Adolf,
Correct, all PSK IPSec Roadwarriors can resolve anything anywhere.
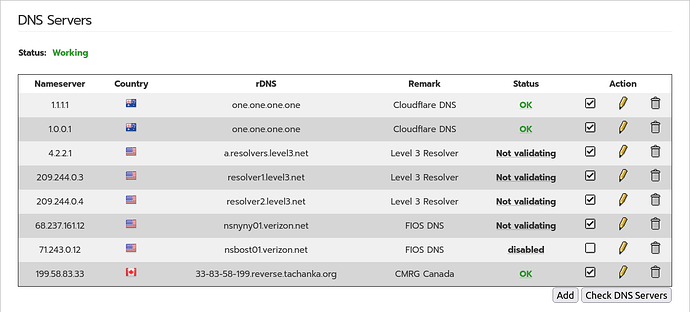
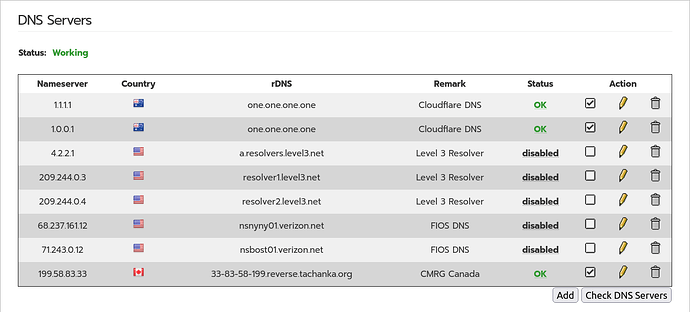
All non validating DNS servers have been disabled, and just tried a certificate based IPSec RW, and still experiences same condition of being unable to resolve ANY address, internal or external.
I am including a full dump of the charon output below of a test connection, resolving address using PSK, and then another one with a cert from start to close (this includes the PSK connection and the Cert connections. Please forgive me if there was a better way to upload this…see below.
Just strange that this would just stop working, considering we made no changes.
Aug 8 17:16:45 ******* charon: 16[NET] received packet: from yyy.yyy.yyy.yyy[49733] to xxx.xxx.xxx.xxx[500] (1096 bytes)
Aug 8 17:16:45 ******* charon: 16[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Aug 8 17:16:45 ******* charon: 16[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:16:45 ******* charon: 16[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:16:45 ******* charon: 16[CFG] selected proposal: IKE:CHACHA20_POLY1305/PRF_HMAC_SHA2_512/CURVE_448
Aug 8 17:16:45 ******* charon: 16[IKE] remote host is behind NAT
Aug 8 17:16:45 ******* charon: 16[IKE] DH group CURVE_25519 unacceptable, requesting CURVE_448
Aug 8 17:16:45 ******* charon: 16[ENC] generating IKE_SA_INIT response 0 [ N(INVAL_KE) ]
Aug 8 17:16:45 ******* charon: 16[NET] sending packet: from xxx.xxx.xxx.xxx[500] to yyy.yyy.yyy.yyy[49733] (38 bytes)
Aug 8 17:16:45 ******* charon: 06[NET] received packet: from yyy.yyy.yyy.yyy[49733] to xxx.xxx.xxx.xxx[500] (1120 bytes)
Aug 8 17:16:45 ******* charon: 06[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Aug 8 17:16:45 ******* charon: 06[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:16:45 ******* charon: 06[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:16:45 ******* charon: 06[CFG] selected proposal: IKE:CHACHA20_POLY1305/PRF_HMAC_SHA2_512/CURVE_448
Aug 8 17:16:45 ******* charon: 06[IKE] remote host is behind NAT
Aug 8 17:16:45 ******* charon: 06[IKE] sending cert request for "C=US, O=XXXXXX, CN=XXXXXX CA, E=*******@xxxxxxxxx"
Aug 8 17:16:45 ******* charon: 06[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ]
Aug 8 17:16:45 ******* charon: 06[NET] sending packet: from xxx.xxx.xxx.xxx[500] to yyy.yyy.yyy.yyy[49733] (285 bytes)
Aug 8 17:16:45 ******* charon: 07[NET] received packet: from yyy.yyy.yyy.yyy[56437] to xxx.xxx.xxx.xxx[4500] (522 bytes)
Aug 8 17:16:45 ******* charon: 07[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ AUTH CPRQ(ADDR ADDR6 DNS NBNS DNS6) SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
