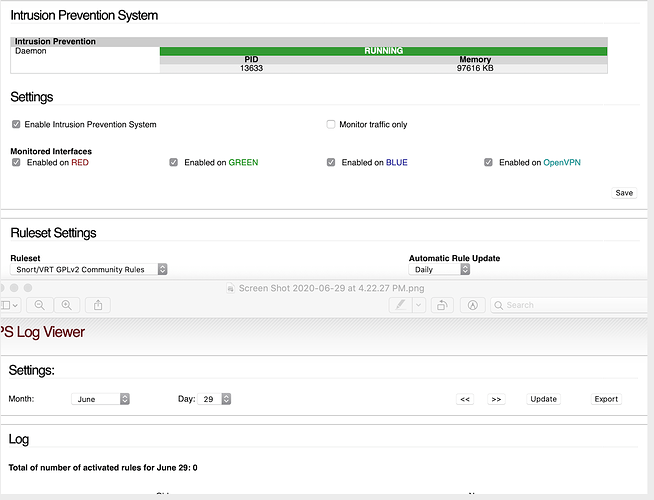
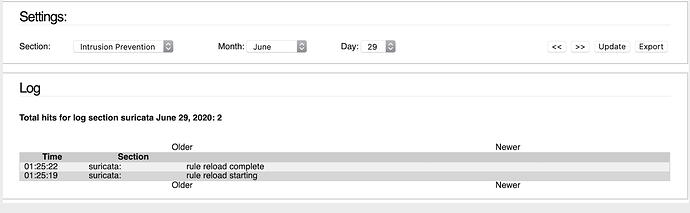
I’ve read the other squawks that appeared relevant. Follows are the IPS enabled and Log screen shots. Have used this ipfire for 30 days (on a ipfire appliance) and not once have the logs reported. Always blank except for 17 errors early on: those were unchecked and the Log has been empty.
Hi,
which IPS rules or rulesets do you have enabled?
Thanks, and best regards,
Peter Müller
The rule set is visible in the images with the post: Snort/VRT GPLv2 Community Rules. I’ve tried other rule sets and have kept this one, as the rules themselves didn’t appear the problem,.
Hi,
oh, I am sorry for not being precise enough. I meant: What IPS rules are activated on your machine? They were cropped off from the screenshot you posted.
If you enabled the attack_response rules, you might try to visit http://testmyids.com/. This site should not load then, and the IPS should log GPL ATTACK_RESPONSE id check returned root.
Thanks, and best regards,
Peter Müller
If you enable Sid 37732 – POLICY-OTHER eicar test string download attempt
and then visit page http://2016.eicar.org/86-0-Intended-use.html
You should get an entry in IPS Log Viewer
NO SUCH FILE
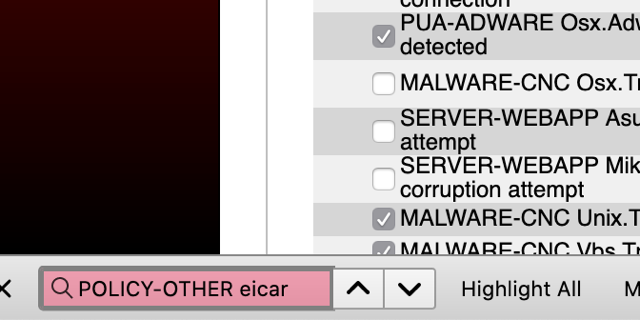
While that file did not load, nor was there a IPS Log note about the block See top line.
However, did enable a few PROTOCOL DNS and received 170 returns. Image follows: That’s too many and not that helpful. Though the problem may be very real. Why is that or more importantly which Protocol or Policy should be enabled or use a different list - home office use?
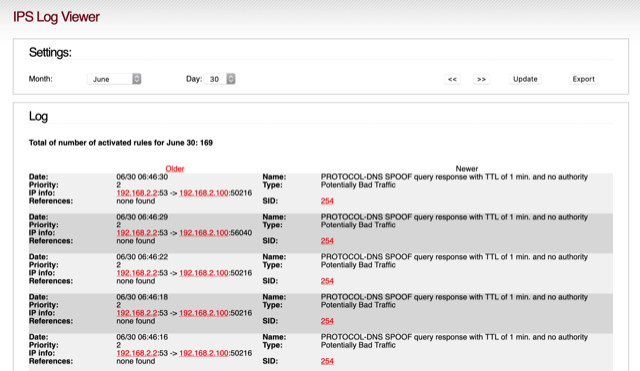
Hi,
That’s too many and not that helpful.
You probably need something like a monitoring script for the IPS hits. If something indicating C&C communication or active malware in your internal networks shows up, you most possible want to know.
Why is that or more importantly which Protocol or Policy should be enabled or use a different list - home office use?
Please refer to IPS Rule Selection for further information regarding the IPS rule selection.
Thanks, and best regards,
Peter Müller
Suricata rules must be adapted according to the usage environment. You need to check the logs and activate or deactivate rules. For example, scan.rules disturbs some software on my macOS. Disable when using this software and reactive again. Other rules are unnecessary for my environment.
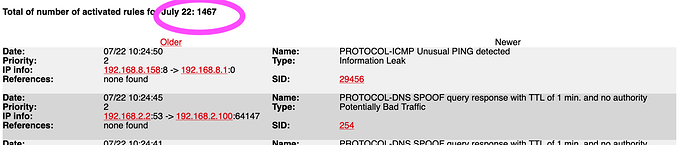
The IPS Log reports thousands of unusual Pings and Information Leakage every day. Does that mean those actions are being blocked by Suricata or just reported to have happened?
One way for you to check is by interrupting the service. If it’s working, it’s just an alert. Suricata is always necessary to keep an eye on the logs and control false positives.
Hi,
Does that mean those actions are being blocked by Suricata or just reported to have happened?
have you checked “monitor traffic only”? If so, those events will be logged only, otherwise, they will be dropped too.
The IPS Log reports thousands of unusual Pings and Information Leakage every day.
If your IPFire machine is exposed to the internet directly, this is quite normal. If not, please read the corresponding documentation on IPS rule selection and enable only those which make sense in your environment.
Thanks, and best regards,
Peter Müller