Thanks for the feedback.
I was a OpenVPN user since years until it failed with some of my colleagues.
Never understood why it failed so badly.
Although 8 users doesn’t look much.
Perhaps the load of more simultaneous users.
The internet was a mess back in Mar/ Apr.
That didn’t help either.
Considering both your comments I might give OpenVPN another try.
Nevertheless, I followed the IPSec Roadwarrior guide step by step.
Step 1 - Global IPSec Settings
Step 2 - Generate certificates
Step 3 - Create the Connection on IPFire
Local Subnet 192.68.0.0/255.255.255.0
Fill in the form to generate the device certificate
“Keyexchange”: Select “IKEv2”
• “Encryption”: Select “256 bit AES-CBC”, “192 bit AES-CBC”, and “128 bit AES-CBC”
• “Integrity”: Select “SHA2 512 bit”, “SHA2 256 bit”, and “SHA1 (Weak)” (NOTE: SHA1 should not be used, but Windows 10 does not support SHA2 by default. Powershell can be used to allow the use of SHA2. When I have a chance I will revisit this article and revise to remove this cipher)
• “Grouptype”: Select “MODP-2048” and “MODP-1024 (Broken)” (NOTE: MODP-1024 should not be used, but Windows 10 does not support strong encryption by default. Powershell can be used to enable better encryption.
The advanced settings aren’t sufficiently documented.
I assumed the settings are the same for both sections IKE and ESP.
Only works without breaking every 45 min. if we enable ESP grouptype -none-.
Lifetime, DPD and other settings aren’t clear for me.
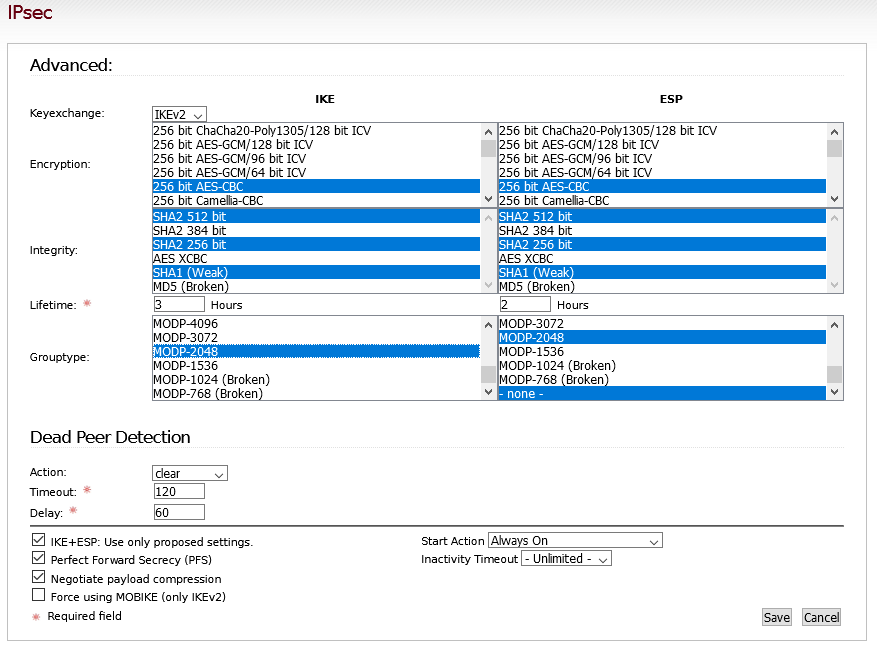
ie. I only managed to get a stable connection with ESP “none” enabled.
Step 5 - Install the certificate on the Windows PC
Step 6 - Create the connection in Windows
In regard to windows 10 I found this instructions but no further details.
AES-256-CBC and MODP2048
By default, the Windows Agile VPN Client only offers AES-128-CBC, AES-192-CBC, AES-256-CBC, 3DES, SHA-1,SHA-256, SHA-384 and MODP-1024.
By creating and setting the following registry key as a DWORD key, support for MODP2048 can be enabled, disabled or enforced.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters\NegotiateDH2048_AES256
The values that can be used are 0, 1 or 2. The table tells you what the values mean.
value
meaning
0 (default)
disable AES-256-CBC and MODP-2048
1
Enable AES-256-CBC and MODP-2048
2
Enforce the usage of AES-256-CBC and MODP-2048
By using the Set-VpnConnectionIPsecConfiguration PowerShell cmdlet it is possible to use even more algorithms like AES-GCM and ECP DH groups (at least on Windows 10). The VPN connection may be added in the GUI or via “Add-VpnConnection” cmdlet.
It’s a pity the person who contributed with the IPSec guide didn’t have time to finish it.
From what I read so far it doesn’t look sufficient to be secure using IPSec.
Thank you