Aug 8 17:16:45 ******* charon: 07[IKE] received cert request for "C=US, O=XXXXXX, CN=XXXXXX CA, E=*******@xxxxxxxxx"
Aug 8 17:16:45 ******* charon: 07[CFG] looking for peer configs matching xxx.xxx.xxx.xxx[%any]...yyy.yyy.yyy.yyy[192.168.64.53]
Aug 8 17:16:45 ******* charon: 07[CFG] selected peer config 'PSKAdm'
Aug 8 17:16:45 ******* charon: 07[IKE] authentication of '192.168.64.53' with pre-shared key successful
Aug 8 17:16:45 ******* charon: 07[IKE] peer supports MOBIKE
Aug 8 17:16:45 ******* charon: 07[CFG] no IDr configured, fall back on IP address
Aug 8 17:16:45 ******* charon: 07[IKE] authentication of 'xxx.xxx.xxx.xxx' (myself) with pre-shared key
Aug 8 17:16:45 ******* charon: 07[IKE] peer requested virtual IP %any
Aug 8 17:16:45 ******* charon: 07[CFG] reassigning offline lease to '192.168.64.53'
Aug 8 17:16:45 ******* charon: 07[IKE] assigning virtual IP 192.168.128.2 to peer '192.168.64.53'
Aug 8 17:16:45 ******* charon: 07[IKE] peer requested virtual IP %any6
Aug 8 17:16:45 ******* charon: 07[IKE] no virtual IP found for %any6 requested by '192.168.64.53'
Aug 8 17:16:45 ******* charon: 07[IKE] IKE_SA PSKAdm[33] established between xxx.xxx.xxx.xxx[xxx.xxx.xxx.xxx]...yyy.yyy.yyy.yyy[192.168.64.53]
Aug 8 17:16:45 ******* charon: 07[IKE] IKE_SA PSKAdm[33] established between xxx.xxx.xxx.xxx[xxx.xxx.xxx.xxx]...yyy.yyy.yyy.yyy[192.168.64.53]
Aug 8 17:16:45 ******* charon: 07[IKE] scheduling reauthentication in 9807s
Aug 8 17:16:45 ******* charon: 07[IKE] maximum IKE_SA lifetime 10347s
Aug 8 17:16:45 ******* charon: 07[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA2_512_256/NO_EXT_SEQ
Aug 8 17:16:45 ******* charon: 07[IKE] CHILD_SA PSKAdm{194} established with SPIs cbe9f078_i c6b7535e_o and TS 0.0.0.0/0 === 192.168.128.2/32
Aug 8 17:16:45 ******* charon: 07[IKE] CHILD_SA PSKAdm{194} established with SPIs cbe9f078_i c6b7535e_o and TS 0.0.0.0/0 === 192.168.128.2/32
Aug 8 17:16:45 ******* charon: 07[ENC] generating IKE_AUTH response 1 [ IDr AUTH CPRP(ADDR DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Aug 8 17:16:45 ******* charon: 07[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[56437] (373 bytes)
Aug 8 17:16:45 ******* charon: 05[NET] received packet: from yyy.yyy.yyy.yyy[56437] to xxx.xxx.xxx.xxx[4500] (81 bytes)
Aug 8 17:16:45 ******* charon: 05[ENC] parsed INFORMATIONAL request 2 [ N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Aug 8 17:16:45 ******* charon: 05[ENC] generating INFORMATIONAL response 2 [ ]
Aug 8 17:16:45 ******* charon: 05[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[56437] (57 bytes)
Aug 8 17:16:55 ******* charon: 14[NET] received packet: from yyy.yyy.yyy.yyy[56437] to xxx.xxx.xxx.xxx[4500] (65 bytes)
Aug 8 17:16:55 ******* charon: 14[ENC] parsed INFORMATIONAL request 3 [ D ]
