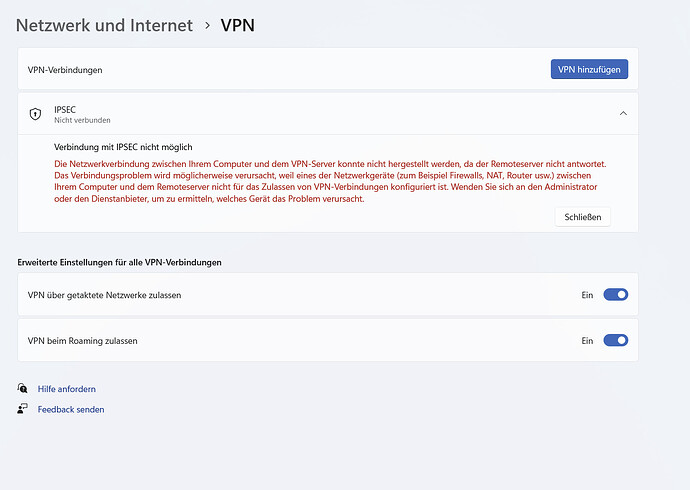
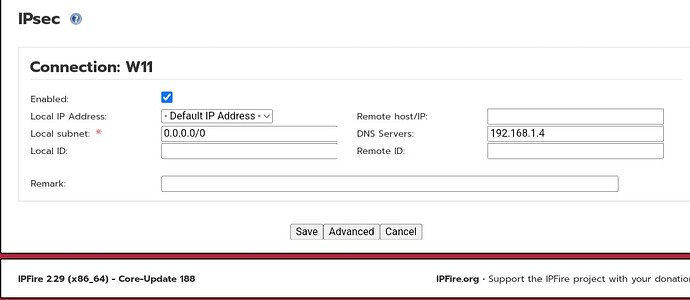
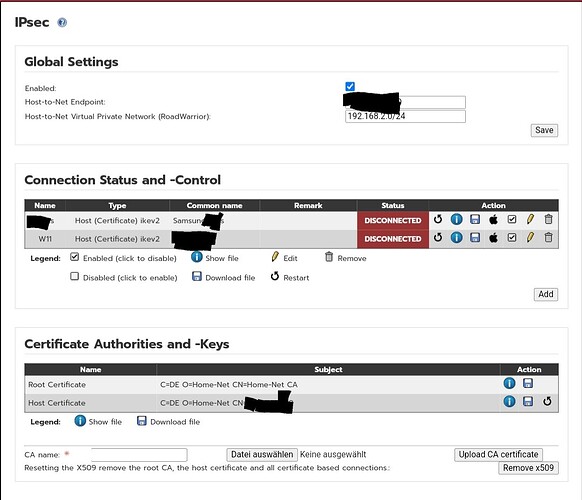
I have activated IPSec server. I was able to set up an android client and it also works. But it does not work on the Windows 11 and Linux client. I have tried several methods PSK, certificate. But it does not work. I have already read the blog (www.ipfire.org - Microsoft Windows) and implemented it. My suspicion is that it is due to IPfire, but I can’t explain exactly where. Can a VPN/IPSec specialist help me? Thanks in advance.
I have added the logs.
Hi,
that looks like the IPsec configuration settings between your Windows/Linux clients and your IPFire machine differ, e. g., the former expect to receive a virtual IP assignment from IPFire (which is common for IPsec roadwarriors), but do not actually receive anything - potentially due to the IPsec configuration not configured accordingly in your IPFire machine.
In order to be able to help you, please post a screenshot of both the IPsec configuration settings in your client and IPFire system.
Thanks, and best regards,
Peter Müller
Hi,
thanks for your reply.
