Hi everone!
I am new to IPfire. Used to run IPcop starting already with a 0.x version back then. Switched to pfSense for several years now and want to give IPfire a try.
Installation and general config including server in DMZ, DHCP, DNS etc are really simple and all worked like a charm (HW: PC engines APU2).
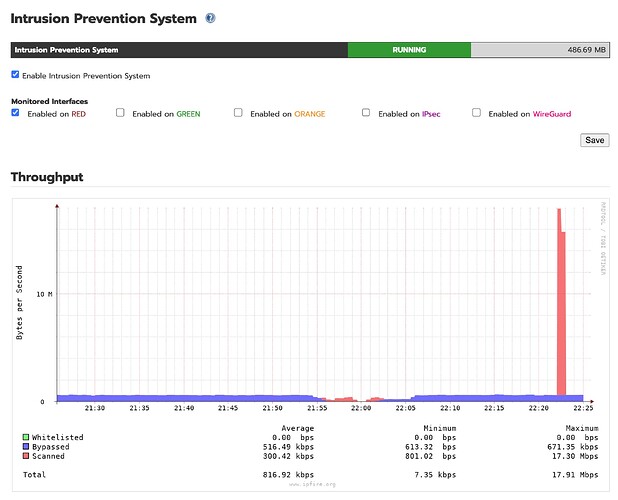
As I used to run Snort on the pfSense previously I have now set up IPS and here it says the intrusion detection is implemented using Suricata.
But apart from the possibility to select individual rules from the list via the “Customize Ruleset”-button I cant find anything to define how the IDS should behave.
On the Suricata website are details on the rules and i.e. what actions are taken (i.e. drop, reject). However, I cant find anything alike on IPfire so far.
More precisely, I would like to configure the IDS such that a rule match leads to the “offending IP” being blocked (=dropped) entirely for 1 hour, and I also like to have list of the currently blocked IPs (with some details, i.e. which rule matched). Currently, I just don’t know what exactly the system does when a match occurs, nor how I could configure the behaviour in more detail.
I know IPfire aims at “simple use”, which is obviously very different with pfSense which does offer ‘too many options’ sometimes, but it would be nice to know how/where I could customize IPfire a little bit more (perhaps I am just missing some hidden expert button/page).
Edit: Even customization on the command line (i.e. using root via SSH) would be fine, given proper documentation),.
Thanks in advance.