Aug 8 17:16:55 ******* charon: 14[IKE] received DELETE for IKE_SA PSKAdm[33]
Aug 8 17:16:55 ******* charon: 14[IKE] deleting IKE_SA PSKAdm[33] between xxx.xxx.xxx.xxx[xxx.xxx.xxx.xxx]...yyy.yyy.yyy.yyy[192.168.64.53]
Aug 8 17:16:55 ******* charon: 14[IKE] deleting IKE_SA PSKAdm[33] between xxx.xxx.xxx.xxx[xxx.xxx.xxx.xxx]...yyy.yyy.yyy.yyy[192.168.64.53]
Aug 8 17:16:55 ******* charon: 14[IKE] IKE_SA deleted
Aug 8 17:16:55 ******* charon: 14[IKE] IKE_SA deleted
Aug 8 17:16:55 ******* charon: 14[ENC] generating INFORMATIONAL response 3 [ ]
Aug 8 17:16:55 ******* charon: 14[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[56437] (57 bytes)
Aug 8 17:16:55 ******* charon: 14[CFG] lease 192.168.128.2 by '192.168.64.53' went offline
Aug 8 17:17:07 ******* charon: 05[NET] received packet: from yyy.yyy.yyy.yyy[60176] to xxx.xxx.xxx.xxx[500] (660 bytes)
Aug 8 17:17:07 ******* charon: 05[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Aug 8 17:17:07 ******* charon: 05[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:17:07 ******* charon: 05[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:17:07 ******* charon: 05[CFG] selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/ECP_384
Aug 8 17:17:07 ******* charon: 05[IKE] remote host is behind NAT
Aug 8 17:17:07 ******* charon: 05[IKE] DH group MODP_2048_256 unacceptable, requesting ECP_384
Aug 8 17:17:07 ******* charon: 05[ENC] generating IKE_SA_INIT response 0 [ N(INVAL_KE) ]
Aug 8 17:17:07 ******* charon: 05[NET] sending packet: from xxx.xxx.xxx.xxx[500] to yyy.yyy.yyy.yyy[60176] (38 bytes)
Aug 8 17:17:07 ******* charon: 10[NET] received packet: from yyy.yyy.yyy.yyy[60176] to xxx.xxx.xxx.xxx[500] (500 bytes)
Aug 8 17:17:07 ******* charon: 10[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Aug 8 17:17:07 ******* charon: 10[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:17:07 ******* charon: 10[IKE] yyy.yyy.yyy.yyy is initiating an IKE_SA
Aug 8 17:17:07 ******* charon: 10[CFG] selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_512/ECP_384
Aug 8 17:17:07 ******* charon: 10[IKE] remote host is behind NAT
Aug 8 17:17:07 ******* charon: 10[IKE] sending cert request for "C=US, O=XXXXXX, CN=XXXXXX CA, E=*******@xxxxxxxxx"
Aug 8 17:17:07 ******* charon: 10[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ]
Aug 8 17:17:07 ******* charon: 10[NET] sending packet: from xxx.xxx.xxx.xxx[500] to yyy.yyy.yyy.yyy[60176] (329 bytes)
Aug 8 17:17:07 ******* charon: 13[NET] received packet: from yyy.yyy.yyy.yyy[58154] to xxx.xxx.xxx.xxx[4500] (1248 bytes)
Aug 8 17:17:07 ******* charon: 13[ENC] parsed IKE_AUTH request 1 [ EF(1/3) ]
Aug 8 17:17:07 ******* charon: 13[ENC] received fragment #1 of 3, waiting for complete IKE message
Aug 8 17:17:07 ******* charon: 12[NET] received packet: from yyy.yyy.yyy.yyy[58154] to xxx.xxx.xxx.xxx[4500] (1248 bytes)
