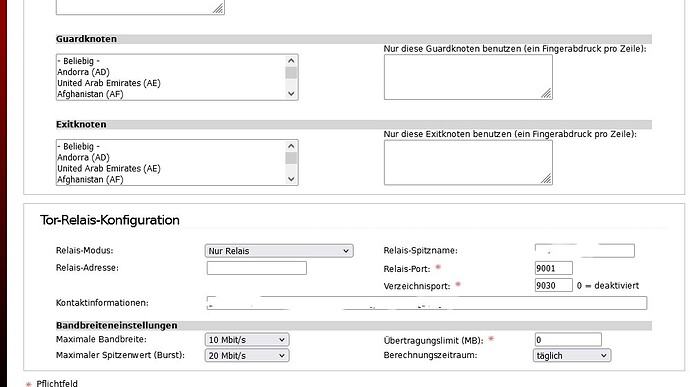
In the Tor Relay configuration, I entered and saved the default port 9030 as the directory port, but it is simply not used or displayed by the https://metrics.torproject.org info page.
Is there anything else I need to do to make this work?
Hi,
this looks fine to me, presuming you ticked the “enable Tor relay” checkbox above as well. ![]()
In /var/log/messages, the following line should be logged if Tor could started the relay procedure properly:
May 1 03:20:38 maverick Tor[5558]: Self-testing indicates your ORPort x.x.x.x:9001 is reachable from the outside. Excellent. Publishing server descriptor.
Thanks, and best regards,
Peter Müller
Yes of course I ticked Relay on Port 9001, since febuary and Proxy on Port 9060 since last week.
Blockquote
May 1 11:49:24 Tor[11640]: We compiled with OpenSSL 101010ef: OpenSSL 1.1.1n 15 Mar 2022 and we are running with OpenSSL 101010ef: 1.1.1n. These two versions should be binary compatible.
May 1 11:49:24 Tor[11640]: Tor 0.4.6.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 1.1.1n, Zlib 1.2.12, Liblzma 5.2.5, Libzstd 1.5.2 and Glibc 2.35 as libc.
May 1 11:49:24 Tor[11640]: Tor can’t help you if you use it wrong! Learn how to be safe at Am I totally anonymous if I use Tor? | Tor Project | Support
May 1 11:49:24 Tor[11640]: Read configuration file “/usr/share/tor/defaults-torrc”.
May 1 11:49:24 Tor[11640]: Read configuration file “/etc/tor/torrc”.
May 1 11:49:24 Tor[11640]: Based on detected system memory, MaxMemInQueues is set to 6267 MB. You can override this by setting MaxMemInQueues by hand.
May 1 11:49:24 Tor[11640]: ControlPort is open, but no authentication method has been configured. This means that any program on your computer can reconfigure your Tor. That’s bad! You should upgrade your Tor controller as soon as possible.
May 1 11:49:24 Tor[11640]: You specified a public address ‘0.0.0.0:9060’ for SocksPort. Other people on the Internet might find your computer and use it as an open proxy. Please don’t allow this unless you have a good reason.
May 1 11:49:24 Tor[11640]: Opening Socks listener on 0.0.0.0:9060
May 1 11:49:24 n Tor[11640]: Opened Socks listener connection (ready) on 0.0.0.0:9060
May 1 11:49:24 Tor[11640]: Opening Control listener on 127.0.0.1:9051
May 1 11:49:24 Tor[11640]: Opened Control listener connection (ready) on 127.0.0.1:9051
May 1 11:49:24 Tor[11640]: Opening OR listener on 0.0.0.0:9001
May 1 11:49:24 Tor[11640]: Opened OR listener connection (ready) on 0.0.0.0:9001
May 1 11:49:24 Tor[11640]: Opening Directory listener on 0.0.0.0:9030
May 1 11:49:24 Tor[11640]: Opened Directory listener connection (ready) on 0.0.0.0:9030
May 1 11:49:24 Tor[11640]: Parsing GEOIP IPv4 file /usr/share/tor/geoip.
May 1 11:49:24 Tor[11640]: Parsing GEOIP IPv6 file /usr/share/tor/geoip6.