It is a bit confusing to distinguish between the different clients, and which IPsec configuration works (is it only the Android one?), and which doesn’t. ![]()
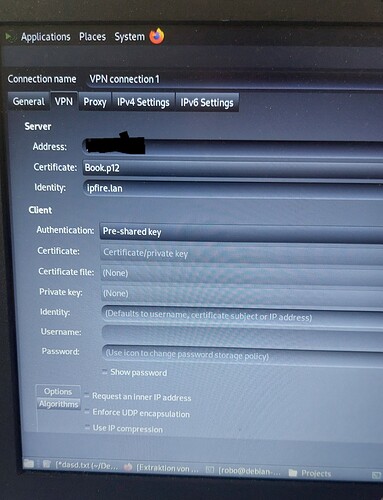
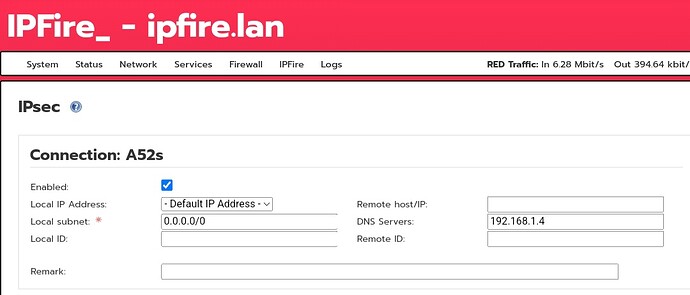
What sticks out to me though is the mismatch between the IPsec server ID ipfire.lan shown in the NetworkManager screenshot, and the “local ID” being left empty in the IPFire configuration screenshot you posted. Please ensure local and remote IDs always align properly on IPsec server and client; see here for additional information on this topic.
As a suggestion, start with PSK-only IPsec connections. The problem does not appear to be (always?) related to the IPsec authentication, it seems to be the IPsec configuration part that takes place after successful authentication (“traffic selectors … unacceptable” is a strong indicator of this).
Thanks, and best regards,
Peter Müller
Hi Peter,
thanks for the quick reply.
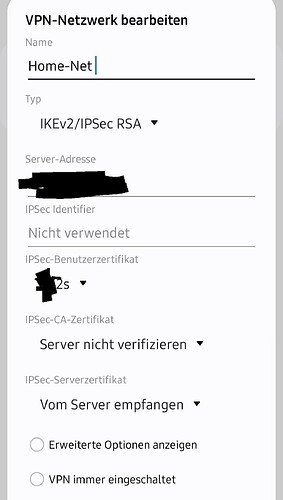
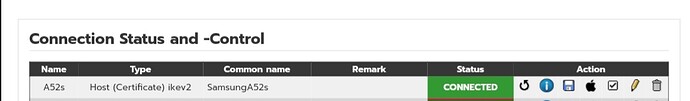
sorry I had forgotten to upload from Android client. This is the current config from the Android client and from the ipfire config.
Hi,
thank you for your reply.
As mentioned earlier, the problem likely isn’t the IPsec authentication, but what happens next. Please increase the logging for that phase (see below for doing so), and provide us with the IPsec logs that are written while attempting to establish IPsec connections from your Linux and Windows clients.
ipsec stroke loglevel cfg 5
Thanks, and best regards,
Peter Müller
Hi Peter,
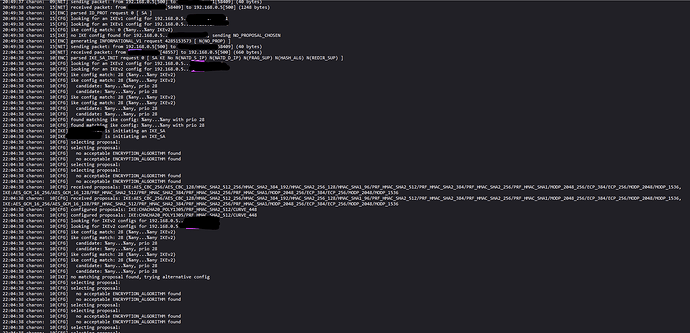
I have now set it up with the (ipsec stroke loglevel cfg 5) and, as you suggested, only tried to establish a connection via PSK. Here is the log.