Aug 8 17:17:07 ******* charon: 12[ENC] parsed IKE_AUTH request 1 [ EF(2/3) ]
Aug 8 17:17:07 ******* charon: 12[ENC] received fragment #2 of 3, waiting for complete IKE message
Aug 8 17:17:07 ******* charon: 09[NET] received packet: from yyy.yyy.yyy.yyy[58154] to xxx.xxx.xxx.xxx[4500] (235 bytes)
Aug 8 17:17:07 ******* charon: 09[ENC] parsed IKE_AUTH request 1 [ EF(3/3) ]
Aug 8 17:17:07 ******* charon: 09[ENC] received fragment #3 of 3, reassembled fragmented IKE message (2605 bytes)
Aug 8 17:17:07 ******* charon: 09[ENC] parsed IKE_AUTH request 1 [ IDi CERT CERTREQ AUTH CPRQ(ADDR DNS) SA TSi TSr N(MOBIKE_SUP) N(ADD_6_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
Aug 8 17:17:07 ******* charon: 09[IKE] received cert request for "C=US, O=XXXXXX, CN=XXXXXX CA, E=*******@xxxxxxxxx"
Aug 8 17:17:07 ******* charon: 09[IKE] received end entity cert "C=US, O=XXXXXX, CN=Palladium"
Aug 8 17:17:07 ******* charon: 09[CFG] looking for peer configs matching xxx.xxx.xxx.xxx[%any]...yyy.yyy.yyy.yyy[C=US, O=XXXXXX, CN=Palladium]
Aug 8 17:17:07 ******* charon: 09[CFG] selected peer config 'Palladium'
Aug 8 17:17:07 ******* charon: 09[CFG] using trusted certificate "C=US, O=XXXXXX, CN=Palladium"
Aug 8 17:17:07 ******* charon: 09[CFG] using trusted ca certificate "C=US, O=XXXXXX, CN=XXXXXX CA, E=*******@xxxxxxxxx"
Aug 8 17:17:07 ******* charon: 09[CFG] reached self-signed root ca with a path length of 0
Aug 8 17:17:07 ******* charon: 09[CFG] checking certificate status of "C=US, O=XXXXXX, CN=Palladium"
Aug 8 17:17:07 ******* charon: 09[CFG] certificate status is not available
Aug 8 17:17:07 ******* charon: 09[IKE] authentication of 'C=US, O=XXXXXX, CN=Palladium' with RSA_EMSA_PKCS1_SHA2_384 successful
Aug 8 17:17:07 ******* charon: 09[IKE] peer supports MOBIKE
Aug 8 17:17:07 ******* charon: 09[IKE] authentication of 'C=US, O=XXXXXX, CN=*******.xxxxxxxxx' (myself) with RSA_EMSA_PKCS1_SHA2_384 successful
Aug 8 17:17:07 ******* charon: 09[IKE] sending end entity cert "C=US, O=XXXXXX, CN=*******.xxxxxxxxx"
Aug 8 17:17:07 ******* charon: 09[IKE] peer requested virtual IP %any
Aug 8 17:17:07 ******* charon: 09[CFG] reassigning offline lease to 'C=US, O=XXXXXX, CN=Palladium'
Aug 8 17:17:07 ******* charon: 09[IKE] assigning virtual IP 192.168.128.1 to peer 'C=US, O=XXXXXX, CN=Palladium'
Aug 8 17:17:07 ******* charon: 09[IKE] IKE_SA Palladium[35] established between xxx.xxx.xxx.xxx[C=US, O=XXXXXX, CN=*******.xxxxxxxxx]...yyy.yyy.yyy.yyy[C=US, O=XXXXXX, CN=Palladium]
Aug 8 17:17:07 ******* charon: 09[IKE] IKE_SA Palladium[35] established between xxx.xxx.xxx.xxx[C=US, O=XXXXXX, CN=*******.xxxxxxxxx]...yyy.yyy.yyy.yyy[C=US, O=XXXXXX, CN=Palladium]
Aug 8 17:17:07 ******* charon: 09[IKE] scheduling reauthentication in 42614s
