Hi there,
we just set up a net-to-net VPN with IPSec between our two offices.
On the one side we have a connection with 300Mbit/300Mbit and on the other side we have a connection with VDSL250.
The general connection between the two sites works fine but the network speed for all operations (copying, storage etc.) is only 4-5 Mb/s.
I have already done some tests with iperf but only reach a maximum speed of 4-5Mb/s between the two ipfire servers.
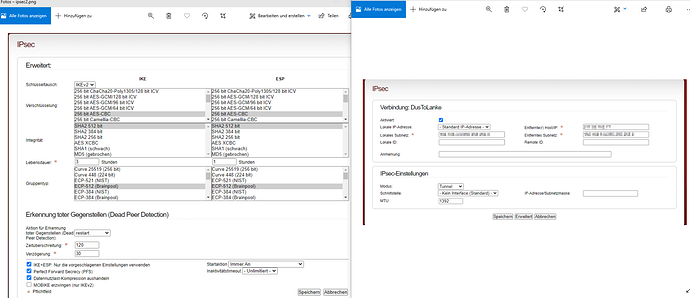
You can find a screenshot from our IPsec configuration in the attachement area.
Would be nice to get some tips/help to boost the speed here.
Thanks!!
Did you verified the CPU load of both firewalls during transfer rates?
Does CPU supports AES-NI instructions?
CPU load on both sides seems to be fine as there is no big load while transferring big files.
Hardware on both sides supports AES-NI.
Any other idea is there something we can change and test with the configuration?
Sorry, more questions…
Did you setup manually the IPSec MTU?
Is there any option for ignore the fragmenting request that’s been enabled?
The data transfer operations that you’re talking about on what protocols rely?
We changed the MTU value manually but it was just a shot in the dark. We wanted to see if something changes but it had no effect.
The fragmenting request is enabled because the best practice guide in the IPFire wiki says so. We will deactivate it and try again.
We just did some simple copy jobs. Behind firewall A is a fileserver so we logged in to a client behind firewall B and started a copyjob of a big iso file from the fileserver behind firewall A. In addition we started multiple iperf tests from client to client and from firewall to firewall. Every copyjob or test gave us a result of 4 to 5 MB/s.
We also tested some downloads from servers outside the network and reached the maximum on both sides (30MB/s and 25MB/s).
More questions or advices? 
Hi,
having a look at your screenshots (thanks for providing them), some configuration items strike my attention:
- Especially on modern hardware, AES-GCM is (sometimes significantly) faster than AES-CBC.
openssl speed [algorithm]should give you a precise idea for the exact difference on your hardware. - Personally, I prefer Curve 25519 for security reasons over the NIST/Brainpool ones, but have no information regarding performance aspects of it at hand.
- Compression is often not worth the CPU time it consumes. Does it make a difference if you turn it off?
Aside from that (the AES-GCM issue is the only one I can imagine to make a noticeable performance difference), I suspect MTU issues as well, but am unfortunately not an expert when it comes to VPN and performance. @ms is, but he is short on spare time those days…
Thanks, and best regards,
Peter Müller
Hi Peter,
thanks for your answer and advices. I changed the following configurations directly:
- AES-CBC to AES-GCM as
openssl speed [algorithm]showed me better rates with AES-GCM. - Brainpool to Curve, even if there is no real benefit proven
- Turn compression of
I did a new iperf3 test and here are the results:
Firewall A to Firewall B: 250 Mbit/sec
Client A to Client B: 30 Mbit/sec
So the result between firewall to firewall seems to be excellent now but the speed between client to client behind the firewalls is not sufficient for me.
Some more Information: The clients in OFFICEA are connected via cable and the clients in OFFICEB are connected via wifi. We checked the wifi nics in OFFICEB and they show us at least 300MBit/s constantly. The firewall in OFFICEA has QoS activated but no defined rule for the IPSec tunnel. This should not be a problem because it should get as much bandwith as possible if not defined, right?
Any other idea why the connection from client to client is not as fast as the connection between the two firewalls? 
Depends on the configuration of your QoS… IPSec is a protocol which should be considered.
Are both connections symmetrical as speed?
I would think that a service which is not defined in QoS settings can get at much bandwith as possible or not?
OfficeA has a 300Mbit symmetrical connection and in OfficeB we have 250Mbit down and 50Mbit up.
Hi,
hm, this sounds like you enabled the IPS on your firewalls. For IPsec, this causes packets generated by clients behind IPFire to be inspected twice (the original packet as it appears on GREEN/BLUE and the encrypted one on RED, although the parser should stop analysing pretty soon).
Personally, I would recommend to set up a QoS rule for IPsec anyway to ensure you won’t run out of bandwidth and such traffic will be prioritised first.
Thanks, and best regards,
Peter Müller
Hi Peter,
thanks for your reply. I just checked to be sure and the IPS is deactivated on both sides so that should not be any problem.
Best regards
Johannes