Hi,
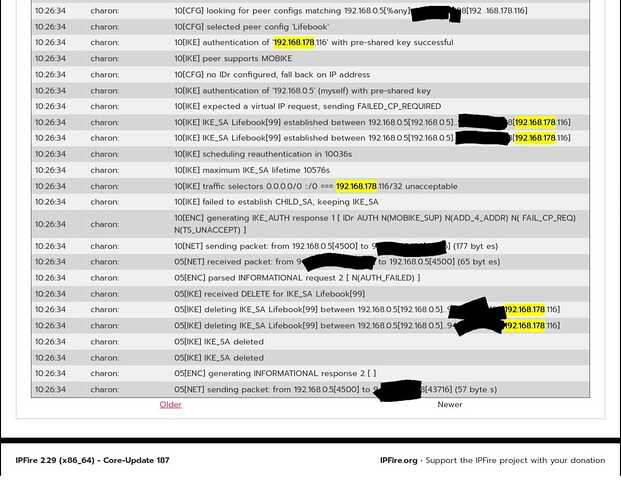
no acceptable ENCRYPTION_ALGORITHM found
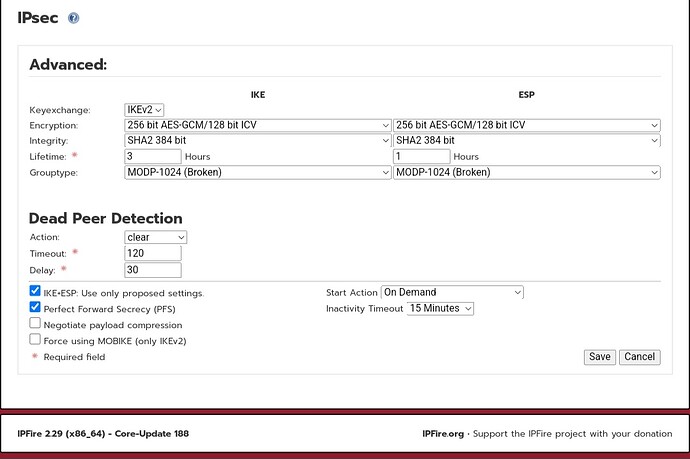
is the culprit: The remote IPsec client does not support the cipher/MAC/key exchange combination your IPFire has configured for this connection (which is CHACHA20_POLY1305/PRF_HMAC_SHA2_512/CURVE_448).
Please change the connection settings on your IPFire machine to allow for a cipher combination supported by the IPsec client, and try again.
(While the logs appear to be somewhat mangled, it looks like the IPsec only supports MODP_1024, which is considered broken. Phasing out that device or IPsec application with some that supports modern cryptography is therefore recommended.)
Thanks, and best regards,
Peter Müller
P.S.: Blacking out public IP addresses did not appear to have worked properly. ![]()
Hi,
well, this should not happen.
Is your IPFire installation fine in terms of the disk and filesystem being healthy, and all updates properly and completely installed? If you can share your Fireinfo profile here, that would be helpful to assess what the situation looks like from a hardware perspective, and to rule out a major problem there.
Is there any error message logged to /var/log/httpd/error_log when trying to create that certificate?
Thanks, and best regards,
Peter Müller
Hi,
As you described above, I have now excluded certain algorithms and created a new certificate. but still no success.
Hi,
as you can see, the
no acceptable ENCRYPTION_ALGORITHM found
error is still there: Your IPsec client (still) does not support the ciphers your IPFire installations mandates it to use.
Thanks, and best regards,
Peter Müller
Hi Peter,
thanks for the quick reply.
How can I set this in Windows 11 Client, for example?
Hi,
unfortunately, I have no experience with IPsec on Windows, as I am not using Windows. It rather interesting, however, to see the apparent lack of modern cipher support in Windows 11… ![]()
You could allow MODP-2048 on your IPFire for this particular IPsec connection, which is supported by the Windows 11 device, according to the log output you posted.
Thanks, and best regards,
Peter Müller
![]() Perhaps the strongSwan documentation would be helpful?
Perhaps the strongSwan documentation would be helpful?
https://docs.strongswan.org/docs/5.9/interop/windowsClients.html
Regards
Hi Peter,
strangely enough, I had the same problems with Debian 12 client.