May 1 11:49:24 Tor[11640]: Configured to measure statistics. Look for the *-stats files that will first be written to the data directory in 24 hours from now.
May 1 11:49:24 Tor[11640]: Your Tor server’s identity key fingerprint is ‘xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx’
May 1 11:49:24 Tor[11640]: Your Tor server’s identity key ed25519 fingerprint is ‘xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx’
May 1 11:49:24 Tor[11640]: Bootstrapped 0% (starting): Starting
May 1 11:49:28 Tor[11640]: Starting with guard context “default”
May 1 11:49:28 Tor[11640]: Bootstrapped 5% (conn): Connecting to a relay
May 1 11:49:29 Tor[11640]: Bootstrapped 10% (conn_done): Connected to a relay
May 1 11:49:29 Tor[11640]: Bootstrapped 14% (handshake): Handshaking with a relay
May 1 11:49:29 Tor[11640]: Bootstrapped 15% (handshake_done): Handshake with a relay done
May 1 11:49:29 Tor[11640]: Bootstrapped 75% (enough_dirinfo): Loaded enough directory info to build circuits
May 1 11:49:29 Tor[11640]: Bootstrapped 90% (ap_handshake_done): Handshake finished with a relay to build circuits
May 1 11:49:29 Tor[11640]: Bootstrapped 95% (circuit_create): Establishing a Tor circuit
May 1 11:49:30 Tor[11640]: Bootstrapped 100% (done): Done
May 1 11:49:30 Tor[11640]: Now checking whether IPv4 ORPort XXX.XXX.XXX.XXX:9001 is reachable… (this may take up to 20 minutes – look for log messages indicating success)
May 1 12:09:28 Tor[11640]: Your server has not managed to confirm reachability for its ORPort(s) at XXX.XXX.XXX.XXX:9001. Relays do not publish descriptors until their ORPort and DirPort are reachable. Please check your firewalls, ports, address, /etc/hosts file, etc.
But this error occurs only since today, after I installed the update to core167 this morning and restarted, before I had over weeks mostly over 4000 connections and the relay ran…only without open DIR:Port:9030!
/etc/hosts file is empty also no firewall rules at all…
and in /var/ipfire/tor/torrc first line is out comment.
Hi,
just a short side notice on that: Unless you run IPFire on an ARM board (where Tor’s sandboxing feature is still broken from upstream), you can enable sandboxing again, since it has been fixed in Core Update 167.
This is weird indeed. Core Update 167 and running a Tor relay works fine for me, and I am not aware of general issues here… ![]()
To the best of my understanding, this is entirely optional, and Tor will work fine as a relay without it. What happens if you (temporarily) disable DirPort again? Do things work fine then?
Thanks, and best regards,
Peter Müller
Sandbox is active again, DIRPORT set to zero
Same behavior, my TOR Relay does not work anymore ![]()
The TOR Proxy works.
Blockquote
May 1 23:22:33 Tor[21531]: Your server has not managed to confirm reachability for its ORPort(s) at XXX.XXX.XXX.XXX:9001. Relays do not publish descriptors until their ORPort and DirPort are reachable. Please check your firewalls, ports, address, /etc/hosts file, etc.
Blockquote
May 2 01:23:29 Tor[5577]: Now checking whether IPv4 ORPort XXX.XX.XXX.XXX:9001 is reachable… (this may take up to 20 minutes – look for log messages indicating success)
May 2 01:24:09 Tor[5577]: Rejecting SOCKS request for anonymous connection to private address [scrubbed].
May 2 01:29:28 Tor[5577]: Self-testing indicates your ORPort XXX.XXX.XXX.XXX:9001 is reachable from the outside. Excellent. Publishing server descriptor.
May 2 01:29:29 Tor[5577]: Performing bandwidth self-test…done.
May 2 01:32:51 Tor[5577]: Rejecting SOCKS request for anonymous connection to private address [scrubbed]. [74 similar message(s) suppressed in last 540 seconds]
May 2 01:38:29 Tor[5577]: Rejecting SOCKS request for anonymous connection to private address [scrubbed]. [220 similar message(s) suppressed in last 360 seconds]
The TOR relay is running again, but still without DIRPORT.