks for reading, and thanks for potentially helping me out!
Kind regards