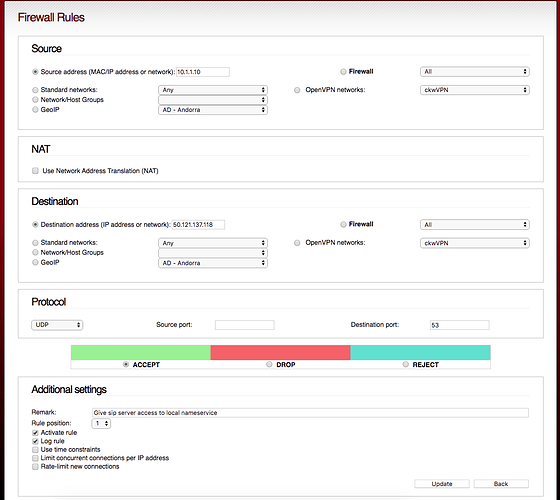
Getting attempted intrusions from some specific ip addresses, some with 10s of thousands of attempts w/ DPT=5060. I’ve attempted to block those specific ip addresses by using the WebUI. I added a rule to DROP all incoming packets from a few of those specified ip address, but the packets continue to be accepted.
Those rules were being added to the filter table, so, from a bash command line I added a rule to the PREROUTING chain in the RAW table and that is successfully dropping the packets.
Michael Tremer suggested I bring up this issue here.
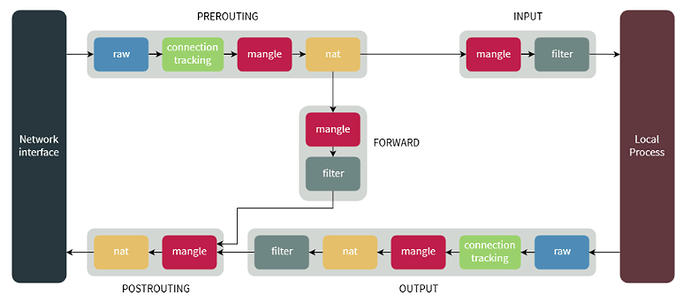
Now, I’m not an iptables guru, but in my research, here is what I’ve discovered. In order to determine why the rule I created in the WebUI (to DROP all packets coming from those specific IP address) wasn’t working, I first needed to understand the flow a packet takes through the iptables tables, chains, and targets. Reading through several iptables tutorials I gained an understanding of that flow. I found a reasonable flowchart which I found instructive:
From the command line, the command “iptables -t raw -L -v --line-numbers” we get the following:
The first chain listed in the output is the PREROUTING chain, which only has one entry with the target CONNTRACK. Now, if I’m reading this information correctly, all packets are sent to the CONNTRACK chain. (If I am wrong on this presumption, please let me know as the rest of this post relies on this presumption).
Now, looking at the first two rules in the CONNTRACK chain:
Again, if I am interpreting this correctly, then this accepts all SIP connections (incoming and outgoing). Presuming this is correct, then this is occurring in the packet flow well before we get to the INPUT chain of the filter table.
This would, to me at least, explain why the rule created by the WebUI is ineffective, while entering the iptables rule at the command line into the PREROUTING chain of the RAW table is effective.
After manually entering, at the command line, the iptables rules to DROP the packets from the attacking IP addresses into the PREROUTING chain of the RAW table, the PREROUTING chain then looks like this:
which actually DROPs all the packets from the subject IP addresses.
OK, this post is way more long winded that I had anticipated, however, could someone more knowledge about iptables please respond to my understanding here. And, if I am correct, what can be done in the WebUI to address this issue?
Also, this is my first post, so I hope it is formatted well enough.
Thank you,
Clark