Aug 8 17:17:07 ******* charon: 09[IKE] maximum IKE_SA lifetime 43154s
Aug 8 17:17:07 ******* charon: 09[CFG] selected proposal: ESP:AES_GCM_16_256/NO_EXT_SEQ
Aug 8 17:17:07 ******* charon: 09[IKE] CHILD_SA Palladium{195} established with SPIs ce958887_i ced23074_o and TS 0.0.0.0/0 === 192.168.128.1/32
Aug 8 17:17:07 ******* charon: 09[IKE] CHILD_SA Palladium{195} established with SPIs ce958887_i ced23074_o and TS 0.0.0.0/0 === 192.168.128.1/32
Aug 8 17:17:07 ******* charon: 09[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH CPRP(ADDR DNS DNS) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) ]
Aug 8 17:17:07 ******* charon: 09[ENC] splitting IKE message (2650 bytes) into 3 fragments
Aug 8 17:17:07 ******* charon: 09[ENC] generating IKE_AUTH response 1 [ EF(1/3) ]
Aug 8 17:17:07 ******* charon: 09[ENC] generating IKE_AUTH response 1 [ EF(2/3) ]
Aug 8 17:17:07 ******* charon: 09[ENC] generating IKE_AUTH response 1 [ EF(3/3) ]
Aug 8 17:17:07 ******* charon: 09[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[58154] (1248 bytes)
Aug 8 17:17:07 ******* charon: 09[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[58154] (1248 bytes)
Aug 8 17:17:07 ******* charon: 09[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[58154] (280 bytes)
Aug 8 17:17:08 ******* charon: 14[NET] received packet: from yyy.yyy.yyy.yyy[58154] to xxx.xxx.xxx.xxx[4500] (113 bytes)
Aug 8 17:17:08 ******* charon: 14[ENC] parsed INFORMATIONAL request 2 [ N(NATD_S_IP) N(NATD_D_IP) ]
Aug 8 17:17:08 ******* charon: 14[ENC] generating INFORMATIONAL response 2 [ N(NATD_S_IP) N(NATD_D_IP) ]
Aug 8 17:17:08 ******* charon: 14[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[58154] (113 bytes)
Aug 8 17:17:15 ******* charon: 10[NET] received packet: from yyy.yyy.yyy.yyy[58154] to xxx.xxx.xxx.xxx[4500] (65 bytes)
Aug 8 17:17:15 ******* charon: 10[ENC] parsed INFORMATIONAL request 3 [ D ]
Aug 8 17:17:15 ******* charon: 10[IKE] received DELETE for IKE_SA Palladium[35]
Aug 8 17:17:15 ******* charon: 10[IKE] deleting IKE_SA Palladium[35] between xxx.xxx.xxx.xxx[C=US, O=XXXXXX, CN=*******.xxxxxxxxx]...yyy.yyy.yyy.yyy[C=US, O=XXXXXX, CN=Palladium]
Aug 8 17:17:15 ******* charon: 10[IKE] deleting IKE_SA Palladium[35] between xxx.xxx.xxx.xxx[C=US, O=XXXXXX, CN=*******.xxxxxxxxx]...yyy.yyy.yyy.yyy[C=US, O=XXXXXX, CN=Palladium]
Aug 8 17:17:15 ******* charon: 10[IKE] IKE_SA deleted
Aug 8 17:17:15 ******* charon: 10[IKE] IKE_SA deleted
Aug 8 17:17:15 ******* charon: 10[ENC] generating INFORMATIONAL response 3 [ ]
Aug 8 17:17:15 ******* charon: 10[NET] sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[58154] (57 bytes)
Aug 8 17:17:15 ******* charon: 10[CFG] lease 192.168.128.1 by 'C=US, O=XXXXXX, CN=Palladium' went offline